WiFi Password Cracking with Hashcat and Aircrack-ng on Kali Linux
WiFi cracking involves capturing a hashed version of a WiFi password, then using a tool that will cycle through a list of words hashing each of them and checking the result to see if it matches the hashed WiFi password’s hash.
If you don’t know what hashing is, here’s a simple example:
Password you don't know: password3
Hash from that password, which you do know: b61f66aecae3165af130b360cfa4152ff885269a8a11ebca17f8e50befd4dd82
In password cracking, you would brute force the answer by hashing every possible password combination, and checking the resulting hash for each against the hash you have.
If you find a matching hash, that means the password being hashed must be the same as the password you are cracking! You might check:
password1 —> d7bb81c5451c6101b643cd90394b281742a90703a854af26a11e5a5846c51e38
(no match)
password2 —> a6ef9c3c42396c3385dccbf81ee215bd7e7546d9c74faf4e3745ab0eaf2616ad
(no match)
password3—> b61f66aecae3165af130b360cfa4152ff885269a8a11ebca17f8e50befd4dd82
(match found!)As you can see, the third version matches the hash, so we have guessed the password correctly. This works well if the password is extremely simple, but with over 170,000 words in the English dictionary, as well as multi-word and word-number combination or combinations the two as options, you can see how the number of potential passwords grows exponentially.
The Process: Identifying Patterns and Building Wordlists
The first step in WiFi password cracking is to determine whether the network is using a default configuration or a customized setup.
This helps us predict the most likely password patterns and avoid wasting time on irrelevant guesses. Based on this, we either precompute a wordlist using known patterns or build a custom pattern-based wordlist using information about the target.
1. Is it a Default WiFi Network Name?
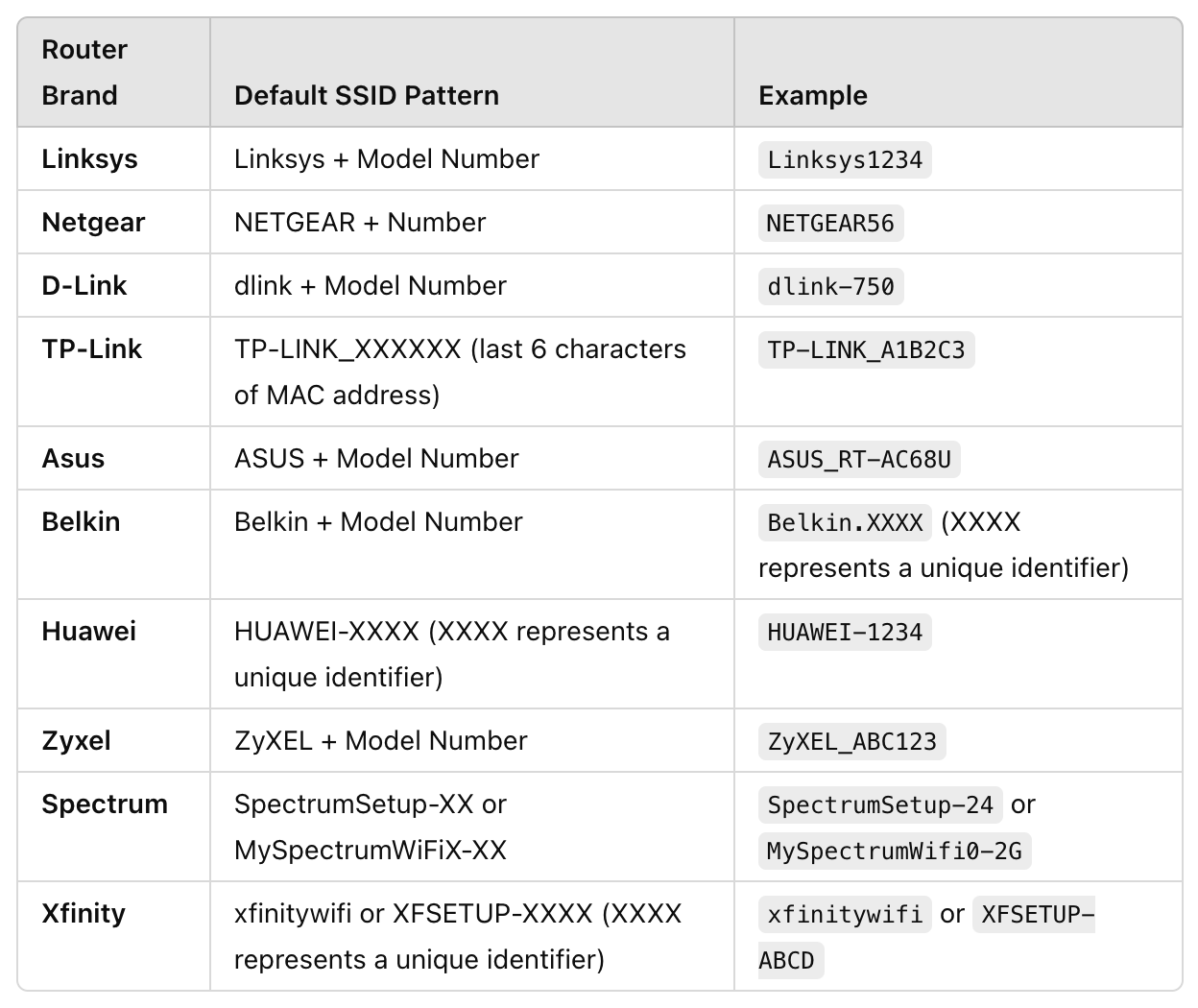
If the WiFi network name (SSID) is still the default assigned by the manufacturer, there’s a high chance that the password also follows a default pattern. Router manufacturers often assign predictable default SSIDs and passwords based on the router’s brand and model.
In these cases, you can:
Use prebuilt wordlists for known default passwords.
Precompute a wordlist based on the expected password pattern, like combining adjectives, nouns, and numbers as shown in our example.
By following these predictable patterns, you can significantly reduce the time needed to crack the password.
2. Is the WiFi Network Name Customized?
If the network name has been changed, the password is more likely to be personalized. In this case, we gather as much relevant information as possible to create a target-specific wordlist.
For Home WiFi:
Collect personal information about the user to generate a targeted wordlist:Social media profiles
Data breaches for plaintext passwords, emails, or phone numbers
Common patterns like family member names, pets, birthdates, or favorite teams
For Business WiFi:
Business networks often follow predictable patterns based on company details:The company’s social media profiles and website
Keywords related to the business or industry
Common patterns like office locations, department names, slogans, or founding years
Router manufacturers often assign default Wi-Fi network names, known as Service Set Identifiers (SSIDs), that follow specific patterns based on the router brand and model. These patterns can provide valuable clues about the likely password structure. If the SSID has not been changed, there’s a strong chance that the Wi-Fi password still follows the default format set by the manufacturer.
For example, some manufacturers use part of the router’s serial number in the SSID, while others follow a simple alphanumeric pattern (Netgear123, Linksys456).
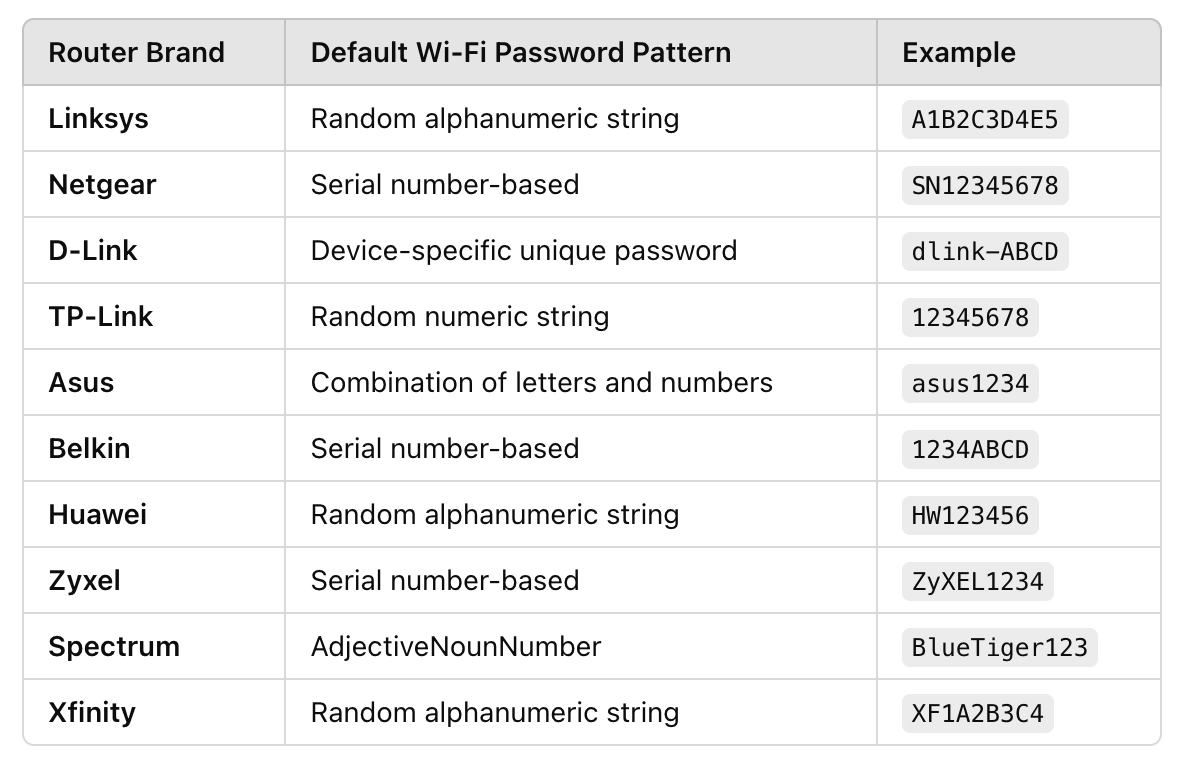
Router manufacturers also assign default passwords that follow specific patterns. These passwords often include combinations of letters and numbers unique to the router, but they can be predictable once the manufacturer’s pattern is known.
What if the user isn’t using the default WiFi password?
1. Start with a Generic Wordlist
When users create their own Wi-Fi passwords, they often choose simple and memorable combinations. These passwords tend to follow predictable patterns, based on common personal or business details.
Wordlists: https://github.com/taikuukaits/SimpleWordlists
2. Use AI to generate a wordlist based on the user’s information.
Artificial intelligence can help you generate a custom wordlist by analyzing information about the target. By gathering personal or business-related data, you can create a wordlist that reflects likely password choices. Here’s what to look for:
For Personal Wi-Fi Passwords:
Users often personalize their passwords by incorporating elements that are meaningful to them. These choices might seem random to others but follow predictable patterns.
Names: Using one's own name, family members' names, or pets' names (e.g., JohnSmith, Bella2025).
Birthdates or Anniversaries: Combining significant dates with names or words (e.g., Emma1990, Anniversary06/15).
Favorite Teams or Bands: Incorporating the names of favorite sports teams or musical groups (e.g., LakersFan, Beatles4Ever).
Common Words or Phrases: Using simple, memorable words or phrases (e.g., HomeSweetHome, LetMeIn).
Addresses: Using house numbers, street names, or zip codes (e.g., 123MainSt, Apt42B).
Phone Numbers: Using personal or familiar phone numbers, often in partial formats (e.g., 5551234, 818-555-6789).
For Business Wi-Fi Passwords:
When businesses set custom Wi-Fi passwords, they often choose details that are easy for employees to remember. Unfortunately, these choices can also make passwords easier to guess. Common business-related Wi-Fi password choices include:
Company Name: Using the business name or a variation of it (e.g., AcmeCorp2024, BestCafeWiFi).
Office Address: Including the street number, name, or suite number (e.g., 123MainStWiFi, Suite500Net).
Phone Number: Incorporating the company’s contact number (e.g., for number (555) 123-1234: 5551231234 555WiFi).
Slogans or Taglines: Using a well-known company motto (e.g., JustDoIt123, QualityMatters!).
Industry Keywords: Including terms related to the business (e.g., TechSupport99, AutoFix2024).
Founding Year or Anniversary: Referencing the company’s establishment date (e.g., Since1998, 25YearsStrong).
Department-Based Passwords: Different passwords for various departments (e.g., SalesWiFi2024, HRnetwork42).
Wi-Fi Related Words: Using generic terms for public/business Wi-Fi (e.g., FreeGuestWiFi, OfficeNet123).
Employee or Owner Names: Referencing key people in the company (e.g., JSmithOfficeWiFi, CEO1234).
Businesses that use predictable passwords risk unauthorized access, especially if the Wi-Fi is publicly available.
To use generative AI like ChatGPT, Claude, or DeepSeek, try copying / pasting all the data from a target’s profile (LinkedIn, Website, Facebook page, etc) and use a prompt like this to generate words:
"Given the text below, extract single words that are relevant and could be used in combination to form a password. Focus on names, dates, locations, keywords, and unique phrases. Return each word as a single entry on a new line without combining them."Example for Personal WiFi:
Input (Social Media Content)
"Hi, I'm John Smith. I live in Los Angeles with my dog Bella. I'm a huge fan of the Lakers and love music from The Beatles. My birthday is June 15, 1990."
Generated Wordlist:
John
Smith
Bella
Lakers
Beatles
June
June15
61590
615
1990
Los AngelesExample for Business WiFi:
Input (Website Content)
"Welcome to Acme Corp, established in 1998 located at 123 Main Street in New York City, NY. We specialize in tech support and custom IT solutions for small businesses. Contact us at 555-123-4567."
Generated Wordlist:
Acme
Corp
Tech
Support
Custom
IT
Solutions
Small
Business
New York
NYC
123
Main
Main Street
1998
5551234567
555
123
4567Once you have this single-word wordlist, you can combine them using Hashcat’s combination feature to generate multi-word password candidates (e.g., Acme1998, JohnBella, Lakers15).
Capturing a Hashed Wi-Fi Password
To capture a hashed Wi-Fi password, you need to intercept the 4-way handshake that occurs when a device connects to a WPA/WPA2-protected network. This guide walks through the entire process, step by step.
Understanding the 4-Way Handshake
When a device connects to a WPA2 Wi-Fi network, it undergoes a 4-way handshake to establish a secure connection. This process involves exchanging encrypted authentication data, which can be captured and later cracked.
Here’s what happens in each step of the handshake:
Client sends an authentication request to the access point (AP).
AP responds with an authentication challenge, which contains a nonce (random number).
Client generates a hash using the Wi-Fi password (PSK), nonce, and SSID (Wi-Fi network name) and sends a response.
AP verifies the response, and if it matches, both sides generate a Pairwise Master Key (PMK) to encrypt traffic.
Why Capture the Handshake?
The handshake contains a hashed version of the Wi-Fi password.
Hashing is a process that cannot be reversed, but it can be brute-forced or cracked using a dictionary attack, as described earlier.
Requirements: What You’ll Need
To successfully crack a WiFi password, you’ll need both the right hardware and software tools. Here’s a breakdown of what’s required:
Hardware
A Wi-Fi adapter that supports monitor mode and packet injection is essential. Not all adapters have this capability, so choosing the right one is critical. Below are some of the best options:
Recommended models:
Alfa AWUS036NHA (Best for Kali Linux)
TP-Link TL-WN722N v1 (Not v2/v3)
Panda PAU09 (Dual-band support)
Software Requirements:
Kali Linux is a popular Linux distribution designed specifically for penetration testing and ethical hacking. It comes with Aircrack-ng and many other security tools pre-installed. If you’re not using Kali, make sure your Linux distribution supports the necessary tools.
Aircrack-ng Suite: The Aircrack-ng suite is a powerful set of tools for Wi-Fi network security assessments. It focuses on monitoring, capturing, and cracking WPA/WPA2 encryption. The key tools in the suite include:
airmon-ng – Enables monitor mode on your wireless adapter, allowing it to capture packets from any network within range.
airodump-ng – Captures raw packets from Wi-Fi networks and collects handshake data for cracking.
aireplay-ng – Performs packet injection for deauthentication and replay attacks, useful for forcing devices to reconnect to capture handshakes.
aircrack-ng – The main tool used for cracking WPA/WPA2 passwords. It uses captured handshake files and a dictionary attack to guess the password.
Hashcat - Hashcat is a high-performance password cracking tool. We’ll use Hashcat to brute-force the WiFi password using the captured handshake, allowing for advanced password combinations and masks.
Hxctools - The hcxtools suite converts captured handshake files into a format compatible with Hashcat (.cap to .22000 format). This is a necessary step before using Hashcat for password cracking.
Dictionary Files: Dictionary files contain potential passwords for a dictionary attack. Hashcat hashes each word from the file and compares it to the captured handshake. Custom wordlists based on target-specific information can significantly improve accuracy.
How to Capture the Password
1. Disable Conflicting Processes
Before enabling monitor mode, you need to stop certain background processes that might interfere with your Wi-Fi adapter.
What Are These Conflicting Processes?
Your operating system automatically manages Wi-Fi connections, which can disrupt monitor mode.
NetworkManager and wpa_supplicant actively control your network card and must be disabled.
How to Disable Them?
Run the following command:
airmon-ng check killThis will stop:
NetworkManager (which automatically connects/disconnects from Wi-Fi)
wpa_supplicant (which handles authentication)
💡 Tip: After finishing your capture, you can restart these processes to restore normal Wi-Fi functionality:
1. Stop Monitor Mode:
sudo airmon-ng stop wlan0monExplanation:
This command stops monitor mode on your wireless interface (
wlan0mon).Why? When you switch your wireless interface to monitor mode (used for capturing packets), it cannot connect to Wi-Fi networks. This step restores it back to managed mode, which is required for normal network connections.
2. Bring the Interface Back Up:
sudo ip link set wlan0 upExplanation:
This command activates your network interface (
wlan0) if it’s in a DOWN state.Why? After stopping monitor mode, the interface might be disabled. This ensures it’s up and ready to connect to Wi-Fi networks.
3. Restart the Network Manager:
sudo systemctl restart NetworkManagerExplanation:
This command restarts the NetworkManager service, which is responsible for managing network connections in Linux.
Why? When you run
airmon-ng check kill, it stops several services, including NetworkManager, to prevent interference with monitor mode. Restarting it restores all normal network functionality and reconnects you to Wi-Fi automatically.
2. Enable Monitor Mode
Now that conflicting processes are disabled, enable monitor mode on your Wi-Fi adapter.
What Is Monitor Mode?
By default, your Wi-Fi adapter only sees packets meant for your computer.
Monitor mode allows your adapter to capture all network traffic, including handshake packets.
How to Check Available Wi-Fi Adapters?
Run:
airmon-ngThis will list your network interfaces, something like:
Interface Chipset Driver
wlan0 Atheros ath9kHere, wlan0 is the Wi-Fi interface name.
Enable Monitor Mode
Run:
airmon-ng start wlan0If successful, it will create a new interface, such as wlan0mon.
Confirm Monitor Mode is Active
Check the Wi-Fi mode using:
iwconfigYou should see:
wlan0mon IEEE 802.11 Mode:Monitor Frequency:2.437 GHzThe Mode: Monitor confirms it's enabled.
3. Scan for Target Networks
Now that your adapter is in monitor mode, scan for Wi-Fi networks in range.
Why Do This?
You need the BSSID (MAC address) and Channel (CH) of the target Wi-Fi network.
This ensures you capture only relevant traffic.
How to Scan for Wi-Fi Networks?
Run:
airodump-ng wlan0monThis will display a table like -
BSSID PWR Beacons Data CH MB ENC ESSID
AA:BB:CC:DD:EE:FF -40 85 120 6 54 WPA2 MyWiFiWhat Each Column Means:
BSSID: MAC address of the access point
PWR: Signal strength (the closer to 0, the stronger the signal)
CH: The wireless channel the network is on
ENC: Type of encryption (e.g., WEP, WPA, WPA2)
ESSID: Network name (SSID)
💡 Note Down These Details for the Target Network:
BSSID (MAC Address):
AA:BB:CC:DD:EE:FFChannel (CH):
6ESSID (Wi-Fi Name):
MyWiFi
How to Navigate the airodump-ng Interface:
The airodump-ng output is live and constantly refreshing, but you can navigate and control it:
Press
Space: Pauses the real-time output. Press it again to resume.Use
Ctrl+C: Stops the scan and exits the program.Arrow Keys/Scrolling: Unfortunately, you can't scroll up/down directly in
airodump-ng. Instead, you can pipe the output to a file for easier review:
airodump-ng wlan0mon > output.txtOnce saved, open output.txt to review the list of networks.
Search for in output.txt:
To find lines containing a BSSID or ESSID (Wi-Fi name), use the following commands:
Search by BSSID:
grep "AA:BB:CC:DD:EE:FF" output.txtThis will show all lines containing the BSSID AA:BB:CC:DD:EE:FF.
Search by ESSID (Wi-Fi name):
grep "MyWiFi" output.txtThis will display lines with the network name MyWiFi.
4. Capture the 4-Way Handshake
Once you've identified the target network, capture packets only from that network.
Why Is This Important?
Instead of listening to all networks, this filters packets only from the target Wi-Fi.
This increases the chance of capturing a handshake faster.
How to Start Packet Capture?
Run:
airodump-ng -c <channel> --bssid <BSSID> -w capture wlan0monFor example:
airodump-ng -c 6 --bssid AA:BB:CC:DD:EE:FF -w capture wlan0mon-c 6→ Capture only on channel 6 (target Wi-Fi channel).--bssid AA:BB:CC:DD:EE:FF→ Capture only from the target Wi-Fi.-w capture→ Save the packets to a file namedcapture.
What Happens Now?
Your terminal will display connected devices.
If a device connects to the network, the handshake will be captured automatically.
When a device connects or reconnects to the network, the WPA handshake will be captured automatically. This handshake contains EAPOL (Extensible Authentication Protocol over LAN) packets, which are exchanged during the four-way handshake process for authenticating the device to the network.
Look for EAPOL packets in the capture file under the Notes column—they indicate that the handshake process has been captured.
End the Aircrack-ng Session to Complete the Capture
Once you've captured the handshake (indicated by an EAPOL packet in airodump-ng), it's important to stop the process properly to ensure the .cap file is saved with all relevant data.
Steps to end the capture:
In the terminal running airodump-ng, press Ctrl+C to stop the session.
The .cap file will be finalized and saved in the directory you specified with the -w option (e.g., capture-01.cap).
5. Force Devices to Reconnect (Optional)
If no devices are connecting to the target network on their own, you can speed up the handshake capture by forcing devices to disconnect temporarily. This forces them to reconnect, triggering the 4-way handshake in the process.
Why Use a Deauthentication Attack?
A deauthentication attack works by sending deauth packets to the target device, momentarily kicking it off the network. When the device reconnects, it performs the 4-way handshake, giving you a chance to capture it.
Faster Handshake Capture: No need to wait for a natural connection event.
Effective for Networks with Few Devices: Ensures you can capture the handshake even with limited network activity.
Send Deauthentication Packets
Open a new terminal and use aireplay-ng to send deauth packets. Run:
aireplay-ng -0 10 -a <BSSID> wlan0monExample:
aireplay-ng -0 10 -a AA:BB:CC:DD:EE:FF wlan0mon-0→ Deauthentication attack10→ Number of packets to send-a→ Target Wi-Fi MAC address (BSSID)
Target a Specific Device (Stealthier)
aireplay-ng -0 5 -a <BSSID> -c <Client_MAC> wlan0mon-c <Client_MAC> = Kick off only one device instead of all.
This method is stealthier because it only disconnects a single client instead of all devices on the network.
Knocking off every user at once can quickly raise suspicion, while selectively deauthenticating one device makes the attack blend in with normal network behavior, such as a weak signal or temporary interference. Since other users remain connected, the network owner is less likely to notice anything unusual.
6. Verify Handshake Capture
After a client reconnects, check if the handshake was captured.
aircrack-ng capture-01.capIf successful, it will show:
WPA (1 handshake)7. Extract and Crack the Hashed Password
Once you’ve captured the handshake, it’s time to extract and crack the password. While Aircrack-ng is a traditional tool for this, it runs only on the CPU and requires large pre-generated wordlists, which can be slow and inefficient.
Instead, we’ll use Hashcat, a powerful GPU-accelerated tool that is significantly faster and allows for advanced password combinations and masks.
Convert to Hashcat Format
Use hcxpcapngtool to convert your .cap file into a format Hashcat can read:
hcxpcapngtool -o hash.22000 capture-01.capVerify Conversion Success
Once the conversion is complete, you should check if the output contains valid handshakes. Use hcxpcapngtool with the -i option to inspect the file:
hcxpcapngtool -i hash.22000Look for lines indicating the presence of a WPA handshake. If it shows valid entries, your conversion was successful. If not, ensure you captured a proper handshake and repeat the process.
8. Use Hashcat to Crack the Password
Once you’ve captured the handshake and converted it into a format Hashcat can read, it’s time to crack the password. There are two ways to generate password guesses: precompute a full wordlist or generate passwords dynamically using a mask. Both methods have pros and cons, depending on the situation.
Option 1: Precompute the Wordlist
In this method, you generate the entire wordlist in advance, combining different patterns, and feed it into Hashcat.
How it Works:
Combine different wordlists, such as adjectives, nouns, and numbers.
Create all possible combinations and save them in a single file.
Use Hashcat to compare each password in the wordlist to the captured hash.
Example Wordlists:
Here are wordlists you can use for default Spectrum WiFi password patterns:
adjectives.txt: Contains all possible adjectives (e.g., happy, smart, tiny).
nouns.txt: Contains all possible nouns (e.g., dog, bird, fish).
numbers.txt: Contains all three-digit numbers from 000 to 999.
How to Precompute the Wordlist:
Combine adjectives and nouns:
hashcat -a 1 adjectives.txt nouns.txt --stdout > combined_wordlist.txtThis will create a file with entries like:
happydog
angrydog
tinydog
happycat
angrycat
tinycat
happyfish
angryfish
tinyfish
etc...Append numbers to create full combinations:
Once you have the combined list (combined_wordlist.txt), you can append three-digit numbers (000–999) to each combination to follow the pattern [adjective][noun][3 digits] using Hashcat:
hashcat -a 1 combined_wordlist.txt numbers.txt --stdout > final_wordlist.txt This will create a file with entries like:
happydog000
happydog001
happydog999
angrydog000
angrydog123
tinydog999
happycat000
angrycat001
tinycat999
happyfish000
angryfish123
tinyfish999Run Hashcat with the Precomputed Wordlist:
Once you've created the final wordlist with every possible combination of [adjective][noun][3 digits] (e.g., happydog422), the next step is to run Hashcat and check each entry against the captured handshake.
hashcat -m 22000 hash.22000 -a 0 final_wordlist.txtExplanation of the command:
-m 22000: WPA2 hash type.
-a 0: Straight attack mode (reads from the precomputed wordlist).
final_wordlist.txt: Contains every combination of [adjective][noun][3 digits] (e.g., happydog422).
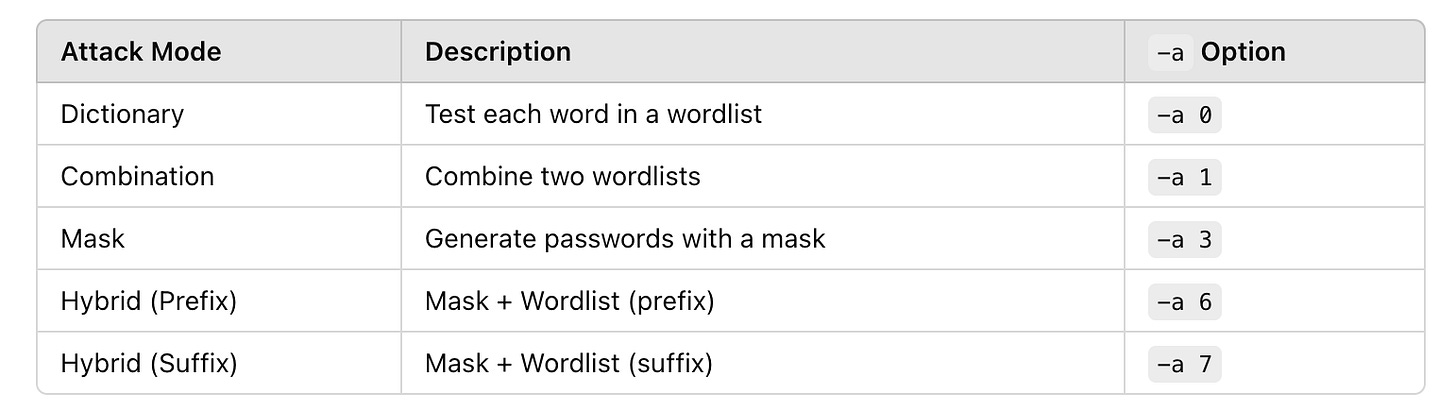
Hashcat Attack Modes (-a Options)
Hashcat has multiple attack modes for generating and testing passwords. Here’s a summary of the most common modes:
Using a precomputed wordlist allows Hashcat to run faster during the attack since it reads each password directly from the list without needing to generate combinations on the fly.
This makes it easy to review because you can see all possible combinations in the file beforehand, ensuring transparency in what will be tested.
Once the wordlist is built, it can be saved and reused for future attacks with similar patterns, saving you time in later efforts. However, the downside is that precomputed lists can take up a significant amount of storage space, especially when dealing with large combinations or longer patterns.
If the list becomes too large, managing it can be a challenge.
Option 2: Use a Mask (Generate Passwords Dynamically)
Instead of creating a large precomputed wordlist, you can use a mask to generate password combinations on the fly. This method is more efficient when dealing with longer patterns or a wide range of possibilities because it doesn’t require you to store and manage massive lists. Instead, Hashcat creates each password combination dynamically during the attack based on a defined pattern.
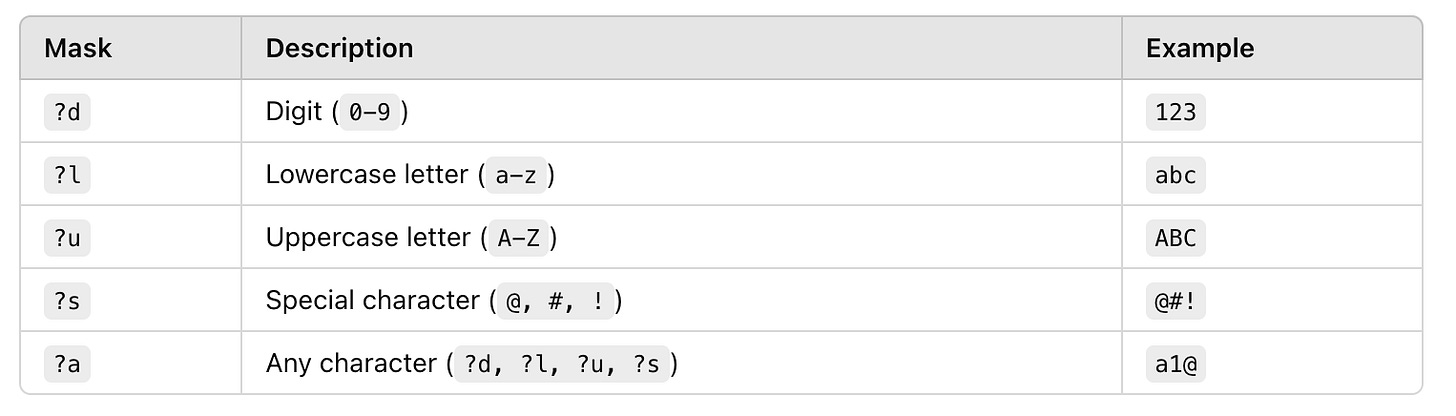
A mask is essentially a template that tells Hashcat what kind of characters to use at each position in the password. Masks are useful for guessing passwords that follow common patterns, such as lowercase letters followed by numbers.
How it Works:
The masks or -m option allow you to generate passwords dynamically based on patterns. Each position in a mask is represented by a placeholder that corresponds to a specific type of character:
?l= lowercase letter (a–z)?d= digit (0–9)
For example, the mask ?l?l?l?d?d?d will generate passwords with three lowercase letters followed by three digits, such as:
abc123
xyz999
dog422Masks are ideal for situations where the pattern is somewhat predictable but you want to avoid the time and storage required to create a full list in advance. They are also more flexible since you can adjust the pattern without needing to regenerate wordlists.
Using a mask keeps storage usage low because no large wordlists are generated or stored. It also provides flexibility, allowing you to change the pattern easily during the attack. However, generating passwords on the fly can be slightly slower compared to reading from a precomputed list, and you won’t be able to see all the possible combinations in advance.
To use a mask instead of precomputing the list, combine the adjectives, and nouns into the combined wordlist, then use a mask for the numbers 000 - 999
hashcat -m 22000 hash.22000 -a 7 combined_wordlist.txt ?d?d?d-a 7: Hybrid attack (combines a wordlist with a mask).
?d?d?d: Appends three digits (000–999) to each word in combined_wordlist.txt.
Hashcat will take every word in the wordlist and add all three-digit combinations dynamically.
Which Option Should You Choose?
Precompute the Wordlist if your pattern is small and well-defined (e.g., [adjective][noun][3 digits]), and you want fast results.
Use a Mask if the pattern is large or complex, or if you need flexibility without generating huge files.
9. Viewing the Cracked Password
Once Hashcat finds the correct password, it saves it in a file called a potfile (short for "potentiated file"). The potfile is a record of previously cracked hashes and their corresponding passwords. This allows Hashcat to skip already-cracked hashes in future attacks, saving time and effort.
To display the cracked password from the potfile, run this command:
hashcat -m 22000 hash.22000 --show-m 22000 specifies the hash type (WPA2 handshake).
--show tells Hashcat to display any previously cracked passwords stored in the potfile.
If a match is found, Hashcat will output the cracked password along with the hash.
What Happens If No Match Is Found?
If no password is found, this means none of the combinations in your wordlist or mask matched the captured handshake. In that case, you should tweak your wordlist, adjust your mask to cover more combinations, or refine your strategy based on what you know about the target.
10. Troubleshooting Hashcat Issues:
When using Hashcat, you might encounter several common issues that can slow down your progress. Here’s a guide to identifying and fixing them.
Issue: Hashcat is Slow
Hashcat’s speed largely depends on whether you’re using a CPU or GPU. While Hashcat can run on a CPU, it’s far slower compared to using a GPU—sometimes up to 100x slower. For most people, buying a GPU just for password cracking is unrealistic due to the cost and the complexity of setup.
Why GPUs Are Faster
GPUs are built for parallel processing, which allows them to compute thousands of password hashes simultaneously, whereas CPUs are optimized for sequential tasks, limiting their speed. While a high-end gaming GPU can dramatically reduce cracking time, configuring and maintaining a dedicated GPU cracking setup can be difficult and expensive.
Realistic Solutions to Speed Up Hashcat:
Use Cloud Services (Most Practical Option):
Cloud platforms offer ready-to-go virtual machines with multiple GPUs, giving you the power you need without the hassle of setup. Some top services include:Amazon AWS: Offers instances with up to 8 GPUs for extremely fast cracking.
Google Cloud: Provides flexible pricing and powerful GPUs.
Microsoft Azure: Reliable and scalable GPU resources.
Cloud solutions allow you to scale up your cracking power temporarily, paying only for what you use.
Repurpose a Gaming PC (If Available):
If you already have a gaming PC, you can install Kali Linux and use its GPU for basic password cracking. It won’t match a cloud setup with multiple GPUs, but it’s an affordable way to boost speed without buying new hardware.
Issue: Wordlist is Too Large or Cracking Takes Too Long
If your wordlist is too large, it can significantly slow down the process. Splitting the wordlist into smaller chunks allows you to process it more efficiently or run multiple instances of Hashcat in parallel.
How to Split a Wordlist into Smaller Files
mkdir split_wordlists for letter in {a..z}; do grep "^$letter" nouns.txt > split_wordlists/${letter}_words.txt; doneExplanation:
for letter in {a..z}: Loops through each letter from a to z.
grep "^$letter": Filters lines that start with the current letter.
> split_wordlists/${letter}_words.txt: Saves each subset in a separate file (a_words.txt, b_words.txt, etc.).
Once split, you can run Hashcat on each smaller file to crack specific portions of your wordlist.
Issue: Managing the Potfile
When Hashcat cracks a password, it saves it in a potfile. The potfile keeps track of previously cracked hashes to prevent re-cracking, which saves time. However, it can cause confusion if you want to start fresh or re-test a wordlist.
Key Potfile Commands:
Locate the Potfile:
find / -name "*.potfile"The potfile is typically located at:
~/.hashcat/hashcat.potfileRemove the Potfile (Start Fresh):
brm ~/.hashcat/hashcat.potfileDisable the Potfile Temporarily:
Use the--potfile-disableoption to prevent Hashcat from using or updating the potfile during a run:
hashcat -m 2500 hash.txt --potfile-disableCongrats! You Made It to the End!
Hopefully, it worked for you! If not, no worries—leave a comment and let me know where you got stuck or what you need help with. I’m here to help you figure it out and get you back on track.
Keep experimenting, stay curious, and have fun honing your skills.



This is interesting. Thank you.