Computer Networking Basics Every Business Owner Must Know for Cybersecurity
Cybersecurity is no longer a concern just for large corporations—small and medium-sized businesses are increasingly becoming targets of digital attacks.
With the rise of artificial intelligence, cybercriminals are utilizing sophisticated methods to breach defenses and steal sensitive information.
Data theft, ransomware attacks, and other threats can lead to severe consequences such as lawsuits, hefty fines, loss of trade secrets and intellectual property, and significant disruptions to your operations.
The reality is clear: all business owners need to understand the fundamentals of networking and cybersecurity. A solid grasp of how data flows within your systems helps you identify vulnerabilities, implement effective controls, and respond to emerging threats with confidence.
This knowledge is not just beneficial; it's essential to safeguard your business from the escalating risks of digital attacks.
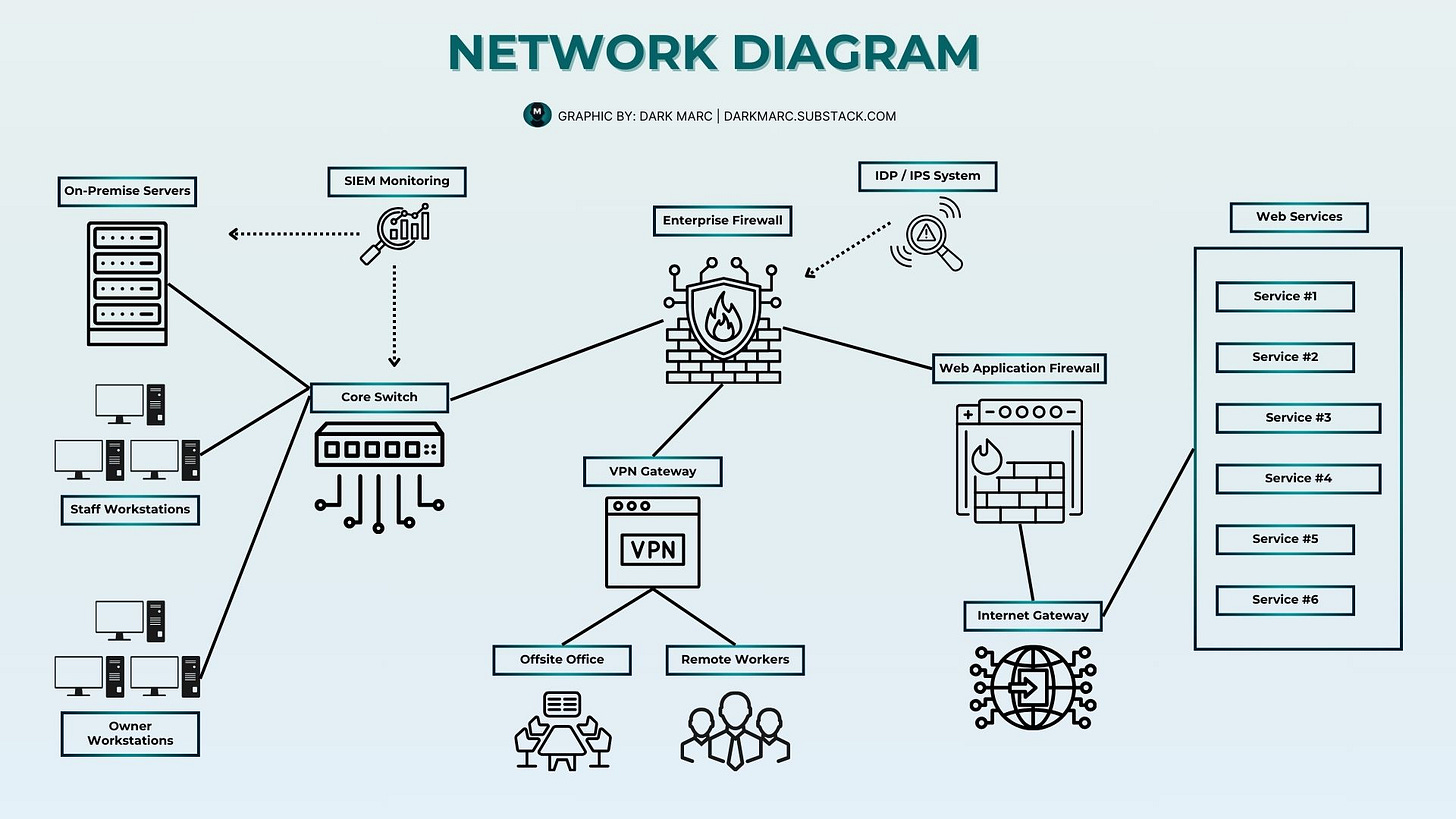
The image above shows a sample implementation of the concepts we'll explore—from basic building blocks like hosts and switches to more advanced security components such as firewalls, VPN gateways, and monitoring systems.
As we examine each networking component in detail, you'll gain insight into not just what these elements do individually, but how they function together to create layers of protection. The enterprise architecture shown provides a real-world example of security principles in action, demonstrating how organizations transform networking theory into effective cybersecurity practices.
Key Networking Components:
Host: A device on a network that can send or receive data, such as a computer or printer.
IP Address: A unique numerical label assigned to each device on a network, serving as its address for communication.
Network: A collection of interconnected devices that can communicate and share resources with each other.
Router: A device that forwards data packets between different networks and directs traffic to the correct IP address.
Switch: A device that connects multiple devices within the same local network, facilitating efficient data communication between them.
Hub: A basic networking device that connects multiple devices, broadcasting incoming data packets to all ports without filtering.
Bridge: A device that connects two or more networks to function as a single network, helping to extend their reach.
Repeater: A device that amplifies and regenerates signals to extend the distance over which data can travel in a network.
Security Components
Alongside foundational computer networking concepts, the network diagram also highlights essential cybersecurity elements, which we will explore in greater detail later. For now, it's important to understand their placement within the overall network structure.
SIEM Monitoring System: Collects and analyzes log data from across the network to detect suspicious activities and security incidents in real-time.
IDP/IPS System: Monitors network traffic to identify and block potential intrusions or attacks before they can compromise network resources.
Enterprise Firewall: Acts as the primary security barrier controlling traffic flow between different network segments based on predefined security rules.
Web Application Firewall: Provides specialized protection specifically for web applications by filtering and monitoring HTTP traffic between web applications and the internet.
VPN Gateway: Enables secure, encrypted connections for remote workers and offsite offices, ensuring sensitive data remains protected when accessed from outside the main network.
Internet Gateway: Serves as the controlled access point between the internal network and external internet resources, providing a security checkpoint for outbound and inbound traffic.
How Do Networks Work?
In the following section, we will explore the fundamental components that make up a network and how they function together to facilitate communication and resource sharing. Understanding these elements is crucial for grasping how data flows within a network.
We will begin with the concept of a Host and continue through key components such as IP Addresses, Networks, Routers, Switches, Hubs, Bridges, and Repeaters.
1. Host
A Host is any device that connects to a network and is capable of sending or receiving data. This includes commonly known devices like computers, laptops, tablets, smartphones, printers, and servers. Each host plays a specific role within the network, whether it's a device that generates data (like a computer) or one that receives data (like a printer).
For example, when you print a document from your laptop, your laptop is the host sending the print request, and the printer is the host receiving that request. Every host has a unique identifier called an IP address that distinguishes it from other devices in the network.
2. IP Address
An IP Address (Internet Protocol Address) is like a postal address for your devices on a network. Just as a home address helps the postal service deliver letters to your home, an IP address allows data to reach your device over the network.
An IP address is typically composed of four numbers separated by periods, such as 192.168.1.10. Each number can range from 0 to 255 and represents binary information that the devices use to communicate. IP addresses can be static (permanently assigned to a device) or dynamic (temporarily assigned by a network each time a device connects).
Think of it as labeling your house in a neighborhood: just like every house has a unique number, every device on a network has a distinct IP address to ensure data gets to the right place.
3. Network
A Network is a system that connects multiple devices together, allowing them to communicate and share resources. You can think of a network as a community where different hosts—such as homes, businesses, or facilities—are connected.
There are different types of networks, such as:
Local Area Network (LAN): This connects devices within a small geographical area, like a home, school, or office.
Wide Area Network (WAN): This covers a larger geographical area and can connect multiple LANs, such as the internet.
Within a network, devices can share files, access the internet, and communicate with each other efficiently. The arrangement and design of the network determine how well devices can interact and share resources.
These foundational concepts provide a solid understanding of the basic building blocks of computer networking.
4. Router
A Router is a crucial device that connects different networks and directs data packets between them. It acts as a traffic manager, determining the best path for data to travel from the source (like your computer) to the destination (like a website server).
For example, when you access a website, your request is sent from your device to the router, which then forwards the request to the correct destination on the internet. The router stores information about various networks, allowing it to make informed decisions about the most efficient routes for data.
Routers often have built-in security features such as firewalls to protect your local network from external threats. They can connect both wired devices, using Ethernet cables, and wireless devices through Wi-Fi, facilitating seamless communication among all connected devices.
5. Switch
A Switch is a networking device that connects multiple devices within the same local network, allowing them to communicate with one another efficiently. Unlike a hub, which indiscriminately sends incoming data to all connected devices, a switch intelligently directs data only to the intended recipient.
For instance, if you send a file from your computer to a printer within the same office network, the switch ensures that the data packet for the printer goes directly to that specific device rather than to every device connected to the network. This efficiency reduces network traffic, speeds up communication, and optimizes overall network performance.
Switches are widely used in home and office environments to create a local area network (LAN) where devices can share resources, access the internet, and communicate with each other.
6. Hub
A Hub is a simpler networking device that also connects multiple devices within a local network, similar to a switch. However, a hub operates without any intelligence; it simply broadcasts incoming data packets to all connected devices without determining their destinations.
Imagine a hub as a loudspeaker in a room: when one person speaks (sends data), everyone can hear them (receive the data) simultaneously. This means that while a hub can connect devices, it does not manage data traffic efficiently. This can lead to network congestion and slower performance, especially as the number of connected devices increases.
Due to its limitations, hubs have mostly been replaced by switches in modern networking, but they are still sometimes used in small or simple setups where advanced features are not necessary.
7. Bridge
A Bridge is a device that connects two or more separate networks, allowing them to function as a single unified network. It helps improve the overall performance and efficiency of data transmission by filtering traffic and reducing collision domains, which occurs when multiple devices attempt to send data simultaneously.
For example, if you have two LANs in different buildings, a bridge can connect these two networks, enabling devices in one building to communicate with devices in the other building seamlessly. The bridge learns the addresses of the devices on either side and only forwards data to the appropriate network, thus minimizing unnecessary traffic and enhancing communication.
Bridges are particularly useful in larger networks where separating traffic can enhance performance and reduce congestion.
8. Repeater
A Repeater is a networking device used to extend the range of a network by amplifying and regenerating signals. When data travels over long distances, the signal can weaken or degrade, making it difficult for devices to communicate effectively.
For instance, in a large building where Wi-Fi signal strength decreases as you move farther away from the router, a repeater can be placed midway to catch the weakened signal, boost it, and pass it on to the devices beyond its range. This ensures that devices located far from the primary source can still maintain a stable and reliable connection.
Repeaters are essential in both wired and wireless networks when distance is a factor, allowing data to travel further without losing quality.
With these eight components—Host, IP Address, Network, Router, Switch, Hub, Bridge, and Repeater—you now have a comprehensive understanding of key elements in computer networking.
Each plays a vital role in ensuring devices can communicate efficiently, share resources, and maintain a functional and secure network environment.
How to Secure Your Enterprise Network
Securing a network is critical for protecting the integrity, confidentiality, and availability of data. Alongside basic networking elements, it's crucial to recognize the role of specialized security components in maintaining a secure environment. Here are key strategies for enhancing network security:
Use Strong Passwords and Authentication
Implementing strong, complex passwords for all devices—including routers, switches, and hosts—is one of the most fundamental measures for securing a network. A strong password should be at least 12 characters long, featuring a mix of uppercase and lowercase letters, numbers, and special symbols. Additionally, incorporating multifactor authentication (MFA) adds an extra layer of security by requiring users to verify their identity through a secondary method, enhancing overall protection.
Network Segmentation
Segmenting a network involves dividing it into smaller, isolated networks (subnets) to restrict access and contain potential threats. For example, separate networks may be created for guest users, employees, and sensitive data servers. By implementing VLANs (Virtual Local Area Networks), organizations can ensure limited access to resources for each group, thereby reducing the attack surface. If one segment is compromised, the threat can be contained without affecting the entire network.
Firewalls and Intrusion Detection Systems (IDS)
Deploying firewalls is essential for monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. Firewalls can be hardware-based, software-based, or a combination.
Utilizing Intrusion Detection Systems (IDS) aids in identifying unauthorized access attempts and potential threats in real time. An IDS monitors network traffic for suspicious activity and alerts administrators for prompt responses to breaches.
Regular Software Updates and Patch Management
Keeping network devices, operating systems, and applications updated is crucial for security. Regular software updates often include patches that fix security vulnerabilities exploited by cybercriminals.
Establishing a routine for checking and applying updates fortifies your network’s devices against known threats. Automating this process can minimize the risk of neglecting important updates.
Use Encryption
Encryption serves to protect sensitive data by converting it into a code that can only be accessed by authorized users with the decryption key. Implementing encryption for data in transit, such as using HTTPS for secure web connections or VPNs (Virtual Private Networks) for remote access, ensures that intercepted data remains unreadable to unauthorized users. Adding encryption for data at rest on servers or storage devices provides another layer of security.
Regular Audits and Monitoring
Performing regular network security audits is essential for organizations to evaluate their security measures' effectiveness. These audits help identify vulnerabilities, compliance gaps, and areas for improvement, ensuring security protocols remain robust.
Utilizing tools such as Security Information and Event Management (SIEM) systems enhances these audits by aggregating and analyzing log data from various network components, providing insights into suspicious activity or potential threats. Continuous monitoring of network traffic and user activities is crucial for detecting unusual behavior or security incidents in real time.
Implementing firewalls alongside Intrusion Detection and Prevention Systems (IDPS) helps establish a defensive perimeter, alerting administrators to anomalies. This proactive approach enables timely responses to mitigate potential threats, reducing the risk of data breaches and bolstering overall network security.
By utilizing traditional security strategies with advanced security components—such as firewalls, SIEM systems, VPN gateways, and internet gateways—organizations can maintain a secure and compliant network environment that effectively safeguards sensitive information.
Securing Your Network is an Ongoing Process
Securing a network is an ongoing process that requires vigilance, proactive measures, and regular assessments.
By implementing strong passwords, segmenting the network, using firewalls and IDS, keeping software updated, utilizing encryption, and conducting regular audits, individuals and organizations can significantly enhance their network security.
These practices not only protect sensitive information but also help maintain trust and confidence in a digital environment. Understanding these security principles is essential for anyone looking to safeguard digital assets effectively.


Great post!