Hping3 for Ethical Hackers: Crafting Packets, Probing, Denial of Service & Firewall Evasion
Hping3 is a packet crafting tool that gives you direct control over individual network packets for security testing and advanced network analysis.
Key capabilities for ethical hackers include:
Craft Custom Packets: Build TCP, UDP, ICMP, and raw IP packets with full control over headers, flags, timing, and payload.
Probe Hosts and Ports: Manually discover hosts and scan ports when automated tools are blocked or too noisy.
Test Firewalls and IDS/IPS: Send specific or unusual traffic to check how security devices respond.
Traffic and DoS Simulation: Generate high-rate or abnormal traffic to test DDoS defenses and system resilience.
Hping3 in Your Workflow:
Hping3 fits into penetration tests after you finish broad discovery with a network‑mapping tool like Nmap.
Once Nmap identifies hosts, ports, and services, Hping3 can probe those targets with custom traffic and test edge cases that scanners can’t handle.
Common uses include:
A firewall is blocking automated scans because it detects Nmap’s signatures, so raw, custom packets are more likely to pass.
Specific hosts or services have been identified, and you need precise, controlled packets to test how they respond under certain conditions.
You need to verify firewall rules, analyze packet handling, or send traffic patterns that automated tools can’t generate.
Hping3 complements network scanning tools by providing manual, packet-level control for precise and targeted testing. It does not perform automated scanning, but rather sends the packets you craft while reporting the responses.
Think of it like a scalpel for network testing: precise, controlled, and fully in your hands: letting you probe, manipulate, and analyze traffic in targeted ways that automated scanning tools can’t.
The History of Hping3
Hping was created by Salvatore Sanfilippo (”Antirez”) in the late 1990s.
The original utility focused on TCP packet crafting for tasks like firewall testing and network probing. Sanfilippo developed Hping3 starting in 2004 as a major evolution. The redesign was driven by the need to:
Expand Protocol Support: Incorporate functionality for protocols beyond TCP, including ICMP, UDP, and RAW-IP modes.
Enable Scripting: Add capabilities for automated, scripted network testing, significantly increasing the tool’s versatility for security auditing.
Early versions were used for experimenting with advanced features like network scanning and system fingerprinting.
The stable version of Hping3 was officially released on November 5, 2005, and published under the GPLv2 license. Salvatore Sanfilippo is also the creator of the popular open-source project, Redis.
⚠︎ Disclaimer: Legal Use Only
Using Hping3 without proper authorization may be illegal and violate computer crime laws in your jurisdiction. Sending packets can disrupt services, cause outages, exhaust system resources, or result in data loss.
Always obtain written permission and clearly understand the scope, authorized targets, and permitted methods before testing any network or system.
The writer of this guide assumes no liability for any misuse, illegal activity, or damage resulting from the information provided.
Pre-Requisites
This guide assumes you’re already familiar with networking fundamentals and penetration testing basics. If you’re reading this, you should already know:
What You Need to Know
Networking basics: IP addressing, CIDR notation, TCP vs UDP, common ports, and how firewalls work.
Basic packet knowledge: Understanding packet structure and headers.
Command line: You can navigate terminals and run commands with sudo/admin privileges on your OS of choice.
How to Install Hping3:
Hping3 is primarily designed for Linux and is included in most Linux distributions like Kali, Debian, and Ubuntu.
Linux: Fully supported, can be installed via package managers (
apt install hping3) or compiled from source.Windows: Older versions of hping (like hping2) exist, but support is limited and development is mostly inactive. Hping3 does not have an official, fully functional Windows version.
macOS: Can be installed via Homebrew (
brew install hping) but may require additional permissions or compilation tweaks.
Linux (Recommended)
Hping3 is fully supported on Linux and comes pre‑installed on distros like Kali and Parrot. You can update or install it with:
sudo apt update && sudo apt install hping3Windows
Hping3 does not have a native, fully supported Windows version.
The recommended way to use it on Windows is through WSL (Windows Subsystem for Linux), which gives you full Linux functionality.
macOS
Hping3 can be installed on macOS using Homebrew:
brew install hpingVirtual Machines
You can also set up a virtual machine using a hypervisor such as VirtualBox, UTM, or Parallels (for Mac) and run a Linux distribution inside it.
This can be a preferable option if you don’t have access to a native Linux machine, providing full Linux functionality for using hping3.
Basic Command Structure
Hping3 uses a flexible, modular command format that lets you build simple or highly customized packets depending on your testing needs.
Command Syntax
The basic syntax defines how every hping3 command is structured. Hping3 commands are made up of three parts:
Mode: Specifies the protocol or operational mode hping3 should use.
Options: Modify packet behavior, headers, timing, and output.
Target: Defines the host or IP address you’re sending packets to.
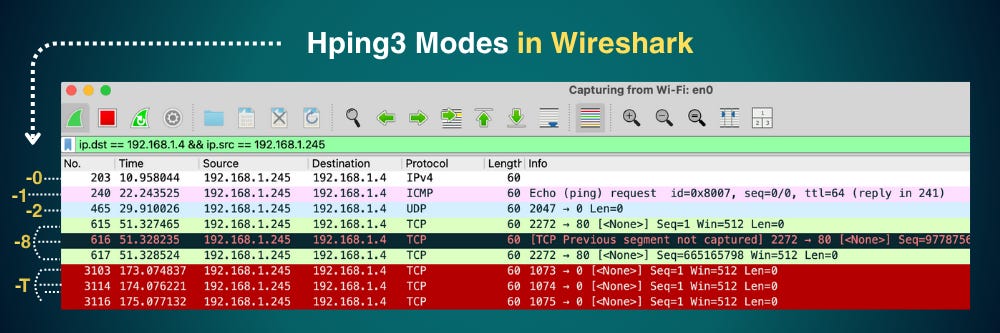
hping3 [mode] [options] targetLearning Tip: Hping3 + Wireshark
When you’re learning Hping3, it can be helpful to run commands on Nmap and watch how they translate to network traffic in Wireshark.
This lets you see exactly what packets Hping3 sends and how targets respond, making it easier to understand what each scan type and option actually does at the network level. Use Wireshark filters to view specific traffic:
# Wireshark Filter Cheat Sheet
# Show packets coming from a specific IP
ip.src == <receiver host ip>
# Show packets going to a specific IP
ip.dst == <sender host ip>
# Show all packets to or from a specific IP
ip.addr == <host ip>
# Combine filters with && for more specific traffic
ip.src == <source ip> && ip.dst == <destination ip>
# Filter by protocol
tcp
udp
icmp
arp
# Filter by port number
tcp.port == 80
udp.port == 53
# Combine protocol and IP filters
tcp && ip.addr == <host ip>Mode
Modes define what kind of packets hping3 sends and the overall behavior of the tool. Choose a mode based on the protocol or action you want to test.
These modes determine the network protocol or special operation hping3 will use when sending packets.
Default (TCP): Sends TCP packets for basic probing or flag‑based testing.
-0/--rawip: Lets you craft arbitrary IP packets when you need full control over protocol values.-1/--icmp: Sends ICMP packets for ping-like tests or diagnostic probing.-2/--udp: Sends UDP packets to test UDP services, firewalls, and filtering.-8/--scan: Performs manual port scanning when Nmap is blocked or filtered.-9/--listen: Listens for packets, useful for debugging or custom replies.-T/--traceroute: Maps the hop path to a target using TTL increments.
Default (TCP)
Sends standard TCP packets and is used automatically if no mode flag is given. It allows testing connectivity, flags, and basic TCP behavior. Useful for quick SYN, ACK, or custom flag‑based probing.
hping3 <target> -S -p 80-0 / --rawip
Crafts raw IP packets, giving full control over protocol fields. This mode is useful when you need to send packets belonging to uncommon or custom protocol numbers. It is mainly used for advanced testing where standard TCP/UDP/ICMP does not apply.
hping3 <target> -0 --ipproto 253-1 / --icmp
Sends ICMP packets similar to traditional ping. Useful for reachability checks, diagnostics, and network path behavior. Often used when ICMP must be tested specifically instead of TCP or UDP.
hping3 <target> -1-2 / --udp
Sends UDP packets to test UDP services or filtering behavior. Helpful for checking whether hosts respond with ICMP “port unreachable.” Useful for understanding how firewalls handle UDP traffic.
hping3 <target> -2 -p 12345-8 / --scan
Performs a manual TCP port scan on a target or range of targets.
This mode is useful when scanners such as Nmap are blocked or filtered.
The option expects a port group argument. Port groups use the following rules:
A single number scans one port
A range uses start-end format
all scans ports 0 through 65535
known scans all ports listed in /etc/services.
/etc/services is a system file found on Unix and Linux systems. It acts as a directory of well-known network services and the ports they use.Groups may be combined
Groups may be negated using !
The port group must appear immediately after the -8 flag
The port group must immediately follow the -8 flag. Most other hping3 options still work inside scan mode.
For example, you must specify -S to perform a SYN scan, and you can still modify TCP window size, TTL, IP fragmentation, and more. The only difference is that normal hping3 behavior is wrapped inside a scanning algorithm.
# Scan port 22 only (single port)
hping3 <target> -8 22
# Scan ports 1 through 1000 (range)
hping3 <target> -8 1-1000
# Scan all ports 0 through 65535 (all)
hping3 <target> -8 all
# Scan all ports defined in /etc/services (known)
hping3 <target> -8 known
# Scan ports 1 through 1000 plus port 8888 plus all known ports
hping3 <target> --scan 1-1000,8888,known -S target.host.com
# Scan all ports from 1 through 1024 except those listed in /etc/services
hping3 <target> --scan ‘1-1024,!known’ -S target.host.com-9 / --listen
Listens for packets that contain a specific signature string. Useful for debugging, custom signaling, or simple packet-trigger experiments. The tool waits passively until matching traffic arrives.
hping3 -9 MYTAG-T / --traceroute
Performs traceroute using TCP packets instead of ICMP. It increments TTL values to map network hops to the destination. Useful for bypassing filters that block regular traceroute probes.
hping3 <target> -T -p 80Options
Options modify packet headers, timing, or output for the selected mode and target. Some options work universally, others only in specific modes. Some options have both short and long forms.
In the following ”Core Functions for Ethical Hackers” section, we’ll go over how to combine these options for specific use cases.
Help & Version
# Command: -h or --help
Displays the complete usage guide with all available options and syntax for quick reference during testing without opening the manual page.
# Example(s)
hping3 -h
hping3 --help
# Command: -v or --version
Shows the current hping3 version number and data link layer type (Ethernet, PPP, etc.) for verifying compatibility and documenting tool versions in reports.
# Example(s)
hping3 -v
hping3 --versionPacket Sending Rate & Control
# Command: -c [count] or --count [count]
Sends exactly the specified number of packets then stops and displays summary statistics. Use for controlled scanning with precise packet counts, benchmarking firewall rules, measuring response rates, or limiting traffic to avoid detection.
# Example(s)
hping3 -c 10 192.168.1.1
hping3 --count 10 192.168.1.1
# Command: -i [interval] or --interval [interval]
Sets the time delay between consecutive packets. Accepts X for seconds, uX for microseconds (u500 = 500µs), or mX for milliseconds. Spaces out packets to evade rate-based intrusion detection systems and simulate realistic traffic patterns during reconnaissance.
# Example(s)
hping3 -i u500 192.168.1.1
hping3 -i 2 192.168.1.1
hping3 --interval u1000 192.168.1.1
# Command: --fast
Sends exactly 10 packets per second (100ms intervals). Provides moderate speed for SYN scans without triggering rate limiting or flood detection mechanisms.
# Example(s)
hping3 --fast 192.168.1.1
# Command: --faster
Increases speed to approximately 100 packets per second (~1ms intervals). Use for time-sensitive operations like latency measurements or rapid service enumeration where speed matters but full flooding would be counterproductive.
# Example(s)
hping3 --faster 192.168.1.1
# Command: --flood
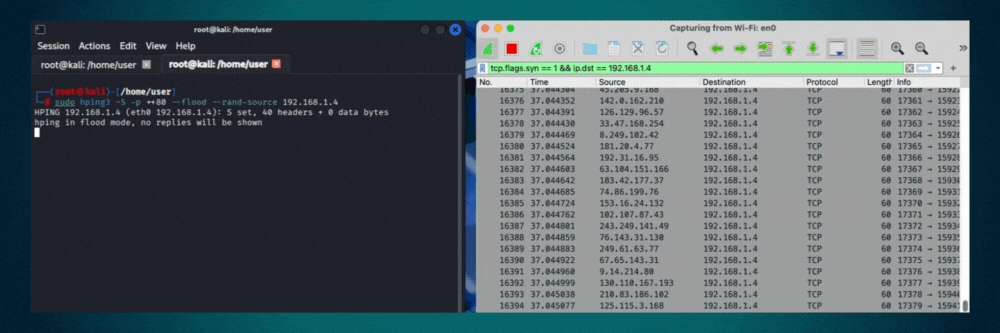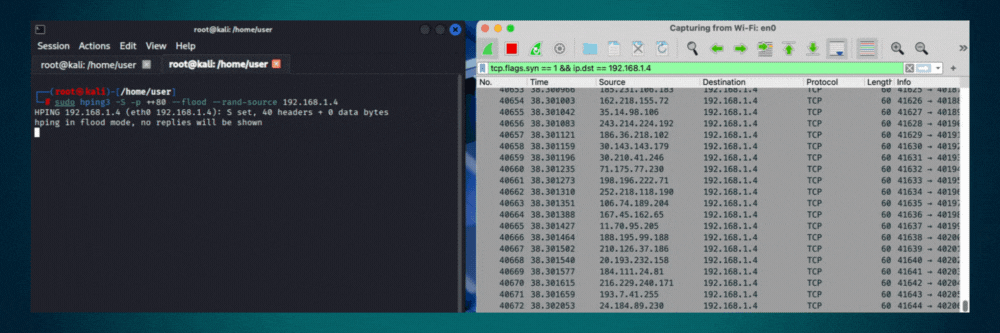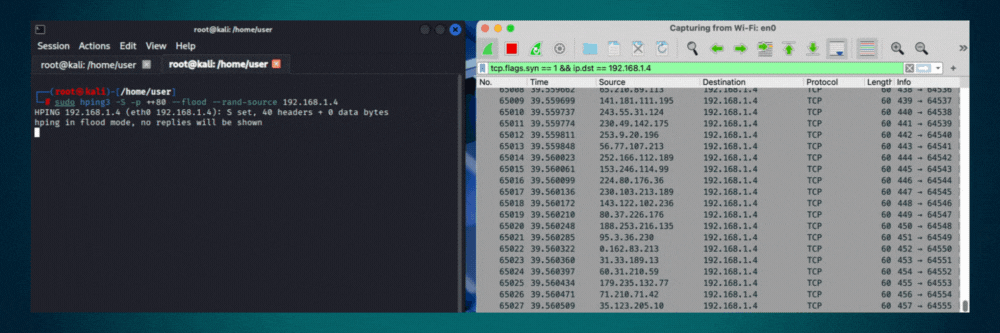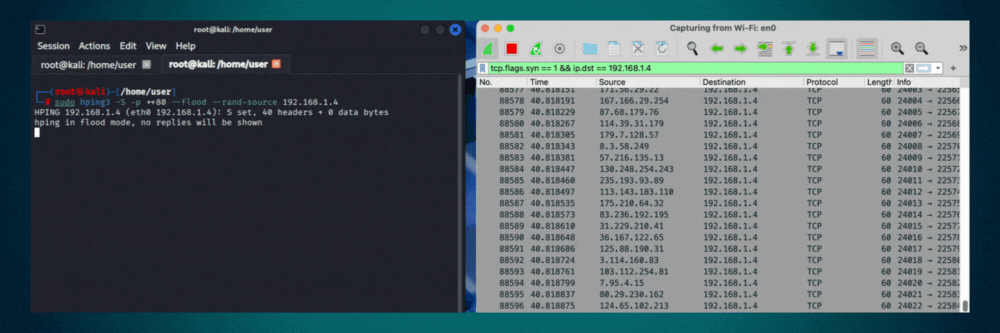
Transmits packets at maximum speed without waiting for replies or adding delays. Sends as fast as the network interface and system can process. Use for stress testing network devices, measuring maximum throughput, or authorized denial-of-service simulations in controlled environments.
# Example(s)
hping3 --flood 192.168.1.1Interface & Output Control
# Command: -I [interface name] or --interface [interface name]
Forces packet transmission through a specific network interface (eth0, wlan0, tun0). Critical for multi-homed systems to direct traffic through a particular path like VPN tunnels, specific network segments during internal assessments, or isolating test traffic from production.
# Example(s)
hping3 -I eth0 192.168.1.1
hping3 --interface wlan0 192.168.1.1
# Command: -n or --numeric
Disables reverse DNS lookups and displays all IP addresses numerically. Speeds up large network scans by eliminating DNS resolution overhead, prevents information leakage through DNS queries, and avoids timeout delays when scanning hosts without reverse DNS entries.
# Example(s)
hping3 -n 192.168.1.1
hping3 --numeric 192.168.1.1
# Command: -q or --quiet
Suppresses per-packet output and displays only initial parameters and final summary statistics. Keeps log files clean in automated scripts, reduces console clutter during long-running tests, and focuses on aggregate results.
# Example(s)
hping3 -q 192.168.1.1
hping3 --quiet 192.168.1.1
# Command: -V or --verbose
Shows comprehensive packet-level information including headers, flags, and timing for every packet sent and received. Use for deep packet inspection, analyzing protocol behavior, debugging unexpected responses, and developing packet-level exploits or evasion techniques.
# Example(s)
hping3 -V 192.168.1.1
hping3 --verbose 192.168.1.1
# Command: -D or --debug
Activates debug mode showing internal program state, function calls, and detailed error messages. Use for troubleshooting unexpected behavior, diagnosing custom packet configuration issues, or understanding why raw packet scenarios fail at the OS level.
# Example(s)
hping3 -D 192.168.1.1
hping3 --debug 192.168.1.1
# Command: -z or --bind
Binds CTRL+Z to dynamically adjust TTL values during execution. Allows interactive hop-by-hop traceroute adjustments in real-time without restarting the command or losing session state.
# Example(s)
hping3 -z 192.168.1.1
hping3 --bind 192.168.1.1
# Command: -Z or --unbind
Releases CTRL+Z binding and restores standard Unix signal behavior where CTRL+Z suspends the process. Use after interactive TTL sessions to return to normal terminal control.
# Example(s)
hping3 -Z 192.168.1.1
hping3 --unbind 192.168.1.1
# Command: --beep
Produces an audible beep for each received reply packet. Helpful for passive monitoring when you need audio alerts for arriving responses, particularly during long-running scans or when multitasking.
# Example(s)
hping3 --beep 192.168.1.1Source & Destination Address Control
# Command: -a [hostname] or --spoof [hostname]
Forges the source IP address in outgoing packets to appear as if they originated from the specified host. Use for testing anti-spoofing mechanisms, assessing ingress filtering effectiveness, conducting backscatter analysis by triggering responses to spoofed addresses, or testing firewall rules that trust certain source IPs.
# Example(s)
hping3 -a 10.0.0.5 192.168.1.1
hping3 --spoof 10.0.0.5 192.168.1.1
# Command: --rand-source
Generates a random source IP address for each packet, creating the appearance of distributed traffic from multiple origins. Use for simulating distributed denial-of-service scenarios in authorized tests, evading source-based blocking rules or rate limits, and making traffic correlation difficult for security devices.
# Example(s)
hping3 --rand-source 192.168.1.1
# Command: --rand-dest
Randomizes destination IP addresses according to specified rules, distributing packets across multiple targets. Use for broad network mapping without sequential predictability, fuzzing multiple endpoints simultaneously, or simulating scattered attack patterns to test network-wide detection.
# Example(s)
hping3 --rand-dest 192.168.1.xIP Header Options
# Command: -t [ttl] or --ttl [ttl]
Sets the IP Time To Live field (0-255), determining maximum router hops before packet discard. Each router decreases TTL by 1; packet drops when reaching 0. Use for traceroute operations, path MTU discovery, fingerprinting intermediate devices based on TTL behavior, and crafting packets that expire at specific network boundaries.
# Example(s)
hping3 -t 5 192.168.1.1
hping3 --ttl 64 192.168.1.1
# Command: -N [id] or --id [id]
Manually overrides the IP identification field with a specific value instead of automatic OS assignment. The IP ID identifies fragments of the same packet. Use for replay attacks with predictable ID values, evading security devices that correlate packets by ID sequence patterns, or testing whether IDS systems track IP fragmentation through ID matching.
# Example(s)
hping3 -N 12345 192.168.1.1
hping3 --id 12345 192.168.1.1
# Command: -H [protocol] or --ipproto [protocol]
Sets the IP protocol number in the IP header for RAW IP mode. Standard protocols use 6 for TCP, 17 for UDP, 1 for ICMP. Use for crafting packets with non-standard or uncommon protocols to test protocol-aware filters, assess firewall protocol handling, or probe for vulnerabilities in custom protocol parsers.
# Example(s)
hping3 -H 47 192.168.1.1
hping3 --ipproto 6 192.168.1.1
# Command: -W or --winid
Uses Windows-style byte ordering for the IP ID field (little-endian) instead of standard network byte order (big-endian). Aids OS fingerprinting evasion by making Linux-generated packets appear as Windows traffic, helping blend into predominantly Windows network environments.
# Example(s)
hping3 -W 192.168.1.1
hping3 --winid 192.168.1.1
# Command: -r or --rel
Displays IP ID field values as relative increments from the previous packet instead of absolute values. Use for detecting Network Address Translation (NAT) devices, identifying load balancers through ID sequence discontinuities, or fingerprinting how different systems increment IP ID counters during reconnaissance.
# Example(s)
hping3 -r 192.168.1.1
hping3 --rel 192.168.1.1
# Command: -o [hex_tos] or --tos [hex_tos]
Sets the IP Type of Service (ToS) or Differentiated Services (DiffServ) field using hexadecimal values. Use for testing Quality of Service policy enforcement, validating priority-based routing behavior, or verifying whether traffic classification and marking rules are correctly applied.
# Example(s)
hping3 -o 0x10 192.168.1.1
hping3 --tos 0x10 192.168.1.1
# Command: -G or --rroute
Enables the IP record route option, instructing routers to insert their IP addresses into the packet header. Captures and displays the actual route taken, revealing internal network topology in environments where routers honor this option (increasingly rare due to security concerns and performance overhead).
# Example(s)
hping3 -G 192.168.1.1
hping3 --rroute 192.168.1.1Fragmentation Options
# Command: -f or --frag
Forces packet fragmentation, splitting data across multiple IP fragments. Use for testing fragmentation handling in firewalls or IDS, probing for fragment reassembly vulnerabilities, or evading signature-based detection that only inspects individual fragments without reassembling streams.
# Example(s)
hping3 -f 192.168.1.1
hping3 --frag 192.168.1.1
# Command: -x or --morefrag
Sets the “more fragments” (MF) flag in the IP header, indicating additional fragments follow. Use for testing how security devices handle incomplete fragment streams, probing drop policies for fragments that never complete, or crafting malformed fragmentation sequences to test parser robustness.
# Example(s)
hping3 -x 192.168.1.1
hping3 --morefrag 192.168.1.1
# Command: -y or --dontfrag
Sets the “don’t fragment” (DF) bit in the IP header, instructing routers never to fragment the packet. If the packet exceeds link MTU, routers drop it and send back an ICMP message. Use for Path MTU Discovery (PMTUD) to find maximum packet size, identifying MTU black holes where oversized packets are silently dropped, or forcing specific packet sizes for exploit delivery.
# Example(s)
hping3 -y 192.168.1.1
hping3 --dontfrag 192.168.1.1
# Command: -g [offset] or --fragoff [offset]
Manually sets the fragment offset field, indicating where in the original packet this fragment belongs (measured in 8-byte blocks). Use for crafting overlapping fragments, out-of-order fragments, or malformed fragmentation patterns to bypass weak reassembly logic or test fragment handling edge cases.
# Example(s)
hping3 -g 100 192.168.1.1
hping3 --fragoff 100 192.168.1.1
# Command: -m [mtu] or --mtu [mtu]
Enforces a virtual Maximum Transmission Unit controlling fragment sizing. Makes hping3 fragment packets as if sent over a link with the specified MTU. Use for simulating small-MTU links for evasion testing or validating how applications and security devices handle various fragment sizes.
# Example(s)
hping3 -m 500 192.168.1.1
hping3 --mtu 1280 192.168.1.1ICMP-Specific Options
# Command: -C [type] or --icmptype [type]
Selects ICMP message type (0-255). Type 8 is echo request (standard ping), type 0 is echo reply, type 3 is destination unreachable, type 11 is time exceeded (traceroute). Use for custom ping sweeps, crafting specific ICMP messages to test firewall rules, or probing target responses to various ICMP types during reconnaissance.
# Example(s)
hping3 -C 8 192.168.1.1
hping3 --icmptype 13 192.168.1.1
# Command: -K [code] or --icmpcode [code]
Sets the ICMP code field providing additional detail for the selected type. Type 3 (destination unreachable) has code 0 for network unreachable, code 1 for host unreachable, code 3 for port unreachable. Use for precise ICMP message crafting to test granular firewall rules or simulate specific network error conditions.
# Example(s)
hping3 -C 3 -K 3 192.168.1.1
hping3 --icmptype 3 --icmpcode 1 192.168.1.1
# Command: --icmp-ipver [version]
Sets the IP version in the ICMP-embedded IP header. Use for manipulating the IP header embedded inside ICMP error messages to test how devices parse embedded headers or simulate error messages for protocols that don’t match the outer packet.
# Example(s)
hping3 --icmp-ipver 4 192.168.1.1
# Command: --icmp-iphlen [length]
Sets the IP header length in the ICMP-embedded header. Use for manipulating the IP header embedded inside ICMP error messages to test parser handling or conduct ICMP tunneling experiments.
# Example(s)
hping3 --icmp-iphlen 20 192.168.1.1
# Command: --icmp-iplen [length]
Sets the total IP packet length in the ICMP-embedded header. Use for manipulating the IP header embedded inside ICMP error messages to test how devices handle malformed embedded headers.
# Example(s)
hping3 --icmp-iplen 100 192.168.1.1
# Command: --icmp-ipid [id]
Sets the IP ID in the ICMP-embedded IP header. Use for manipulating the IP header embedded inside ICMP error messages or conducting ICMP tunneling experiments.
# Example(s)
hping3 --icmp-ipid 5000 192.168.1.1
# Command: --icmp-ipproto [protocol]
Sets the protocol field in the ICMP-embedded IP header. Use for simulating error messages for specific protocols or testing how devices parse embedded protocol fields.
# Example(s)
hping3 --icmp-ipproto 6 192.168.1.1
# Command: --icmp-cksum [checksum]
Forces a specific ICMP checksum value, including intentionally incorrect checksums. Use for testing whether targets validate ICMP checksums before processing, probing for vulnerabilities where hardware checksum offload bypasses validation, or identifying devices that accept malformed ICMP packets.
# Example(s)
hping3 --icmp-cksum 0xFFFF 192.168.1.1
# Command: --icmp-ts
Sends an ICMP timestamp request (type 13), asking the target to reply with its current system time. Use for gathering remote clock information to calculate clock skew for OS fingerprinting, detecting virtualized environments through timing anomalies, or exploiting timing side-channels in cryptographic implementations.
# Example(s)
hping3 --icmp-ts 192.168.1.1
# Command: --icmp-addr
Sends an ICMP address mask request (type 17), historically used to query a host’s subnet mask. Modern systems rarely respond. Use for mapping legacy network configurations, identifying old systems that honor deprecated ICMP types, or discovering older infrastructure during reconnaissance.
# Example(s)
hping3 --icmp-addr 192.168.1.1TCP/UDP Port Options
# Command: -s [port] or --baseport [port]
Sets or fixes the source port number for outgoing packets. Use for maintaining consistent source ports across packets to preserve stateful firewall sessions, spoofing trusted source ports (53 for DNS, 20 for FTP-DATA) to bypass poorly configured access controls, or setting a specific starting port for sequential scanning.
# Example(s)
hping3 -s 53 192.168.1.1
hping3 --baseport 8080 192.168.1.1
# Command: -p[+][+] [port]
Sets destination port with optional auto-increment. -p 80 targets port 80 only, -p+ 80 increments per packet (80, 81, 82...), -p++ 80 increments per cycle. Use for automating sequential port scanning across ranges, testing versioned services on consecutive ports, or efficiently checking service availability across port spaces.
# Example(s)
hping3 -p 80 192.168.1.1
hping3 -p+ 80 192.168.1.1
hping3 -p++ 8000 192.168.1.1
# Command: --keep
Locks the source port to a constant value instead of incrementing or changing. Use for stateful firewall testing where maintaining the same source address-port tuple is required for return traffic, or testing whether security devices properly track connection state based on consistent port pairs.
# Example(s)
hping3 --keep 192.168.1.1TCP Header Options
# Command: -w [size] or --win [size]
Sets the TCP window size field advertising receive buffer capacity. Use for probing window scaling implementation issues, triggering specific receiver behaviors based on window advertisements, testing how applications handle zero-window or unusually large/small window values, or fingerprinting TCP stack implementations.
# Example(s)
hping3 -w 65535 192.168.1.1
hping3 --win 0 192.168.1.1
# Command: -O [offset] or --tcpoff [offset]
Sets the TCP data offset (header length), including values that don’t match actual header size. Use for crafting malformed TCP headers to test parser robustness, probing whether security devices validate header length fields, or attempting to bypass inspection by claiming headers extend beyond actual boundaries.
# Example(s)
hping3 -O 10 192.168.1.1
hping3 --tcpoff 15 192.168.1.1
# Command: -M [number] or --setseq [number]
Sets the TCP sequence number to a specific value instead of random or automatic values. Use for TCP session hijacking simulations by predicting or replaying sequence numbers, conducting replay attacks using captured sequence values, or testing whether applications validate sequence number progression.
# Example(s)
hping3 -M 1000000 192.168.1.1
hping3 --setseq 500000 192.168.1.1
# Command: -L [number] or --setack [number]
Sets the TCP acknowledgment number to a specific value. Use for simulating acknowledgment of unsent data, enabling session hijacking by crafting ACK packets that appear part of existing connections, or testing how applications handle out-of-sequence acknowledgments or malformed ACK values.
# Example(s)
hping3 -L 2000000 192.168.1.1
hping3 --setack 100000 192.168.1.1
# Command: -Q or --seqnum
Displays TCP sequence numbers extracted from received reply packets. Use for mapping Initial Sequence Number (ISN) generation patterns for prediction attacks, analyzing sequence number randomness to assess TCP stack security, or tracking sequence progression to understand connection state during exploitation.
# Example(s)
hping3 -Q 192.168.1.1
hping3 --seqnum 192.168.1.1
# Command: -b or --badcksum
Intentionally sends packets with incorrect TCP or UDP checksums. Use for verifying whether endpoints validate checksums or blindly trust them, detecting checksum offload configurations where network cards calculate checksums in hardware, or identifying middleboxes that modify packets without recalculating checksums.
# Example(s)
hping3 -b 192.168.1.1
hping3 --badcksum 192.168.1.1
# Command: --tcp-timestamp
Enables TCP timestamp options and analyzes returned timestamps to estimate remote system uptime. Use for calculating how long a system has been running based on timestamp counter values, detecting virtualized or containerized hosts through timestamp behavior anomalies, or identifying load balancers by comparing timestamp values across connections.
# Example(s)
hping3 --tcp-timestamp 192.168.1.1TCP Flag Options
# Command: -F or --fin
Sets the FIN (finish) flag signaling connection termination. Use in FIN scans to enumerate ports by observing how closed ports respond with RST while open ports may ignore or respond differently, or for testing stateful firewall behavior.
# Example(s)
hping3 -F 192.168.1.1
hping3 --fin 192.168.1.1
# Command: -S or --syn
Sets the SYN (synchronize) flag initiating TCP connection establishment. Use for SYN scanning to identify open ports through three-way handshake responses, or testing SYN flood protections by observing how systems handle connection requests.
# Example(s)
hping3 -S 192.168.1.1
hping3 --syn 192.168.1.1
# Command: -R or --rst
Sets the RST (reset) flag abruptly terminating connections. Use for testing how applications handle unexpected connection resets, probing for state table manipulation opportunities, or generating reset packets to interfere with existing connections in authorized testing.
# Example(s)
hping3 -R 192.168.1.1
hping3 --rst 192.168.1.1
# Command: -P or --push
Sets the PUSH flag requesting immediate data delivery to the application. Use for testing whether applications respond differently to pushed data, probing protocol timing behaviors, or ensuring data isn’t buffered during time-sensitive operations.
# Example(s)
hping3 -P 192.168.1.1
hping3 --push 192.168.1.1
# Command: -A or --ack
Sets the ACK (acknowledgment) flag indicating data receipt. Use in ACK scans to map firewall rulesets based on how stateful firewalls handle unsolicited ACK packets, or testing whether systems track connection state properly.
# Example(s)
hping3 -A 192.168.1.1
hping3 --ack 192.168.1.1
# Command: -U or --urg
Sets the URG (urgent) flag marking data as high-priority. Use for testing urgent pointer handling, probing for vulnerabilities in urgent data processing, or verifying whether applications properly implement TCP urgent mode.
# Example(s)
hping3 -U 192.168.1.1
hping3 --urg 192.168.1.1
# Command: -X or --xmas
Sets FIN, URG, and PUSH flags simultaneously, creating an “Xmas tree” packet. Use for identifying non-RFC-compliant TCP stacks that respond to invalid flag combinations, fingerprinting operating systems based on how they handle malformed packets, or evading detection systems that don’t expect unusual flag patterns.
# Example(s)
hping3 -X 192.168.1.1
hping3 --xmas 192.168.1.1
# Command: -Y or --ymas
Sets an invalid combination of SYN, FIN, and RST flags simultaneously. Use for stressing TCP state machines with contradictory instructions, testing parser robustness against malformed packets, probing for crash conditions or reset bugs in poorly implemented TCP stacks, or bypassing simple packet filters that only check individual flags.
# Example(s)
hping3 -Y 192.168.1.1
hping3 --ymas 192.168.1.1Payload & Data Options
# Command: -d [size] or --data [size]
Sets payload size in bytes, padding with zeros if no data specified. Use for testing buffer handling by sending specific payload lengths, probing for buffer overflow vulnerabilities in fixed-size buffers, validating MTU-related behaviors, or ensuring packets reach minimum size requirements.
# Example(s)
hping3 -d 100 192.168.1.1
hping3 --data 1400 192.168.1.1
# Command: -E [filename] or --file [filename]
Reads packet payload data from the specified file. Use for covert channel data exfiltration proofs-of-concept by encoding data in packets, enabling protocol fuzzing with specific malformed payloads, or delivering exploit shellcode embedded in packet data fields.
# Example(s)
hping3 -E payload.txt 192.168.1.1
hping3 --file data.bin 192.168.1.1
# Command: -e [signature] or --sign [signature]
Appends an identifiable signature string to packet payload. Use for marking packets for later correlation when using multiple scanning tools, identifying which packets in captured traffic belong to specific test campaigns, or embedding metadata for tracking packet flows through complex network paths.
# Example(s)
hping3 -e “TEST123” 192.168.1.1
hping3 --sign “SCANID-456” 192.168.1.1Output & Packet Display
# Command: -j or --dump
Displays received packets in raw hexadecimal format showing all bytes. Use for forensic analysis of packet contents, manual protocol reverse engineering, identifying hidden data or covert channels in responses, or debugging exact byte-level protocol behaviors during exploit development.
# Example(s)
hping3 -j 192.168.1.1
hping3 --dump 192.168.1.1
# Command: -J or --print
Filters packet display to show only printable ASCII characters, suppressing binary data. Use for cleaning up output when extracting text-based data from responses, making banner grabbing more readable, or quickly identifying human-readable content embedded in packet payloads.
# Example(s)
hping3 -J 192.168.1.1
hping3 --print 192.168.1.1
# Command: --tcpexitcode
Sets program exit code to match the last received TCP flag value. Use for enabling shell scripting conditionals based on scan results, automating decision-making in scanning workflows by testing exit codes, or chaining hping3 with other tools that react based on whether ports are open (SYN-ACK) or closed (RST).
# Example(s)
hping3 --tcpexitcode 192.168.1.1File Transfer & Channel Protocol
# Command: -B or --safe
Enables reliable protocol with ACK-based acknowledgments and automatic retransmissions. Use for transforming hping3 into a basic file transfer tool with reliability guarantees, implementing covert channels that reliably exfiltrate data over unusual protocols, or demonstrating proof-of-concept protocol tunneling through restricted networks.
# Example(s)
hping3 -B 192.168.1.1
hping3 --safe 192.168.1.1
# Command: -u or --end
Signals end of file transfer session and stops accepting further data. Use for cleanly terminating safe-mode transfers ensuring all data is acknowledged, preventing hanging connections after transfer completion, or triggering receiver-side processing once transmission is confirmed complete.
# Example(s)
hping3 -u 192.168.1.1
hping3 --end 192.168.1.1Traceroute Mode Options
# Command: -T or --traceroute
Performs network path tracing by systematically incrementing TTL with each packet. First packet has TTL 1 and expires at first router, which sends back ICMP time exceeded revealing its IP address. Second packet has TTL 2 and reaches second router before expiring. Use for mapping network topology hop-by-hop, identifying routing paths and intermediate devices, discovering network boundaries and filtering points, or tracing packet traversal through multiple routers.
# Example(s)
hping3 -T 192.168.1.1
hping3 --traceroute 192.168.1.1
# Command: --tr-keep-ttl
Fixes TTL to repeatedly probe a single hop instead of incrementing. Use for diagnosing asymmetric routing by observing consistent behaviors at one hop, testing rate limiting or filtering at specific network points, or focusing analysis on a particular intermediate device’s responses.
# Example(s)
hping3 --tr-keep-ttl 192.168.1.1
# Command: --tr-stop
Halts traceroute after receiving the first non-ICMP time exceeded reply (typically when reaching destination). Use for focusing traceroute on finding the path without excess probing, reducing unnecessary traffic once the target responds, or quickly determining whether a host is reachable.
# Example(s)
hping3 --tr-stop 192.168.1.1
# Command: --tr-no-rtt
Disables round-trip time display in traceroute output, showing only hop IP addresses without timing information. Use for reducing output clutter during high-volume path recordings, simplifying parsing when only topology matters, or focusing on route enumeration without performance analysis.
# Example(s)
hping3 --tr-no-rtt 192.168.1.1Target
The target specifies the host or IP address that hping3 will send packets to. It can be a domain, IPv4, IPv6, or even a broadcast/multicast address when appropriate.
All packet crafting, flags, and options operate toward this destination.
Domain Name – Uses a hostname that hping3 resolves to an IP. Useful for public or dynamically assigned hosts. Behaves the same as the resolved IP.
IPv4 Address – Targets a host directly using its IPv4 address. Avoids DNS resolution and gives precise packet delivery. Ideal for internal or static hosts.
IPv6 Address – Targets a host using an IPv6 address. Requires IPv6 networking and the
-6flag. Useful for testing IPv6 routing or firewalls.
Domain Name
Uses a hostname that hping3 resolves to an IP address.
Useful for testing public services or any system with DNS records. Behaves the same as targeting the resolved IP.
hping3 example.com -S -p 80IPv4 Address
Targets a host directly using its IPv4 address. Avoids DNS resolution and is ideal for internal or static hosts. Provides exact, predictable packet delivery.
hping3 192.168.1.10 -S -p 80IPv6 Address
Targets a host using an IPv6 address. Requires -6 flag to force IPv6 mode. Useful in dual‑stack or IPv6‑only networks for testing routing or firewall behavior.
hping3 -6 2001:db8::1 -S -p 80Use Cases for Ethical Hackers:
Hping3’s ability to craft and send custom packets with precise control makes it valuable across multiple IT and security scenarios.
Network administrators use it to troubleshoot routing issues, test firewall configurations, measure latency and performance, verify Quality of Service policies, and diagnose connectivity problems.
Security teams rely on it to validate security device configurations, test defense mechanisms, verify policy enforcement, and simulate various attack patterns in controlled environments.
For ethical hackers, it’s a useful tool for reconnaissance, security testing, and identifying vulnerabilities that automated scanners often miss. The core use cases of hping3 for ethical hackers are outlined below.
Craft Custom Packets
Building custom packets gives you complete control over headers, flags, timing, and payload content. This precision is critical when standard tools can’t generate the exact traffic patterns needed for specialized testing.
Protocol Testing Test non-standard protocols like GRE, IPsec, and SCTP that automated scanners don’t support by crafting raw IP packets with specific protocol numbers.
Vulnerability Discovery Fuzz applications by sending malformed packets with invalid checksums, unusual TCP offsets, or invalid flag combinations to trigger edge cases in application logic.
Exploit Development Deliver precise payloads with specific sizes and timing to test buffer overflows, measure response timing for timing attacks, and set specific TCP sequence numbers.
Evasion Testing Bypass security controls using fragmentation, spoofed source addresses, unusual TTL values, and unexpected TCP flag combinations.
IDS/IPS Validation Test whether security monitoring detects known exploit patterns, fragmented attack traffic, spoofed addresses, and unusual protocol usage.
Stack Fingerprinting Identify remote operating systems by analyzing how different TCP/IP implementations respond to packets with specific characteristics.
# Test raw IP protocols (GRE, IPsec, SCTP)
hping3 -0 -H 47 target.com
# Fuzz with malformed packets using bad checksums
hping3 -S -p 80 -b target.com
# Deliver custom exploit payloads
hping3 -S -p 80 -E payload.bin -d 5000 target.com
# Test fragmentation handling
hping3 -S -p 80 -d 10000 -f target.comProbe Hosts and Ports
Manual probing provides granular control when automated scanners are too noisy or trigger security alerts. Unlike tools that follow predefined patterns, hping3 lets you craft individual probes with precise characteristics.
Stealth Scanning Control scan timing and packet construction to stay below IDS thresholds using microsecond-level timing control and unusual flag combinations.
Firewall Mapping Test how stateful firewalls respond differently to SYN packets versus ACK packets to map filtering rules without completing three-way handshakes.
Rule Enumeration Systematically test different flag combinations, ports, and protocols to build a complete picture of firewall policies.
Service Fingerprinting Discover services that respond only to specific protocols, source ports, packet flags, or payload content.
Rate Limit Bypass Space probes to stay under detection thresholds while maintaining scan progress by monitoring response patterns and adjusting timing.
Honeypot Detection Identify deception systems by analyzing response characteristics, timing patterns, and TCP/IP stack behavior.
# Stealth SYN scan with slow timing
hping3 -S --scan 1-1000 -i u100000 target.com
# ACK scan to map firewall stateful rules
hping3 -A --scan 1-1000 target.com
# NULL scan for firewall evasion
hping3 --scan 1-1000 target.com
# UDP service discovery
hping3 -2 -p 53,123,161 target.comTest Firewalls and IDS/IPS
Testing security devices validates whether firewalls enforce intended policies and IDS/IPS systems detect sophisticated attack patterns. Understanding device responses reveals misconfigurations and detection gaps.
Evasion Technique Testing Use fragmentation, unusual flag combinations (Xmas, NULL, FIN), and timing manipulation to test whether security devices properly inspect and reassemble traffic.
Anti-Spoofing Validation Verify that ingress and egress filtering prevents source address spoofing by sending packets with spoofed IPs from different network locations.
Deep Packet Inspection Test whether devices examine packet contents beyond headers by sending fragmented packets with payloads split across fragments.
Service Impersonation Manipulate source ports to appear as legitimate services like DNS (port 53) or HTTP (port 80) to test firewall rule configurations.
Blind Spot Identification Systematically probe with different protocols, ports, and flag combinations to find gaps in security monitoring coverage.
Validation Bypass Test inspection depth by sending packets with incorrect checksums, invalid sequence numbers, impossible flag combinations, and malformed options.
# Xmas scan to test IDS detection
hping3 -F -P -U --scan 1-1000 target.com
# Fragmentation to evade deep packet inspection
hping3 -S -p 80 -f -c 10 target.com
# Source port spoofing to impersonate DNS
hping3 -S -p 80 -s 53 -k target.com
# NULL scan with timing evasion
hping3 --scan 1-1000 -i u50000 target.comTraffic and Denial of Service Simulation
Simulating attack traffic in authorized environments tests system resilience, validates DDoS mitigation controls, identifies breaking points, and measures incident response effectiveness.
SYN Flood Testing Generate half-open connections by sending SYN packets without completing handshakes to exhaust server connection tables and test stateful firewall resilience.
Amplification Attack Simulation Test UDP services for reflection and amplification vulnerabilities by sending small requests with spoofed source addresses that generate large responses.
Connection Exhaustion Test connection limits by creating thousands of connections with varying source ports to identify at what point systems start rejecting new connections.
Resource Consumption Send large or fragmented packets to identify which resources (CPU, memory, bandwidth, connection tables) fail first under load.
Rate Limit Detection Gradually increase traffic rates from slow to fast while monitoring responses to find exact thresholds where systems start dropping packets or triggering defenses.
Distributed Simulation Use random source IPs to mimic multi-source DDoS attacks and test whether mitigation systems can handle distributed attack patterns.
# Gradual rate increase to find breaking points
hping3 -S -p 80 --fast -c 1000 target.com
hping3 -S -p 80 --faster -c 1000 target.com
# SYN flood test (authorized environments only)
hping3 -S -p 80 --flood --rand-source target.com
# Connection exhaustion with incrementing source ports
hping3 -S -p 80 -s ++1 --faster -c 10000 target.com
# Large packet resource consumption test
hping3 -S -p 80 -d 65000 --faster -c 1000 target.comHping3 is a complex tool that can be used for a variety of unique situations. I highly recommend trying out as many commands as you can, and trying to find a couple use cases to emulate using the commands from this guide.
Mastering packets enables you to understand network behavior at the deepest level, identify security gaps that automated tools miss, and test defenses with the precision.
Happy Hacking!