Your info is out there. Whether it’s your email, passwords, or even sensitive financial details, chances are, some of your personal data has already been exposed in a breach. Hackers trade, sell, and leak stolen information daily, fueling identity theft, scams, and cyberattacks.
You don’t have to be a high-profile target—massive breaches from companies like Facebook, LinkedIn, and T-Mobile have already exposed billions of accounts. Even old accounts you forgot about can come back to haunt you if the data falls into the wrong hands.
So, how do you find out what’s been leaked? And more importantly, how do you lock down your security before cybercriminals take advantage of it? Let’s break it down.
Disclaimer: This article is for educational and cybersecurity awareness purposes only. It does not condone or promote illegal activity in any form. The techniques and information discussed are meant for ethical security research, defense strategies, and personal data protection.
Which Companies Have Lost Data in Breaches?
The number of large-scale data breaches has only increased in the past five years, affecting billions of people worldwide. High-profile breaches include:
The National Public Data breach (2024) – Nearly 3 billion people had their personal information exposed, including potentially every American’s Social Security number.
Facebook (2021) – Personal data of over 530 million users exposed.
LinkedIn (2021) – Information of 700 million users leaked.
T-Mobile (2021) – 40 million customer records compromised.
Yahoo (2017, revealed later) – 3 billion accounts breached, making it one of the largest data breaches ever recorded.
Marriott (2018-2020) – Multiple breaches affecting over 500 million customers.
Experian (2015 & beyond) – One of the most severe breaches of 2015, affecting 15 million customers, with additional breaches occurring in later years.
New breaches emerge every year as cybercriminals, including nation-state-backed hackers, seek to exploit, disrupt, and profit from large-scale data leaks.
Where Are Breaches Leaked?
Once stolen, data spreads rapidly across hacking forums, Telegram channels, and dark web marketplaces. Cybercriminals buy, sell, and trade breached information, using it for fraud, identity theft, and cyberattacks. While some stolen data is sold for profit, hackers often leak it for free—to pressure victims, cause disruption, or simply because a buyer decides to release it.
Law enforcement agencies are cracking down harder than ever, taking down major forums at an increasing rate.
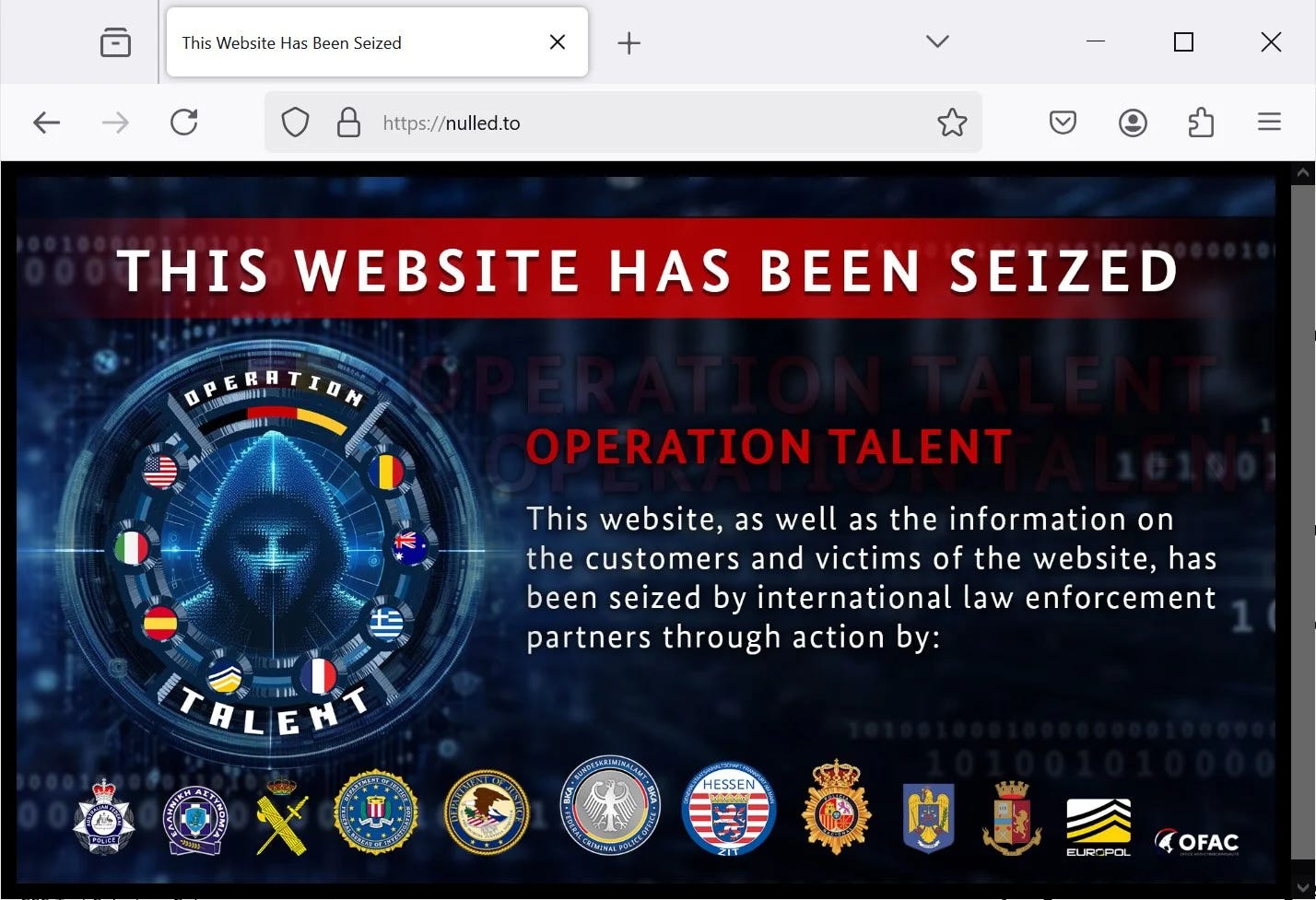
January 2025 – Operation Talent, a global effort led by the FBI, shut down major hacking forums including Cracked[.]io, Nulled[.]to, MySellIX[.]io, and StarkRDP[.]io, which were hubs for selling stolen credentials, hacking tools, and financial records.
2023 – BreachForums, one of the largest data-leak marketplaces, was seized by U.S. and international law enforcement.
2022 – RaidForums, a notorious hacking forum, was taken down in another major operation.
Despite these takedowns, cybercriminals adapt quickly. As fast as forums are seized by federal agencies, new ones pop up to take their place. Hackers shift to private Telegram groups, Discord servers, invite-only dark web sites, and self-hosted marketplaces, ensuring the stolen data keeps circulating.
No matter how many platforms are shut down, the cycle continues—fueled by new breaches, new marketplaces, and a constant demand for stolen data.
With every shutdown, cybercriminals adapt, shifting to private Telegram groups, Discord servers, invite-only dark web sites, and self-hosted marketplaces. As long as data breaches continue, new channels will always emerge to keep the cycle going.
What Kind of Data is Leaked in a Breach?
When a company suffers a data breach, attackers gain access to sensitive information, which may include:
Hashed Passwords – Encrypted but crackable passwords.
Plaintext Passwords – Some breaches expose passwords without encryption.
Email Addresses – Commonly leaked and used for phishing attacks.
Full Names & Addresses – Used for identity theft and scams.
IP Addresses – Can be used to track users or aid in further attacks.
Credit Card & Financial Data – In rare cases, unencrypted payment details are exposed.
How to Use Data Breach Information for Cybersecurity
Leaked data can be useful for gathering intelligence on a target, but obtaining this data from shady hacker forums or Telegram groups comes with legal and ethical risks.
Even if you have good intentions, visiting these forums can lead to:
Being caught up in a law enforcement sweep of the website’s users.
Getting hacked by cybercriminals operating on the platform.
Downloading malware that steals your own credentials.
Instead, use legitimate platforms that collect and share breach data in a secure and ethical way for cybersecurity research and open-source intelligence.
Legal Sources for Leaked Data
There are websites that allow users to check whether their data has been leaked:
Have I Been Pwned – Free service that tells users if their email or password has been found in a breach. It does not show the leaked data itself but indicates which breaches it appeared in.
CheckLeaked.cc – Provides two free searches per day to see what information about you has been leaked, including plaintext and hashed passwords.
DeHashed – Paid service that allows users to search for leaked personal data, including full credential sets.
Snusbase – Another lookup service that provides access to breached data.
Using Breach Data for Security Insights
Data breaches can reveal extensive details about individuals, which can be analyzed and utilized for various purposes:
Passwords and Credential Reuse – Many people reuse the same password across multiple websites. If a plaintext or weakly hashed password is exposed, it can be used to gain unauthorized access to other accounts.
Associated Online Accounts – Searching an email address in multiple breaches can reveal all the services a person has registered on.
Alternate Contact Details – If an IP address or phone number is included in a breach, cross-referencing it may uncover additional email addresses, usernames, or accounts linked to the individual.
Physical Location Information – Some breaches contain addresses and phone numbers, which could be misused for doxxing or real-world attacks.
Corporate Exposure – If a work email is compromised, it may indicate a larger organizational breach, which could be leveraged for phishing, business email compromise (BEC), and other targeted cyberattacks.
By analyzing breached data, security professionals and researchers can better understand common security failures, improve password security recommendations, and help individuals protect themselves from cyber threats.
How to Protect Yourself from Data Breaches
Sign up for email alerts on Have I Been Pwned to be notified if your data appears in a new breach.
Use a unique password for each site – Assume that if a site is breached, your password will eventually be exposed. Avoid predictable patterns like "Amazon123!" for Amazon and "Gmail123!" for Gmail.
Use a password manager like Bitwarden or 1Password to generate and store strong, unique passwords for each service.
Enable app-based two-factor authentication (2FA) – Avoid SMS-based 2FA, as phone numbers can be compromised through SIM swapping. Use apps like Google Authenticator or Authy instead.
Use a VPN – If your data is exposed in a breach, it can include your IP address, which can be used to track your online activity. Privacy-focused VPNs like ProtonVPN, based in Switzerland, provide strong legal protections against data exposure.
Data breaches are an unfortunate reality of the digital world, but by taking proactive steps, individuals and organizations can significantly reduce their risk of compromise.
Strengthening password habits, enabling multi-factor authentication, and staying vigilant against phishing attacks can go a long way in maintaining online security. Staying informed and leveraging the right tools will help protect personal and financial data from cyber threats.







Awesome content! Keep it up!