How to Create an Infrastructure Security Plan for Your Business
Cyberattacks are surging, with global data breaches rising 78% in 2024, per IBM’s Cost of a Data Breach Report.
Small businesses face devastating consequences, as 60% shut down within six months of a major breach.
Hackers today have access to advanced tools like AI to launch ransomware, phishing, and supply chain attacks, sparing no company, regardless of size. The risks—lost revenue, legal battles, and shattered customer trust—can ruin your business.
For small business owners, operators, and CEOs, cybersecurity is essential in 2025 to safeguard your livelihood. A single breach can undo years of hard work and destroy your reputation.
What’s Inside the Guide?
This guide offers a straightforward, step-by-step plan to protect your business by identifying critical operations, evaluating risks, and building robust defenses. Follow these steps to strengthen your cybersecurity and safeguard your livelihood.
Here’s what you’ll find:
Step 1: Identify Critical Functions - Pinpoint essential operations (e.g., payment processing, client data) and their security needs to prioritize protection.
Step 2: Baseline Infrastructure - Document your IT setup, including hardware, software, and security controls, to spot vulnerabilities.
Step 3: Risk Assessment - Evaluate cyber risks like ransomware and data breaches, assessing their likelihood and impact.
Step 4: Defense-in-Depth - Build layered defenses with firewalls, multi-factor authentication, and least privilege access to block attacks.
Step 5: Monitor the Network - Set up tools and schedules for continuous monitoring to detect threats early.
Step 6: Secure Software - Harden operating systems, websites, and databases with updates, encryption, and access controls.
Step 7: Secure Behavior - Implement policies and incident response plans to address human risks and recover quickly from breaches.
By following these steps, you’ll build a solid cybersecurity plan that fortifies your defenses, boosts resilience, and secures your business’s future. Let’s get started!
How to Create an Infrastructure Security Plan
The Infrastructure Security Plan outlines a structured approach to safeguard an organization's critical IT functions against cyber threats through a comprehensive seven-step framework.
Step 1) Identify Critical Functions
The first step involves pinpointing essential organizational functions supported by IT, focusing on organizational goals and compliance requirements.
This includes identifying critical operations such as point-of-sale transactions or data privacy functions and assessing their specific security requirements to understand what must be protected.
Step 2) Baseline Infrastructure
This stage conducts a thorough assessment of the current security posture through comprehensive inventory and future planning initiatives.
It covers an inventory of entry and exit points, systems in use, patch management status, and existing security controls. This baseline establishes the foundation for understanding current capabilities and identifying gaps that need to be addressed in future security enhancements.
Step 3) Risk Assessment
A critical evaluation that examines both likelihood and business impact to identify the top cyber risks affecting the organization. This comprehensive analysis includes understanding how these threats could be exploited, the probability of occurrence, and the potential impact on critical functions, enabling organizations to prioritize their security investments effectively.
Step 4) Defense-in-Depth
This phase implements multilayered security recommendations involving secure perimeter defenses, robust AAA (Authentication, Authorization, Accounting) implementations, and strict adherence to the principle of least privilege across all systems. This approach ensures that multiple security barriers protect critical assets, so if one layer fails, others continue to provide protection.
Step 5) Monitor the Network
Establishes comprehensive methods for continuous network monitoring through systematic collection, detection, and analysis processes. This includes specifying appropriate tools and defining frequencies for both automated and manual security checks to ensure ongoing visibility into network activities and potential threats.
Step 6) Secure Software
The plan proposes specific security controls across all software components, including operating systems (OS), web applications, databases, and other applications to mitigate vulnerabilities. This comprehensive approach addresses security at every software layer to prevent exploitation of system weaknesses.
Step 7) Secure Behavior
This final section emphasizes the critical human element through incident response procedures and administrative controls.
It addresses human factors in security, establishes clear incident response processes for security breaches, and defines measures to quickly restore affected critical functions while maintaining operational continuity.
This structured approach ensures that security investments align with business priorities while providing comprehensive protection across all organizational assets.
Step 1: Identify Critical Functions
The first step in developing a strong cybersecurity plan is to pinpoint the critical functions of your organization. These functions are vital processes that support your mission and objectives. Protecting them should be a top priority, as any disruption can lead to serious consequences.
Define Critical Functions: Start by listing all the critical functions that depend on IT infrastructure. Focus on operations essential for running your business efficiently.
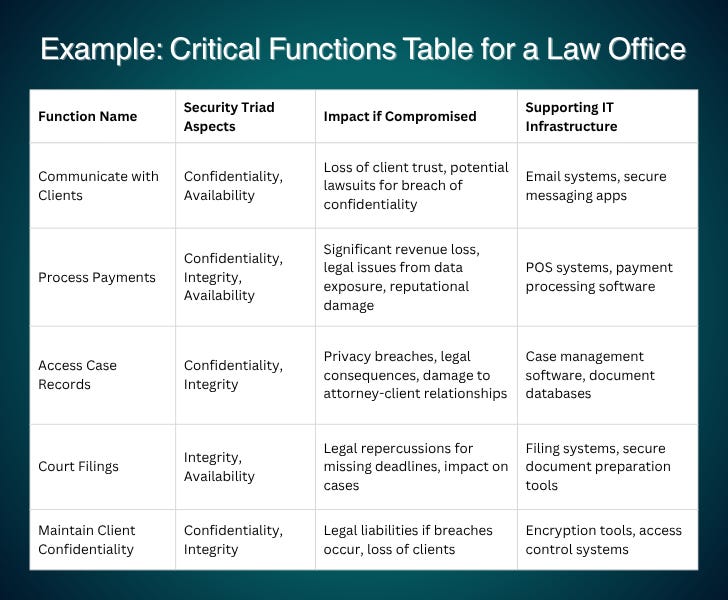
For instance, let's examine the critical functions of an attorney's office. Key functions include:
Communicating with Clients: Essential for maintaining relationships and handling cases.
Conducting Court Filings: Necessary for submitting legal documents and meeting deadlines.
Accessing Case Records: Important for preparing legal arguments and ensuring accuracy.
Maintaining Client Confidentiality: Crucial for protecting sensitive information and upholding legal ethics.
Inter-Office Communication: Enables collaboration among attorneys and staff.
Using Computers and Internet: Supports documentation, research, and case management.
A. List Your Critical Functions
What are your business’s critical functions?
Take a moment to write down as many as you can think of. This exercise will help you clarify which areas require robust cybersecurity measures.
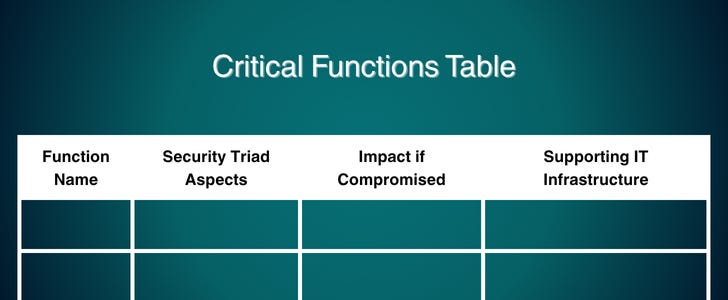
B. Create a Critical Functions Table
The next step is to develop a Critical Functions Table. This table serves as a visual organization of the essential functions you identified in the previous step.
It helps clarify the importance of each function and provides a structured way to evaluate their security needs.
How to Structure the Table
Function Name: Start with the title of each critical function. For example, "Communicate with Clients" or "Process Payments." This labels what each component of your operation is.
Security Triad Aspects: Identify the security aspects essential for each function. The security triad consists of three key concepts:
Confidentiality: This means keeping sensitive information private and ensuring that only authorized individuals can access it. For instance, client records in a law office should only be seen by lawyers and their staff.
Integrity: This ensures that data remains accurate and unaltered without permission. Any changes to client information must be authorized and documented. For example, if a case file is modified, only the lawyer assigned should have the ability to do so.
Availability: This focuses on ensuring that critical functions and data are accessible when needed. If a lawyer needs to access a case file urgently, the system should be operational and available at that time.
Impact if Compromised: Assess what could happen if each function were breached. Think about these consequences:
Financial Losses: This includes immediate revenue loss from disrupted operations or costs to recover from a breach. For example, if payment processing is down, money can't flow into the business.
Legal Repercussions: This covers potential fines or legal action resulting from data breaches. For instance, compromised client confidentiality could lead to lawsuits.
Reputation Damage: Consider how a breach would affect the trust client's place in your organization. If clients feel their data isn't safe, they may choose to take their business elsewhere.
Supporting IT Infrastructure: List the specific IT systems, networks, and software that support each function. Identifying these helps clarify where to direct security efforts. For example, for “Process Payments,” you might include:
Systems: Point-of-sale terminals and payment processing servers.
Software: Payment processing applications and customer management systems.
Network: Secure internet connections that handle payment transactions.
By utilizing this Critical Functions Table, you gain a clearer understanding of your organization's cybersecurity landscape. This documentation allows you to prioritize which functions require immediate attention and resources.
Step 2) Develop a Baseline
Developing a baseline for your infrastructure security involves creating a comprehensive snapshot of your current IT environment to understand its security posture and identify areas for improvement.
This step establishes a foundation for your cybersecurity plan by documenting existing systems, networks, security controls, and planned upgrades. Below, we outline how to develop a thorough and exhaustive baseline, addressing each component as described in the provided guidance.
A comprehensive baseline ensures you have a clear understanding of your systems, networks, and security controls, enabling you to prioritize resources and address gaps effectively.
What Does It Mean to Develop a Baseline?
Developing a baseline means creating a detailed, documented inventory of your organization's IT infrastructure, including all hardware, software, networks, and security controls currently in place.
This snapshot serves as a reference point to evaluate your security posture, identify weaknesses, and plan for future enhancements. The baseline answers the question, "Where are we now?" and provides a foundation for comparing your current state to desired security standards or compliance requirements.
The baseline is not a one-time activity; it should be regularly updated to reflect changes in your IT environment, such as new systems, software updates, or evolving threats. By establishing a clear and comprehensive baseline, you can:
Identify vulnerabilities: Pinpoint gaps in security controls or unpatched systems.
Prioritize resources: Focus on protecting critical functions and assets.
Measure progress: Track improvements over time as you implement security measures.
Ensure compliance: Align with regulatory requirements, such as GDPR, HIPAA, or PCI-DSS, by documenting systems and controls.
Steps to Developing a Baseline:
Follow the steps below and complete the prompts to develop your baseline. To help illustrate how to complete each step, we'll use the example of a mid-sized law firm called Sterling & Rhodes, LLP working through their baseline assessment.
1. Overall Description of the Infrastructure
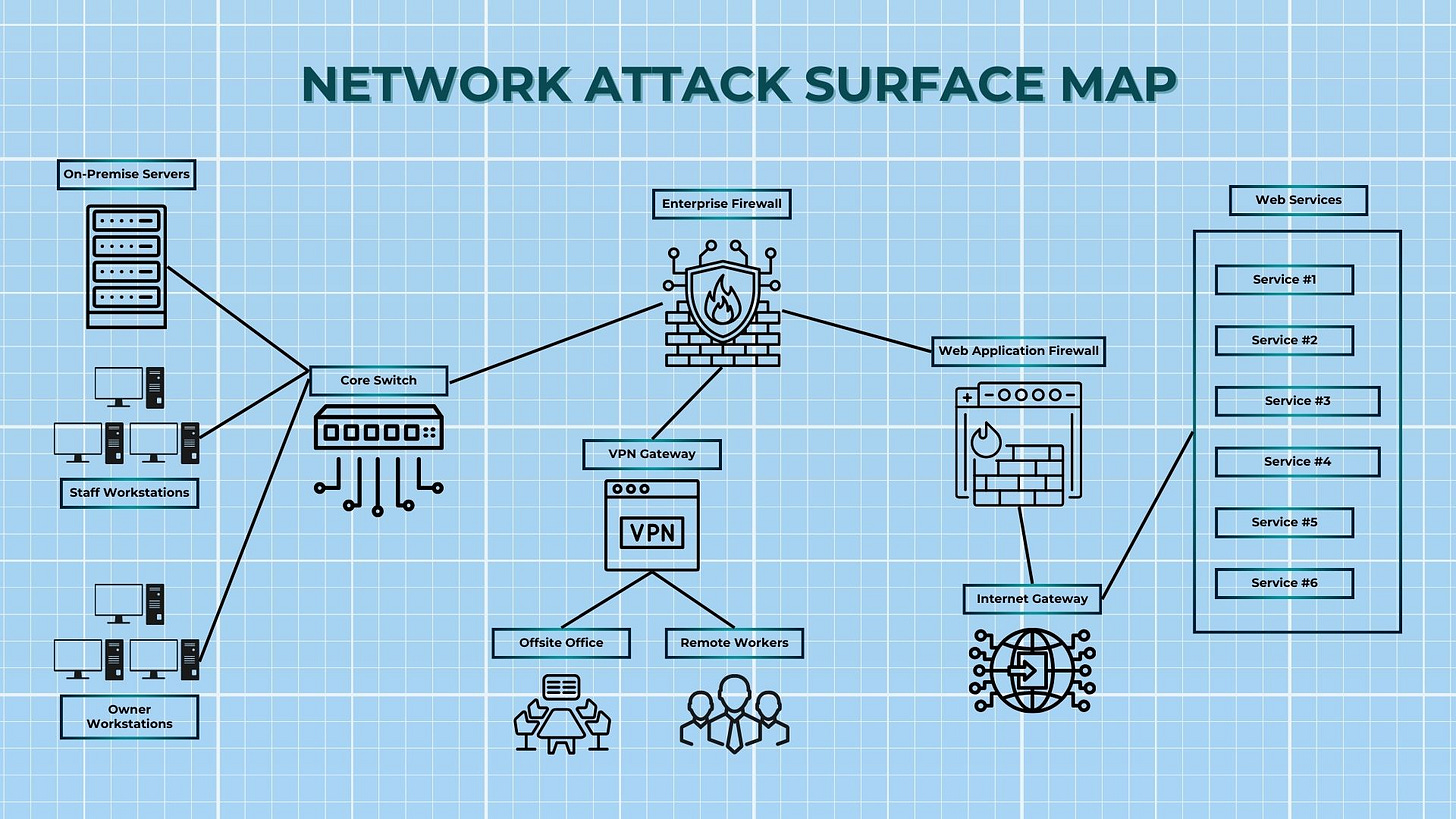
You need a clear view of your IT setup—servers, PCs, networks, cloud tools—and their purpose (e.g., managing client data, processing orders). A diagram shows how everything links, helping you spot vulnerabilities hackers could exploit.
Prompt: Write a brief overview of your IT environment, listing main components (e.g., servers, PCs, networks, cloud services) and their purpose (e.g., client data, order processing). Draw a simple diagram showing connections.
Example Answer:
“We run our practice on a mix of on-site equipment and cloud services. Our main file server sits in our office closet—it's a Dell that stores all our case files and contracts. Everyone has either a desktop computer or laptop, about 20 machines total.
We use Clio for managing cases and billing clients, which runs in the cloud. Our internet comes through a fiber line, and we have a backup system that saves everything overnight. The phones are internet-based and tie into our case management system so we can see who's calling about which case.Everything connects through our main network, with Wi-Fi for the attorneys who use laptops and a separate guest network for clients. The main server talks to all the computers, and everything goes out through our internet connection to reach the cloud services we depend on.”
2. Networks
Networks (wired, Wi-Fi, cloud) are how your data moves. Unsecured or poorly configured networks let hackers spread fast. Listing them helps you secure connections and limit damage.
Prompt: List all networks (e.g., wired, Wi-Fi, cloud) and describe their configuration.
Example Answer:
“We have three separate networks. The main office network connects all our computers and the server through ethernet cables. Our staff Wi-Fi is password-protected and lets attorneys use their laptops anywhere in the office. We also set up a guest Wi-Fi for clients that doesn't connect to our internal systems.
For remote work, we have a VPN that lets attorneys access files from home. All our cloud services—email, case management, legal research—connect through our main internet line. The networks are set up so guests can't see our internal files, and remote users have to use two-factor authentication to get in.”
3. Entry and Exit Points
These are where data enters or leaves—internet, VPNs, vendor connections, USB ports, smart devices. Hackers target these to get in. Knowing every point lets you lock them down.
Prompt: List all points where data enters or leaves (e.g., internet, VPNs, vendor connections, USB ports, smart devices).
Example Answer:
“Data comes and goes through several channels. Our main internet connection handles email, web browsing, and cloud services. Remote attorneys connect through VPN from their homes. We file documents electronically with courts through their online portals.
Physical entry points include USB drives that attorneys use for large documents and court filings. Everyone has work phones that sync with email and calendars. Our scanner connects to the network to digitize paper documents. We also have direct connections to our legal research database and our banking system for client trust accounts.
The reception area computers can access USB ports for client document scanning, but we've restricted USB access on most other workstations.”
4. Systems in the Infrastructure
Every device (servers, PCs, smart devices) and software (e.g., email, accounting tools) is a potential weak spot. Cataloging them ensures you know what to secure.
Prompt: List all devices (e.g., servers, PCs, smart devices) and their software (e.g., Windows, email apps), including version numbers.
Example Answer:
“Our hardware includes one main server, 15 desktop computers, 5 laptops for attorneys, three printers, our firewall device, and network equipment. Everything runs Windows—the server has Windows Server 2019, and all the computers have Windows 11.
For software, we use Clio for case management, Office 365 for email and documents, QuickBooks for accounting, and LexisNexis for legal research. Everyone has Adobe Acrobat for PDF work. We run Bitdefender antivirus on all machines.
Most software updates automatically, but QuickBooks we update manually because we've had compatibility issues before. Some attorneys turn off automatic updates on their laptops, which creates problems keeping everything current.”
5. OS Patch Management
Patching fixes security holes in systems and software. Skipping updates leaves you open to attacks. Documenting your process shows if you're protected or vulnerable.
Prompt: Describe how you update systems and software, including schedules and tools (e.g., auto-updates, patch management software), and note any gaps.
Example Answer:
“Windows updates happen automatically on most computers, usually on the second Tuesday of each month. Our server gets updated manually during maintenance windows—typically the first Sunday morning when nobody's working.
Office 365 and our cloud services update themselves. The antivirus definitions update daily. Network equipment gets firmware updates twice a year when our IT vendor comes in.
The main gaps are with QuickBooks, which we're often slow to update, and some attorneys who disable Windows updates on their laptops because they don't want interruptions during client meetings. We don't have a good system for tracking what version of software is on each computer.”
6. Workstation and Server Security Controls
Defenses like antivirus, encryption, or firewalls on PCs and servers block hackers. Listing what's in place and their settings shows if your devices are safe or exposed.
Prompt: List defenses on PCs and servers (e.g., antivirus, encryption, firewalls) and their settings (e.g., auto-updates enabled, unused services disabled).
Example Answer:
“All computers have Bitdefender antivirus that scans files in real-time and updates daily. Windows Firewall runs on everything with default settings. The laptops have BitLocker encryption turned on, but we haven't encrypted the desktop computers yet.
Our server runs Windows Defender and does full scans weekly. We've turned off services we don't need and set up the file sharing so only certain people can access different folders. Computers lock after 10 minutes if nobody's using them.
The reception computers have USB restrictions so clients can't plug in random devices. We still need to encrypt the desktop computers and add encryption to our server drives.”
7. AAA (Authentication, Authorization, Accounting)
This controls who gets in (authentication), what they can do (authorization), and tracks their actions (accounting). Weak controls let intruders slip through. Clear processes stop them and help trace issues.
Prompt: Describe user authentication (e.g., passwords, MFA), authorization (e.g., access limits), and activity tracking (e.g., logs).
Example Answer:
“Everyone logs in with their own username and password. Passwords have to be 12 characters with numbers and symbols, and they expire every 90 days. Email and VPN access require two-factor authentication through an app on your phone.
We've set up different permission levels—partners can see everything, associates can access their own cases, paralegals have limited access, and administrative staff can only reach billing and scheduling systems. File access depends on which practice area you work in.
The system tracks when people log in and out, and our case management software records who accessed which files. Email activity gets logged too. We don't have alerts set up for unusual activity, and we don't regularly review these logs unless there's a problem.”
8. Other Security Controls
Extra defenses like firewalls, intrusion detection, encryption, or backups add layers to stop attacks and aid recovery. Policies (e.g., password rules, device policies) keep everyone aligned. Listing these shows your strengths and gaps.
Prompt: List additional defenses (e.g., firewalls, intrusion detection, encryption, backups) and policies (e.g., password rules, device policies), including their settings.
Example Answer:
“Our firewall blocks suspicious traffic and has intrusion detection turned on. We back up all files nightly to a storage device in the office, and important data gets backed up to the cloud weekly. Office 365 protects our email from spam and malicious links.
We have written policies about cybersecurity, password requirements, and keeping client information confidential. Personal devices aren't allowed for work, and we have rules about keeping papers locked up. There's a basic plan for what to do if we get hacked.
Our biggest gaps are in training—we don't have regular cybersecurity training for staff, and we don't have a detailed disaster recovery plan. We tested our backups about six months ago, but we should do it more regularly. If something major happened, we estimate it would take about a day to get back up and running, but we haven't documented exactly how we'd do that.”
Step 3) Risk Assessment
Now that you've identified your critical functions and documented your current infrastructure, it's time to assess the cyber risks that could impact your business.
This step evaluates both the likelihood of different attacks and their potential impact on your operations.
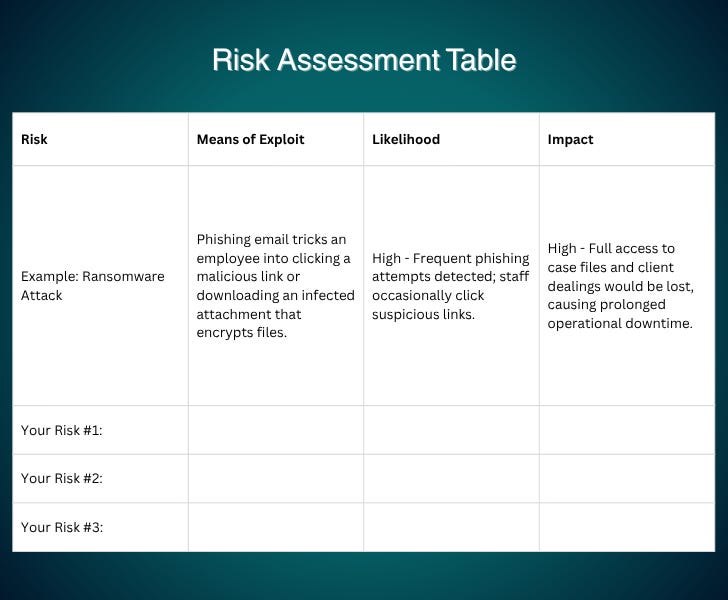
Your Task: Identify as many cyber risks as you can and document them using the framework below. For each risk, describe:
Means of Exploit: How would an attacker carry out this attack?
Likelihood: How probable is this attack? (High/Medium/Low with reasoning)
Impact: What would happen to your critical functions if this occurred? (High/Medium/Low with reasoning)
Remember, there's no point spending money to protect against something that's unlikely to happen or would have minimal impact on your critical functions. Sometimes the best choice is to simply accept certain risks rather than implement expensive controls.
Example Risks:
For the law firm, Sterling & Rhodes, LLP, the following risks were identified and serve as examples you can follow for your own assessment.
Risk #1: Ransomware Attack
Means of Exploit: Employee receives convincing phishing email and clicks malicious attachment or link. Ransomware encrypts all accessible files on the network, including the main server and connected workstations.
Likelihood: High - We get phishing emails daily, and staff sometimes click suspicious links. Our email filtering catches obvious spam but sophisticated attacks get through.
Impact: High - Would encrypt all case files, client records, and billing data. We'd lose access to everything needed to serve clients and run the business. Even with backups, recovery could take days or weeks.
Risk #2: Data Breach via Compromised Credentials
Means of Exploit: Attacker obtains employee login credentials through password reuse, weak passwords, or credential stuffing attacks. Uses legitimate access to steal client data and confidential case information.
Likelihood: Medium - Some employees reuse passwords across multiple sites. We don't have multi-factor authentication on internal systems, only cloud services.
Impact: High - Breach of client confidentiality would destroy our reputation and result in legal liability. Could face regulatory fines and lawsuits from affected clients.
Risk #3: Business Email Compromise
Means of Exploit: Attacker gains access to partner's email account and sends fraudulent wire transfer instructions to clients or requests confidential information by impersonating the attorney.
Likelihood: Medium - Partners are high-value targets, and their email accounts contain sensitive information. Social engineering attacks targeting executives are increasing.
Impact: Medium - Could result in financial loss if clients send money to wrong accounts. Would damage client relationships and firm reputation. Potential legal liability for compromised client communications.
Next Steps: The following sections (Defense-in-Depth, Network Monitoring, etc.) will help you implement security controls specifically designed to reduce either the likelihood of these risks occurring or their impact if they do happen.
Step 4) Defense in Depth
Defense in Depth is a comprehensive cybersecurity strategy that employs multiple layers of security controls to protect critical functions from cyber threats.
By dispersing defenses across various layers—such as securing the perimeter, implementing AAA (Authentication, Authorization, and Accounting) systems, and enforcing the principle of least privilege—organizations can enhance their resilience against potential attacks.
This multifaceted approach ensures that if one layer is compromised, others still provide a critical defense, thereby reducing overall risk.
Your Task: Develop a Defense-in-Depth strategy by answering the prompts below. For each, list specific controls, their locations, and how they protect your critical functions. Use the example from Sterling & Rhodes, LLP, to guide your responses, but tailor them to your business’s unique needs.
a) Defending the Perimeter
Securing the perimeter of your infrastructure is critical to block unauthorized access and protect sensitive data from external threats.
Question: How will you defend the perimeter of your infrastructure? List controls and their locations.
Consider firewalls, intrusion detection/prevention systems (IDS/IPS), secure Wi-Fi configurations, VPNs for remote access, and email security gateways. Specify where each control is applied (e.g., network edge, access points).
Example (Sterling & Rhodes, LLP):
Next-Generation Firewall: Deployed at the main internet gateway to filter traffic and block unauthorized access to the office network, protecting client data and case management systems.
Intrusion Detection/Prevention System (IDS/IPS): Installed at the network edge to monitor and block malicious activities targeting the server and workstations.
Secure Wi-Fi Networks: WPA3 encryption for staff Wi-Fi and a separate guest Wi-Fi at all office access points, preventing unauthorized access to internal systems.
VPN Enforcement: AES-256 encrypted VPN at the network entry point for remote attorneys accessing case files or email.
Email Security Gateway: Cloud-based filter at the mail server to block phishing emails and malicious attachments before they reach staff inboxes.
b) Implementing AAA
AAA (Authentication, Authorization, Accounting) systems manage who can access your network, what they can do, and track their actions to ensure security and accountability.
Question: How will AAA be implemented? List your strategy for Authentication, Authorization, and Accounting.
For Authentication, consider strong passwords and multi-factor authentication (MFA). For Authorization, use role-based access controls. For Accounting, enable logging to track user activities. Specify tools and configurations.
Example (Sterling & Rhodes, LLP):
Authentication: Enforce MFA for all users accessing email, Clio case management, VPN, and LexisNexis, using authenticator apps. Require 12-character passwords with numbers and symbols, expiring every 90 days.
Authorization: Role-based access: partners have full access to all case files; associates access only their cases; paralegals and staff are limited to billing and scheduling. File permissions on the server enforce these restrictions.
Accounting: Enable logging in Clio and Office 365 to track login times and file access. Set up alerts for unusual activity, reviewed weekly by the IT vendor.
c) Ensuring "Least Privilege"
The principle of least privilege limits user access to only what’s necessary for their role, reducing the risk of unauthorized access or insider threats.
Question: How will you ensure “least privilege”? List controls and their locations.
Specify access restrictions for systems, files, and applications. Consider user roles, file permissions, and network segmentation.
Example (Sterling & Rhodes, LLP):
Role-Based File Access: Configure the server to restrict case file access: partners see all files, associates see only their cases, and administrative staff access only billing folders.
Network Segmentation: Separate staff and guest Wi-Fi to prevent clients from accessing internal systems.
Application Restrictions: Limit QuickBooks access to accounting staff and disable USB ports on most workstations, except at reception for client document scanning.
d) Implementing Patch Management
Regularly updating software closes security vulnerabilities, keeping systems secure against known exploits.
Question: How will you implement “patch management” to ensure systems are kept up to date in the most secure state?
Describe your process for updating operating systems, applications, and network devices, including schedules, tools, and manual checks.
Example (Sterling & Rhodes, LLP):
Automated Updates: Enable Windows automatic updates for desktops and laptops, applied monthly on Patch Tuesday.
Manual Server Updates: Schedule server updates (Windows Server 2019) for the first Sunday of each month during low-usage hours, managed by the IT vendor.
Software Updates: Configure Office 365 and Bitdefender antivirus for automatic updates. Manually update QuickBooks quarterly to avoid compatibility issues.
Patch Tracking: Use a patch management tool to track software versions across all devices, with monthly reports to identify unpatched systems.
e) Other Defense-in-Depth Methods
Additional security layers, like host-based protections or backups, strengthen your defenses and aid recovery.
Question: What other Defense-in-Depth methods will you implement?
Consider host-based firewalls, antivirus software, encryption, backups, or security policies. Specify their implementation and purpose.
Example (Sterling & Rhodes, LLP):
Host-Based Firewalls: Enable Windows Firewall on all desktops and laptops with default settings to block unauthorized access.
Antivirus Protection: Run Bitdefender on all devices with real-time scanning and daily definition updates.
Data Encryption: Use BitLocker on all laptops and server drives to protect client data if devices are stolen.
Nightly Backups: Back up case files and billing data to an on-site storage device and weekly to a secure cloud service, tested quarterly.
Security Policies: Enforce policies prohibiting personal devices for work and requiring locked file cabinets for physical documents.
Next Steps: Use your answers to build a layered defense strategy. Document these controls in your security plan to ensure comprehensive protection. In the next step, you’ll establish network monitoring to detect and respond to threats in real time.
Step 5) Monitor the Network
While Defense in Depth provides a robust framework for cybersecurity, it is essential to recognize that it is “necessary but not sufficient” in the face of advanced threats. Continuous monitoring of the network is vital for identifying and responding to potential security incidents in real time.
By implementing effective monitoring strategies, organizations can gain visibility into their network activities and proactively address vulnerabilities before they can be exploited.
To define how you will monitor the network for your infrastructure, please answer the following prompts:
a) Monitoring Tools: Identify the tools that will be implemented to monitor the network. These can include both automated systems and manual procedures, such as regularly reviewing firewall logs. Automated tools may encompass configuration of system logging, firewall logging, packet capture and analysis, and intrusion detection/prevention systems (IDS/IPS).
Question: Describe the tools that will be implemented to monitor the network.
b) Human Analysis Frequency: For aspects of network monitoring that require human oversight, it is important to establish how often analyses will be conducted. Consider whether this will occur daily, weekly, or monthly, based on the needs of your organization.
Question: For aspects of network monitoring that require human analysis, describe the frequency of the analysis activity.
Step 6) Secure Software
Software vulnerabilities in operating systems, web applications, and databases are common entry points for attackers.
By implementing targeted security controls, you can reduce risks and strengthen your infrastructure. This step focuses on applying specific measures to ensure all software components are hardened against exploitation, aligning with the layered defense strategy outlined earlier.
Your Task: Develop a Secure Software Strategy
Answer the following questions to define how you will secure your software. For each, describe specific controls, their purpose, and where they apply.
These controls should address vulnerabilities at every software layer, ensuring comprehensive protection for your critical functions.
To detail your secure software strategy, please answer the following prompts:
1. Operating System Specific Controls
Operating systems (OS) like Windows or Linux are foundational to your infrastructure. Unsecured OS configurations or unpatched systems can expose your business to attacks like ransomware or privilege escalation.
Question: What controls will you implement for the specific operating systems in your infrastructure?
List controls such as hardening configurations (e.g., disabling unnecessary services), enforcing access controls (e.g., limiting admin privileges), and maintaining patch management (e.g., timely updates). Specify the OS and how controls are applied.
Example (Sterling & Rhodes, LLP):
Hardening Configurations: For Windows Server 2019 and Windows 11, disable unused services (e.g., Remote Desktop Protocol unless needed) and remove default accounts to reduce attack surfaces.
Access Controls: Enforce least privilege by limiting administrative accounts to IT staff only; all other users have standard accounts to prevent unauthorized changes.
Patch Management: Apply Windows updates automatically on Patch Tuesday for workstations, with manual updates for servers during monthly maintenance windows to ensure systems are protected against known vulnerabilities.
Security Tools: Use Windows Defender with real-time protection enabled and weekly full scans to detect malware or exploits targeting OS vulnerabilities.
2. Website Specific Controls:
Websites, whether public (e.g., a law firm’s marketing site) or internal (e.g., a client portal), are vulnerable to attacks like SQL injection, cross-site scripting (XSS), or defacement. Securing them is essential to protect your brand and client interactions.
Question: What website-specific controls will you implement?
List controls like Web Application Firewalls (WAF), HTTPS enforcement, secure coding practices, and regular vulnerability scanning. Specify the website type (e.g., public, internal) and how controls safeguard critical functions. If no websites are used, state “NONE.”
Example (Sterling & Rhodes, LLP):
Website Type: Public-facing website (www.sterlingrhodes.com) (www.sterlingrhodes.com) hosted on WordPress for marketing, client intake forms, and attorney bios.
Web Application Firewall (WAF): Deploy a cloud-based WAF (e.g., Cloudflare) to filter malicious traffic and block SQL injection or XSS attempts targeting the website.
HTTPS Enforcement: Configure the website to use TLS 1.3 with a valid SSL certificate to encrypt all client data submitted via contact forms.
Secure Coding Practices: Use a vetted WordPress theme and plugins, with automatic updates enabled to patch vulnerabilities; disable unused plugins to reduce attack surfaces.
Vulnerability Scanning: Conduct monthly scans using tools like WPScan to identify and fix vulnerabilities in WordPress core, themes, or plugins.
3. Database Specific Controls:
Databases often store sensitive data, making them high-value targets for attackers seeking to steal or manipulate information. Robust controls are essential to protect data integrity and confidentiality.
Question: What specific controls will you implement for databases in your infrastructure?
Include controls like encryption, access restrictions, regular backups, and monitoring for unauthorized access. Specify the database type (e.g., SQL Server, MySQL) and how controls safeguard critical data.
Example (Sterling & Rhodes, LLP):
Encryption: Use AES-256 encryption for the SQL Server database storing client records in Clio to protect data at rest and in transit.
Access Controls: Restrict database access to authorized users (e.g., partners and billing staff) via role-based permissions; disable default admin accounts.
Regular Backups: Back up the database nightly to an encrypted on-site storage device and weekly to a secure cloud service, with quarterly restoration tests to ensure recoverability.
Monitoring: Enable SQL Server audit logs to track access and changes, reviewed weekly by the IT vendor to detect unauthorized activity.
Step 7) Secure Behavior
The human element is a critical factor in cybersecurity, as employee actions can introduce risks or mitigate them.
Administrative controls and robust incident response processes are essential to address human-related vulnerabilities and ensure your organization can respond effectively to security incidents.
This step focuses on establishing policies to guide secure behavior and defining clear procedures to handle breaches, aligning with the comprehensive security framework outlined earlier (e.g., protecting critical functions like client confidentiality for a law firm). Below, we guide you through creating these controls and processes, using the example of Sterling & Rhodes, LLP, a mid-sized law firm, where relevant.
Your Task: Develop a Secure Behavior Strategy
Answer the following questions to define how you will address human-related risks and respond to incidents. For each, describe specific controls or processes, their purpose, and how they protect critical functions.
1. Administrative Controls
Administrative controls are policies and procedures that shape employee behavior to reduce risks to critical functions. These controls ensure staff follow secure practices and align with organizational security goals.
Question: What administrative controls will you implement to mitigate identified risks to critical functions?
Include policies such as password management, employee account termination procedures, secure physical access controls, and regular cybersecurity training. Specify how these controls address risks like phishing or insider threats.
Example (Sterling & Rhodes, LLP):
Password Management Policy: Require 12-character passwords with numbers and symbols, changed every 90 days, to prevent credential theft via phishing or weak passwords.
Account Termination Procedures: Deactivate employee accounts within 24 hours of departure, managed by the IT vendor, to prevent unauthorized access by former staff.
Physical Access Controls: Lock file cabinets containing client documents and restrict server room access to IT staff to protect sensitive data.
Cybersecurity Training: Conduct quarterly training sessions for all staff on recognizing phishing emails and secure data handling to reduce human error.
Purpose: These controls minimize risks like data breaches from compromised credentials or unauthorized physical access, protecting client confidentiality and case records.
2. Incident Response
A clear incident response process ensures your organization can quickly address security incidents, minimize damage, and restore critical functions. This process defines roles, actions, and steps to assess and recover from attacks.
Question: What incident response process will you use for security incidents impacting critical functions? Address the following:
Who would be responsible?
What actions would they initially take?
How would the scope and impact of the attack be determined?
How would critical functions be quickly restored?
Specify a response team, initial steps (e.g., isolating systems), methods to assess damage (e.g., log analysis), and recovery procedures (e.g., restoring backups). Ensure the process aligns with critical functions like client communications or payment processing.
Example (Sterling & Rhodes, LLP):
Who is Responsible: The IT vendor leads the response, supported by the managing partner for decision-making and the office manager for staff coordination.
Initial Actions: Disconnect affected systems from the network (e.g., unplug Ethernet or disable Wi-Fi) to contain the breach; notify the IT vendor immediately to begin analysis.
Scope and Impact Assessment: Review firewall and audit logs (e.g., SQL Server, Office 365) to identify compromised systems and data; check for unauthorized access to client records or case files. Engage a forensic consultant if the breach is severe (e.g., ransomware like the 2024 CDK Global attack).
Restoring Critical Functions: Restore affected systems using nightly on-site backups or weekly cloud backups, tested quarterly for reliability; prioritize access to Clio for case management and client communications. Notify clients if confidential data is compromised, per legal requirements.
Purpose: Ensures rapid containment and recovery, minimizing downtime and protecting client trust and legal operations.
A Plan to Protect Your Business
Next Steps: With your secure behavior strategy in place, you’ve completed a comprehensive cybersecurity plan. Regularly review and update all steps (1-7) to adapt to new threats and ensure ongoing protection of your critical functions.
If you have any questions, or need any help, let me know by leaving a comment! I read all of them and will reply to you as soon as possible.