Movie fans searching for the latest releases online may encounter a troubling trend: government (.gov) and educational (.edu) websites linking to illegal downloads. This can compromise cybersecurity and expose users to piracy risks.
These domains, reserved solely for government agencies and accredited schools, require strict authorization to register.
Spam pages, stuffed with keywords to game Google’s search rankings, infiltrate public web directories on these domains.
They feature a fake video player—an image hyperlinked to a malicious site:
https://streamovie[.]xyz/en/movie/1100988/28-years-later?pdf10That website is marked as malicious on VirusTotal, with a 2 score, being flagged as malicious by both Seclookup and CRDF, last analyzed 19 days ago.
While these spam links are a security risk, the greater concern is the potential for more dangerous attacks exploiting the same vulnerabilities, such as phishing, fraud, or distribution of malicious files.
This article explores the risks, guides ethical security researchers on testing these flaws, and provides admins steps to secure affected domains.
Warning: This information is for educational use only. Misuse carries severe legal consequences. Use responsibly to enhance security.
The Issue:
A Google search for “Full Movie” on .gov and .edu domains reveals PDFs linking to illegal streaming sites, hosted on government and educational servers.
Vulnerabilities in CMS platforms like WordPress and Drupal—particularly plugins like Ninja Forms, Gravity Forms, and Drupal’s Webform—allow attackers to upload malicious PDFs to public directories, indexed by search engines and shareable via email or text.
Google search results show varied directory structures across multiple plugins and CMS platforms:
Ninja Forms: https://example.gov/wp-content/uploads/ninja-forms/3/malicious-file.pdf
Gravity Forms: https://example.edu/wp-content/uploads/gravity_forms/folder_name/2025/06/malicious-file.pdf
Drupal Webform: https://example.gov/sites/default/files/webform/form_name_example/_sid_/malicious-file.pdfThe root cause: misconfigured CMS settings and outdated plugins, leaving user-uploaded files in unprotected directories. This enables attackers to spread malicious or illegal content, eroding trust in these authoritative domains.
The Bigger Threat
While the current exploitation involves linking to illegal streaming sites, these vulnerabilities could enable far more dangerous attacks:
Fake Tax Notices: Attackers could upload PDFs posing as IRS notices on .gov domains, demanding immediate payment for alleged tax debts, with links to fraudulent payment portals stealing funds or data.
Forged Agency Letters: Documents with counterfeit government or university logos on .edu or .gov sites could trick users into sharing sensitive information, such as Social Security numbers, under the guise of official correspondence.
Bogus Grant Offers: Fraudulent PDFs on .edu domains could promise fake scholarships or grants, requiring “processing fees” via malicious links to drain victims’ accounts.
Phishing Portals: Attackers could embed links in PDFs redirecting to fake login pages mimicking university or government portals, capturing credentials or financial details.
Malware-Laden Files: Public directories could host PDFs laced with malware, infecting devices of unsuspecting users who download them.
Fake University Acceptance Letters: Hosted on university websites, fraudulent PDFs could be emailed to students, demanding urgent tuition payments to “secure” admission, linking to attackers’ payment sites.
These scenarios highlight the urgent need to address these vulnerabilities to protect public trust and prevent serious harm.
Affected Websites
The following .gov and .edu websites appeared in search results at the time of analysis. Inclusion does not confirm active compromise, but these sites should review their CMS configurations and plugin security:
Government Websites:
Missouri Department of Conservation
Durango Government
National Park Service
Library of Congress
West Linn, Oregon
PubMed Central
Digital.gov
Colorado Trails
Texas Office of Public Utility Counsel
Caddo County, Oklahoma
Supreme Court of New Mexico
DEA Museum
City of Oklahoma City
Alabama Department of Human Resources
National Cancer Institute
Educational Websites:
Liberty University
Syracuse University
Borough of Manhattan Community College
Lakeland Community College
Columbia University
Colorado State University
California State University San Marcos
University of Maryland, Baltimore County
University of California, Berkeley
Rutgers University
University of Utah
Temple University
Northeastern University
University of North Carolina
Citadel Military College
Washington State University
UTHSCSA School of Medicine
Jersey City Public Library
University of Pennsylvania
American Association of University Professors (AAUP)
Replicating the Issue (Drupal Webform)
A test was conducted to verify how vulnerabilities in the Drupal Webform module enable unauthorized file uploads to publicly accessible directories.
The test targeted a Drupal-based website running a vulnerable Webform version and used a public-facing form to ensure ethical and legal compliance, avoiding unauthorized access or harm.
Step 1) Locate a Drupal Webform:
A public-facing Webform was located using a Google search with inurl:files/webform/ to find Drupal sites with exposed Webform directories (e.g., /sites/default/files/webform).
Step 2) Create a Test PDF:
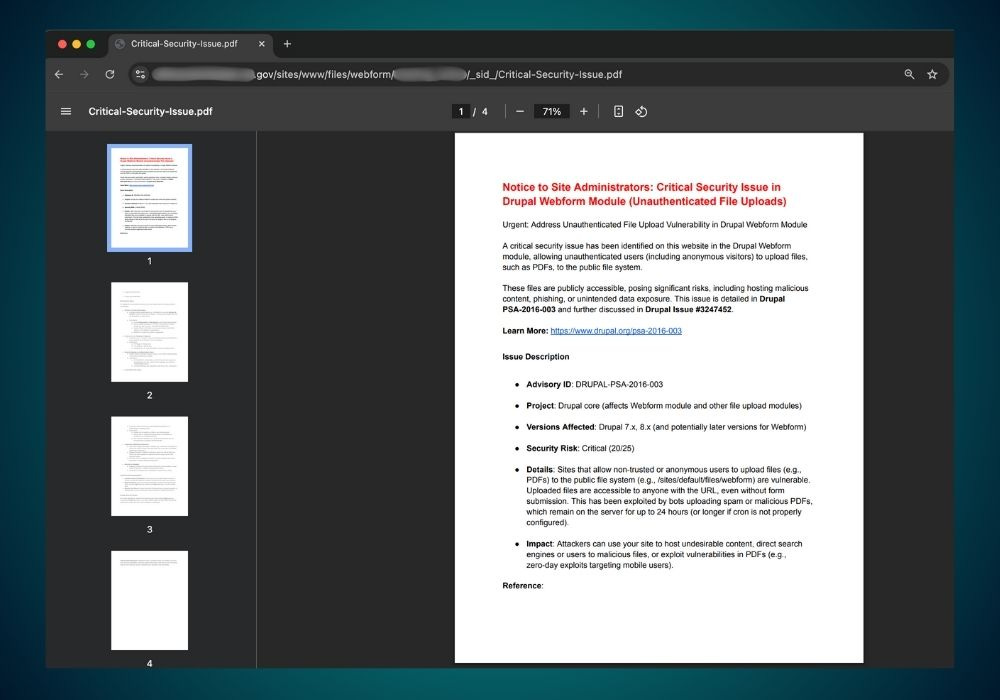
A harmless PDF named Critical-Security-Issue.pdf was created with content warning site administrators about unauthenticated file uploads.
Notice to Site Administrators: Critical Security Issue in Drupal Webform Module (Unauthenticated File Uploads)
A critical security issue has been identified in the Drupal Webform module, allowing unauthenticated users to upload files, such as PDFs, to the public file system.
These files are publicly accessible, posing risks like hosting malicious content or phishing. This issue is detailed in Drupal PSA-2016-003 and Drupal Issue #3247452. Learn more: https://www.drupal.org/psa-2...View File:
The file contains only factual information, remediation steps for the vulnerability, and official Drupal links, ensuring no harm to the website or its users.
Step 3) Open Browser Developer Tools:
Browser developer tools were opened (Ctrl + Shift + I), and the “Network” tab monitored server responses during the upload, observing behavior non-invasively.
Step 4) Upload the File:
The Critical-Security-Issue.pdf was uploaded via the Webform’s file upload field without submitting the form, as vulnerable Webforms store files immediately in public directories (e.g., /sites/default/files/webform).
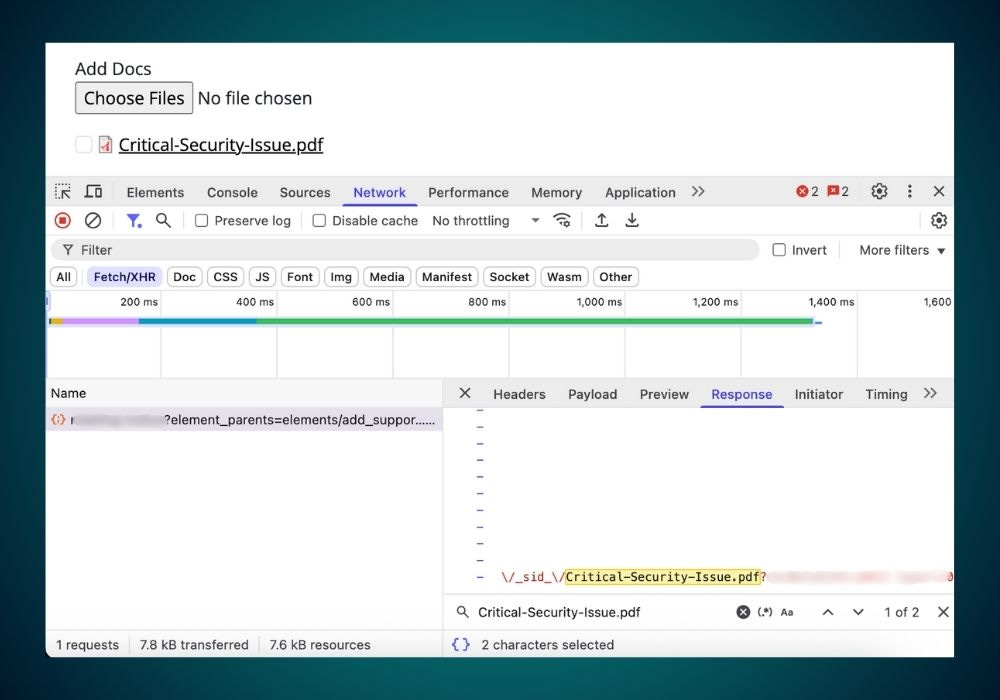
Step 5) Locate File URL:
In the “Network” tab, the server response with the file’s URL was found by searching for the filename (Ctrl + F), appearing as:
https:\/\/example.gov\/sites\/default\/files\/webform\/form_name\/_sid_\/Critical-Security-Issue.pdf.Step 6) Confirm Public Access:
The URL’s escaped slashes (\/) were replaced with regular slashes (/), and the link was accessed in a browser. The PDF loaded without authentication, confirming public directory storage and the vulnerability.
The presence of illegal movie download links on .gov and .edu websites exposes a critical security flaw in CMS platforms, allowing attackers to exploit trusted domains.
Beyond spam, these vulnerabilities could enable phishing, fraud, or malware distribution, eroding public trust and causing significant harm.
By updating systems, securing file uploads, and implementing robust access controls, administrators can mitigate these risks.
Ethical testing, as outlined, can help validate vulnerabilities without causing harm, but it must be done responsibly. Immediate action is essential to protect the integrity of these authoritative domains.
How Admins Can Protect Their Websites
To safeguard websites from vulnerabilities exploited by unauthorized file uploads, administrators must implement robust security measures promptly.
Update Plugins, Extensions, and Core - Regularly update Drupal or WordPress core, plugins, and extensions to patch vulnerabilities. Aggressive updates ensure the latest security fixes. Check weekly via Drupal’s Reports > Available Updates or WordPress’s Dashboard > Updates.
Use Managed Hosting - For sites without dedicated staff or expertise, managed hosting services like Pantheon (Drupal) or WP Engine (WordPress) handle updates, security monitoring, and server maintenance, reducing vulnerabilities through automated configurations.
Switch to Private File Systems - Configure file upload fields to store files in private directories outside the web root (e.g., /sites/default/files/private for Drupal). Set this in Drupal’s Configuration > File System or adjust WordPress plugin settings like Gravity Forms or Ninja Forms.
Restrict Uploads to Authenticated Users - Require user login for file uploads. In Drupal Webform, edit “Form settings” to limit access to authenticated roles. In WordPress, configure plugins to enforce authentication, blocking anonymous uploads.
Audit Public Directories - Inspect public file directories (e.g., /sites/default/files/webform or /wp-content/uploads) for unauthorized files. Use SSH, hosting panels, or tools like Drush (Drupal) or WP-CLI (WordPress) to review and delete suspicious files.
Implement Additional Protections - Install anti-spam modules like CAPTCHA or Honeypot, validate file types to allow only safe formats and use server-side antivirus for uploads. Configure cron (Drupal) or scheduled tasks (WordPress) to delete temporary files daily.
These steps—updates, managed hosting, private file systems, restricted uploads, directory audits, and added protections—prevent attackers from exploiting trusted domains for phishing, fraud, or malware, preserving site integrity and public trust.









Great summary of the problem, thank you.
FYI the "Educational Websites" section duplicates the list of sites.
try searching for
"delta discount senior" site:*.gov filetype:pdf
phishing all the way!