Attackers Don’t Need Exploits When Everything Is Already Public
The most common attack on the web today doesn’t require advanced hacking skills—it just requires knowing where to look.
Instead of breaking into systems with complex exploits, attackers are simply finding ones that were never properly secured in the first place.
Many companies and device manufacturers leave important systems exposed to the internet with little to no protection. Apartment intercoms, industrial control panels, security cameras, medical devices, and corporate admin portals are often online with default passwords, weak authentication, or no safeguards at all.
It’s not hacking in the traditional sense—it’s searching. Tools like Google, Shodan, and ZoomEye index these exposed systems, making them easy to find. The only thing preventing unauthorized access is whether the default password has been changed—and too often, it hasn’t.
This problem is known as broken access control—a failure to properly restrict who can access what. When these systems don’t check permissions correctly, anyone can:
Log into admin panels they shouldn’t have access to
View or modify private data without authorization
Take over user accounts without needing credentials
Access critical systems simply because they were left exposed
This is why this issue has become the biggest security failure on the internet. Attackers aren’t breaking in—they’re walking through open doors, and they’re finding them at scale.
How Easy It Is to Get In
Eric Daigle, a computer science and economics student at the University of British Columbia, demonstrated just how widespread this issue is in his post, Breaking into Dozens of Apartment Buildings in Five Minutes on My Phone.
He didn’t use sophisticated exploits or advanced tools—just a brand name on an apartment entry panel and a few Google searches. That was enough to lead him to an installation guide, which included default admin credentials. A quick search for the login page’s title revealed many other exposed systems using the same defaults.
With nothing more than publicly available information, Daigle was able to uncover:
Resident names linked to apartment numbers
Logs showing when tenants entered and exited the building
Phone numbers of residents
Options to create or disable key fobs
A manual override function to unlock doors
His experiment didn’t stop at a single building. Using tools like ZoomEye and Nuclei, he expanded his research and found 89 vulnerable sites, all open to anyone who knew where to look.
For Educational Use Only: This information is for educational and cybersecurity awareness purposes only to help individuals and businesses understand these risks and secure their systems properly.
A review was conducted to trace the steps taken by Eric, starting from his observation of the access code panel to identifying the vulnerable sites. The results were replicated successfully. The process includes the following steps...
Step 1: Spotting the Device
Eric notices an apartment entry panel with a brand name clearly displayed on it. This small detail is enough to start the process. Many access control systems, intercoms, and security panels include visible branding, model numbers, or company logos—information that can be used to look up documentation online.
From this single observation, he has everything needed to begin searching for potential weaknesses in the system.
Step 2: Searching for the Product
Eric notes the brand name from the panel—"Enterphone by Identiv"—and runs a quick Google search. In the second result, he finds a setup guide for the system.
These kinds of documents are often publicly available because manufacturers provide them for installers and technicians. However, they frequently contain sensitive details, including default credentials, administrative URLs, and configuration instructions—all of which can be misused if the system isn’t properly secured.
Step 3: Viewing the Setup Guide
Eric opens the installation and operational reference guide he found through Google. The document description stated it covered multiple models, including EnterphoneTM MESH 19, EnterphoneTM MESH IQ panels, and EnterphoneTM MESH Kiosks.
Just four pages into the document, he finds a screenshot of the admin login page, titled "FREEDOM Administration Login". Even worse, the default admin username and password were listed directly below the screenshot—making it clear that many of these systems could be accessed if the credentials hadn’t been changed.
Step 5: Searching for Exposed Systems
Eric takes the title of the login page—"FREEDOM Administration Login"—and enters it into Google.
This search pulls up all publicly indexed pages with the same login title, revealing multiple systems running the same software. Since many organizations fail to change default settings, some of these pages were still using the default credentials listed in the setup guide, leaving them completely exposed.
At this stage, it is clear that this isn’t an isolated case—many similar systems were accessible with just a simple Google search.
Step 6: Logging Into Exposed Systems
Eric logged in—and the system was completely unsecured.
Inside the admin panel, he discovers resident names mapped to apartment numbers, entry logs showing when residents arrived and left, phone numbers, controls to create or disable access fobs, and a manual override function to unlock doors.
To see how widespread the issue was, Eric used ZoomEye and Nuclei, identifying 89 exposed sites. ZoomEye is a search engine that scans the internet for connected devices and publicly accessible systems, making it easy to find unprotected infrastructure. Nuclei automates vulnerability scanning, allowing security researchers to quickly detect security weaknesses in web applications and networks.
With these tools, he confirmed that this wasn’t just one vulnerable building—many others were equally exposed.
Finding More Admin Panels with a Simple Pattern
After seeing how Eric found an exposed admin panel, The question arose: How many more vulnerable systems were present? Instead of searching randomly, patterns were sought that could lead to additional vulnerable systems.
The first two numbers of the IP addresses from the Google searches were checked. These numbers, known as IP prefixes, often remain consistent for systems assigned by the same cloud provider, internet provider, or hosting service.
If one admin panel was exposed in a certain range, there was a good chance that others using the same vendor, service, or setup were nearby.
Finding a Pattern in Exposed Admin Panels
By gathering the IP addresses from the exposed admin panels in Eric’s search results, the most common starting numbers were analyzed. The top two most common prefixes identified were:
50.x.x.x
173.x.x.x
Google searches were conducted using these common IP prefixes, incorporating keywords like 'Login' in the page title to find similar login pages.
From that point, the same approach as before was followed:
Find login panels using Google searches.
Look up the vendor’s setup guide.
Check if default credentials were listed in the manual.
This method quickly led to more exposed admin panels, many still using factory-default logins. It proved that this wasn’t just a one-off mistake—it was a system-wide problem, affecting multiple companies, vendors, and industries.
The fact that so many of these systems were running on major cloud providers suggests that this issue is not just a result of individual mistakes—but a failure of how these services are being deployed at scale.
Example #1: Hotel Content Management System – LG Pro:Centric
The first search pulled up an admin panel for LG Pro:Centric, a hotel content management system used to control in-room entertainment, messaging, and digital signage in hospitality environments.
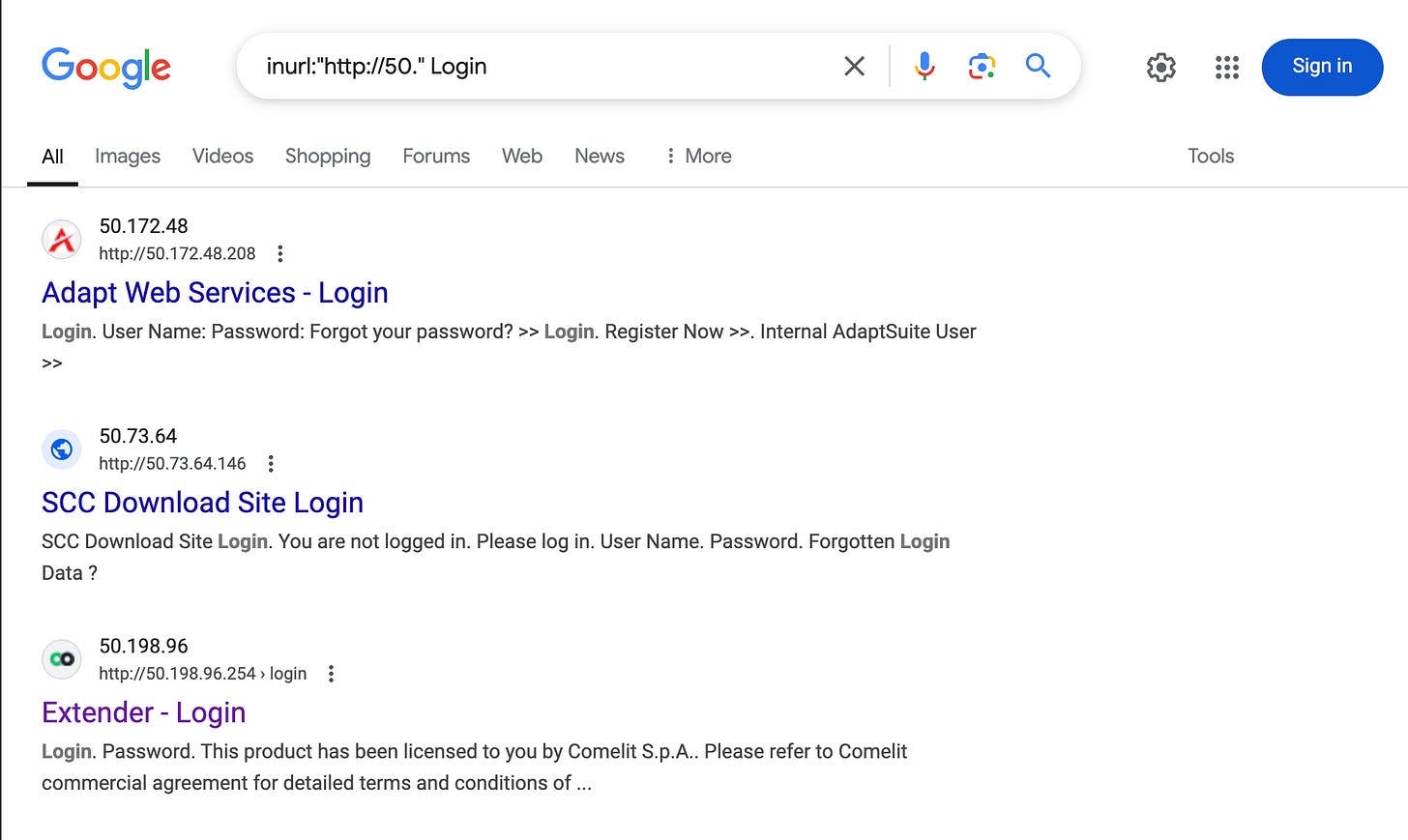
Google Query:
inurl:"http://50." Login
The Google search for "ProCentric default password" revealed the system's default login credentials in publicly available documentation.
The full documentation provides additional details on system configuration, user permissions, and administrative controls, including default login credentials, setup procedures, and remote management features.
Example #2: Building Security System – Comelit Access Control
Another result from the same search as before pulled up an admin panel for a Comelit access control system, a security solution used to manage entry panels, intercoms, and door access for residential buildings, gated communities, and commercial properties.
The Google search for "Comelit default password" revealed the system’s default login credentials in publicly available documentation.
The full documentation provides additional details on system configuration, user access settings, and security management, including default login credentials, setup instructions, and remote access features.
A quick search revealed a site with default credentials, appearing to be a camera system controller for a corporate building. In addition to the system controls, a complete list of staff members responsible for monitoring various aspects of security was available, including some contact information.
Example #3: Emergency Services Routing System for Police, Fire and EMS – Infor EnRoute
Continuing the pattern, the next search focused on 173.x.x.x, another common starting range from earlier results.
Google Query:
inurl:"http://173." Login
This search revealed an admin panel for a page using Infor EnRoute, a computer-aided dispatch (CAD) system used by police, fire departments, and EMS services to route emergency calls and manage response units.
A Google search for "Infor EnRoute Web default admin username" returned publicly available documentation containing setup instructions and default login credentials for the system.
The documentation outlined key details, including how the dispatch system is configured, how automated vehicle location (AVL) works, and how user access is managed, all while listing default login credentials that could still be in use on some systems.
The fact that these portals are publicly accessible in the first place suggests a misconfiguration, making it likely that other security settings—such as password changes—have also been overlooked.
Wrapping Up the Search
Sufficient information was gathered to confirm the pattern and illustrate the widespread nature of the issue."
While the same process could be repeated to uncover even more exposed admin panels, the decision was made not to continue further.
Searching by site titles, branding, or other identifiers on login pages could easily reveal additional instances of the same software; however, given the potential for disrupting sensitive or operationally critical systems, it was decided to cease further investigation.
Lessons Learned
While not every search leads to an exposed system, this method is reliable enough that spending just an hour looking around is likely to reveal multiple admin panels still using default credentials.
If a penetration tester wanted to automate this process, a script could:
Search for login pages with known platform names and panel titles.
Extract common patterns from indexed Google results.
Locate setup guides and documentation that contain default credentials.
Systematically test sites using those default logins.
This issue is not limited to one platform or industry. Many organizations leave admin portals publicly accessible, indexed by search engines, and often secured only by credentials found in a user manual.
The fact that Google alone can uncover so many misconfigured systems shows that default passwords and poor access control remain a massive security failure across industries.
Takeaways for Security Professionals
This research highlights a fundamental issue: many companies are still failing to implement basic security measures. The fact that exposed admin panels, access control systems, and even emergency dispatch platforms can be easily found online suggests a widespread lack of proper configuration and oversight.
If you're responsible for securing systems, take immediate action:
Change default login credentials before deploying any system. Leaving default passwords in place makes it easy for attackers to gain access.
Ensure sensitive systems are not exposed to the public internet. If a system doesn’t need to be accessed remotely, it should be locked down to internal networks only.
Conduct regular audits of your network map to understand what is exposed, how systems are connected, and where security gaps may exist.
Follow security best practices based on Zero Trust principles. This means never automatically trusting any system, device, or user—always verify identity and limit access to the bare minimum required.
With the increasing use of automation and AI-driven attacks, it’s only a matter of time before these vulnerabilities are exploited at scale. Even if access to a system seems minor, the potential for disruption can be serious.
The Risks Go Beyond Just One System
Leaving a system exposed like this is no different than leaving a door wide open to the jungle that is the internet—allowing anything, even predators looking for a kill, to walk right in and start poking around. Attackers don’t need advanced skills to find and access these systems. They simply follow the trail of misconfigurations, searching for vulnerable entry points that were never meant to be public.
While this method doesn’t always grant full control over a system, the fact that it’s misconfigured in the first place can be a red flag that other weaknesses exist. If an admin panel is publicly accessible and still using default credentials, it’s possible the system is also outdated, improperly secured, or running vulnerable services in the background. That opens the door for deeper scanning, allowing attackers to:
Look for unpatched software or exploitable services running on the device.
Test for weak authentication mechanisms beyond the login page.
Map out the internal network to find additional misconfigurations.
A single exposed admin panel might not allow full system takeover, but it can serve as a gateway to bigger security failures. If a security panel controls building access, an attacker could remotely unlock doors. If a dispatch system is exposed, emergency response operations could be disrupted.
This isn’t just a hypothetical risk—it’s a real-world attack vector actively being exploited today. The fact that so many of these systems are publicly exposed and still using default credentials shows that this is a systemic failure across industries, not just an isolated mistake. Fixing these basic security gaps must be a priority before attackers take full advantage of them.
















It’s unrealistic to expect currently deployed systems will be changed anytime soon.
There are some steps that can be implemented:
We can educate manufacturers to update their technology processes to create strong complex passwords at installation admin login.
We could enforce this with legislation placing negligence liability on those manufacturers for not doing so.
What is the probability either of those two remedies will ever see the light of day? Likely zero.
Are we really expecting that the administrators of thousands of systems with default passwords will ever discover their mistakes?