Lab: NetBIOS Enumeration with Windows Command Line Tools
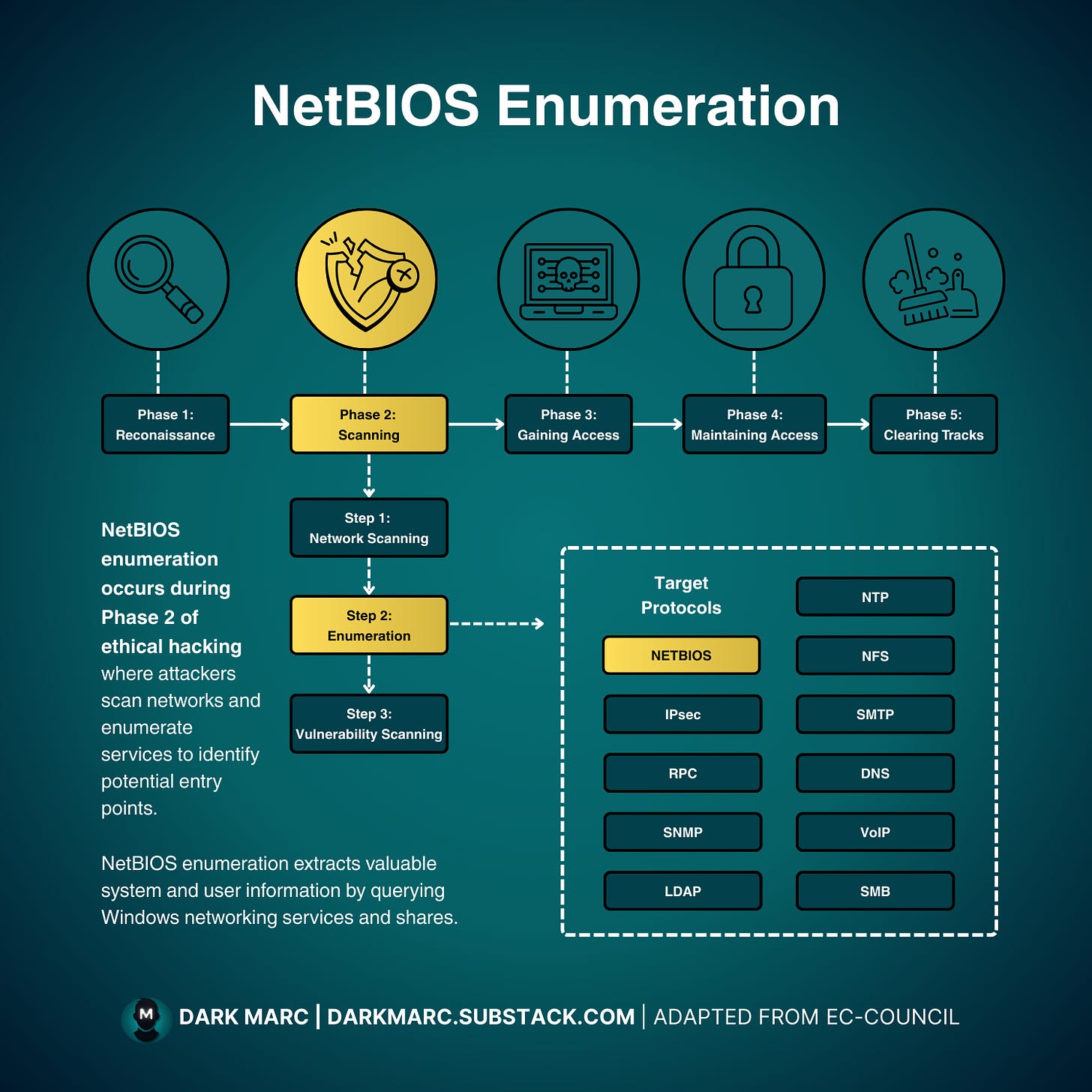
Enumeration is the second step of Phase 2 (Scanning) in the EC-Council Ethical Hacking methodology. In this phase, we actively probe target systems to gather detailed information about available services, resources, and potential vulnerabilities.
Enumeration can target various protocols and services such as SNMP, LDAP, DNS, SMB, and NetBIOS.
When legacy Windows systems are present and NetBIOS is enabled, NetBIOS enumeration is an effective technique we can use to discover critical network intelligence including machine names, shared resources, user accounts, system services, and security configurations.
In this lab we will focus on NetBIOS enumeration using native Windows command-line utilities to discover what information this particular protocol exposes and how that information can be used for further assessment and potential exploitation.
Learning Objectives
By the end of this lab you should be able to reliably extract and interpret reconnaissance data from NetBIOS-enabled hosts, including (but not limited to):
Machine names, operating system versions, running services, and open ports
Network resources and published shares on individual hosts
Usernames and user groups visible via enumeration
Share permissions (read/write/listing capabilities)
System and service policies, and exposed configuration data
Routing table and audit/service settings that are discoverable
SNMP details and fully qualified domain names (FQDNs) where available
Prerequisites
Before you begin this lab, ensure you have the following:
Hypervisor Software: You’ll need a hypervisor to create and manage virtual machines.
Virtual Machines: Set up one Windows Server 2019 machine to act as your attacker and one Windows 11 (with NetBIOS enabled) as the target.
Basic Understanding: This lab is intended for those with some knowledge of hypervisors and virtual machines. If you're new to these concepts, you can learn them in this lab: How to Create Virtual Machines for Cybersecurity Labs
⚠ Important Note: Use an isolated lab network (virtual machines or a segmented VLAN). Do not perform enumeration on networks or devices for which you do not have explicit authorization.
What is NetBIOS?
NetBIOS (Network Basic Input/Output System) is an older API used by Windows to support name resolution and resource sharing on small local networks.
It provides a session layer interface that allows applications on different computers to communicate over a local area network. NetBIOS exposes various types of information through different enumeration methods:
Name records: 16-character identifiers where the first 15 characters represent the host or device name, and the 16th character indicates the service type or record suffix
Shared resources: Network shares, printers, and other resources available on target machines
User and group information: Account details visible through network enumeration
Service information: Running services, session details, and network capabilities
Although modern Windows releases favor DNS and newer protocols, many environments — especially those with legacy systems, default configurations, or mixed network environments — still have NetBIOS enabled.
This persistence makes NetBIOS enumeration a valuable reconnaissance technique that can reveal detailed information about network topology, available resources, and potential attack vectors without requiring authentication.
What are NetBIOS Shares?
On Windows, a share is any folder or resource exported over the network (for example \HOST\Public). Each share has access controls that determine who can list, read, or write files. NetBIOS enumeration reveals which shares exist and what access levels are allowed for particular users or groups.
If a share permits read access, an attacker could exfiltrate files.
If a share permits write access, an attacker could upload files, modify or delete data, or consume disk space (potential DoS).
If no accessible shares exist (or all require strong credentials), the immediate risk is reduced, but enumeration still yields host and account information useful for follow-on attacks.
Lab Goal: Use Windows Utilities for NetBIOS Enumeration (nbtstat and net use)
Part 1: Use nbtstat to perform NetBIOS enumeration
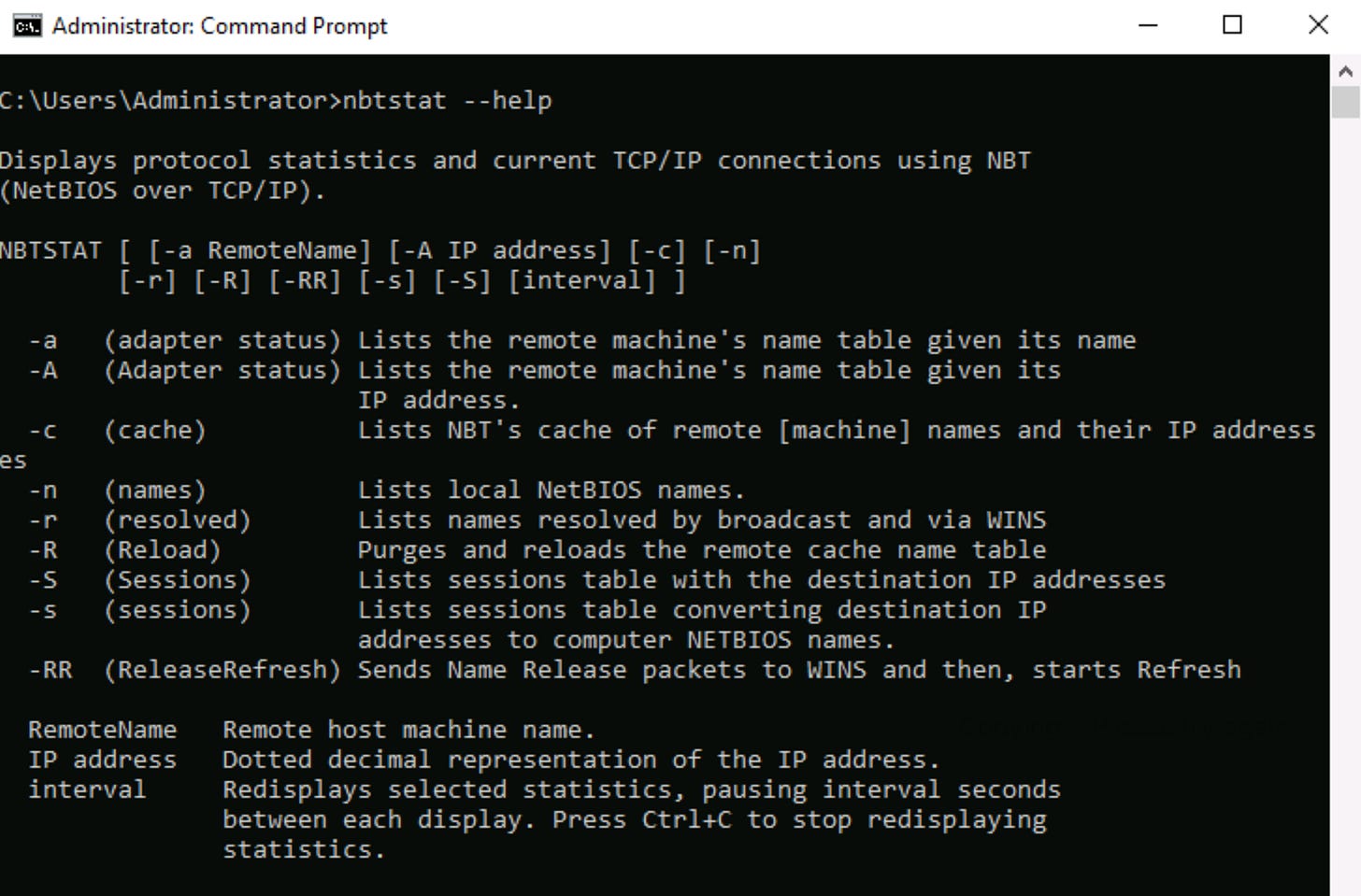
The nbtstat utility is a built-in Windows command that displays NetBIOS over TCP/IP (NetBT) information.
The nbtstat tool reveals which NetBIOS names, services, and resources a target host is advertising over the network.
This information enables further reconnaissance by identifying available shares, active services, and potential entry points for deeper network penetration.
In this lab, we will use our Windows Server 2019 machine (10.10.1.19) as the attacking platform to enumerate a Windows 11 target machine (10.10.1.11) over the network.
Lab Instructions:
Log into your Windows Server 2019 machine.
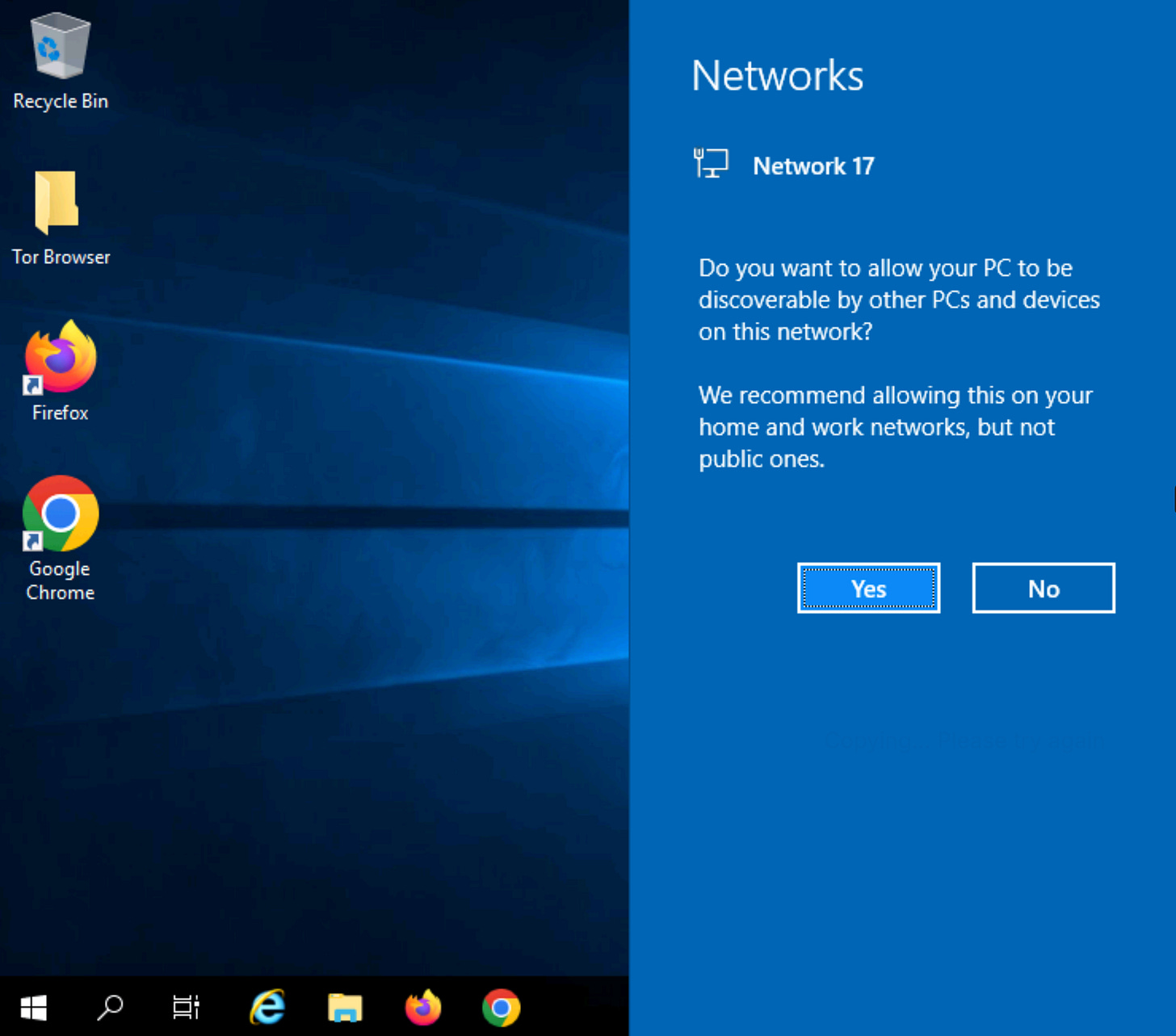
Step 1 ) Make your machine discoverable on the network:
If the Networks screen appears, click ‘Yes’ to allow your PC to be discoverable by other PC’s on the network. This is an important step, because if you don’t click ‘Yes’ the device will be hidden from others on the network.
Step 2) Use 'nbtstat’ to perform NetBIOS enumeration
Use nbtstat commands to enumerate NetBIOS on the target machine.
A) Type nbtstat —help to view all available commands:
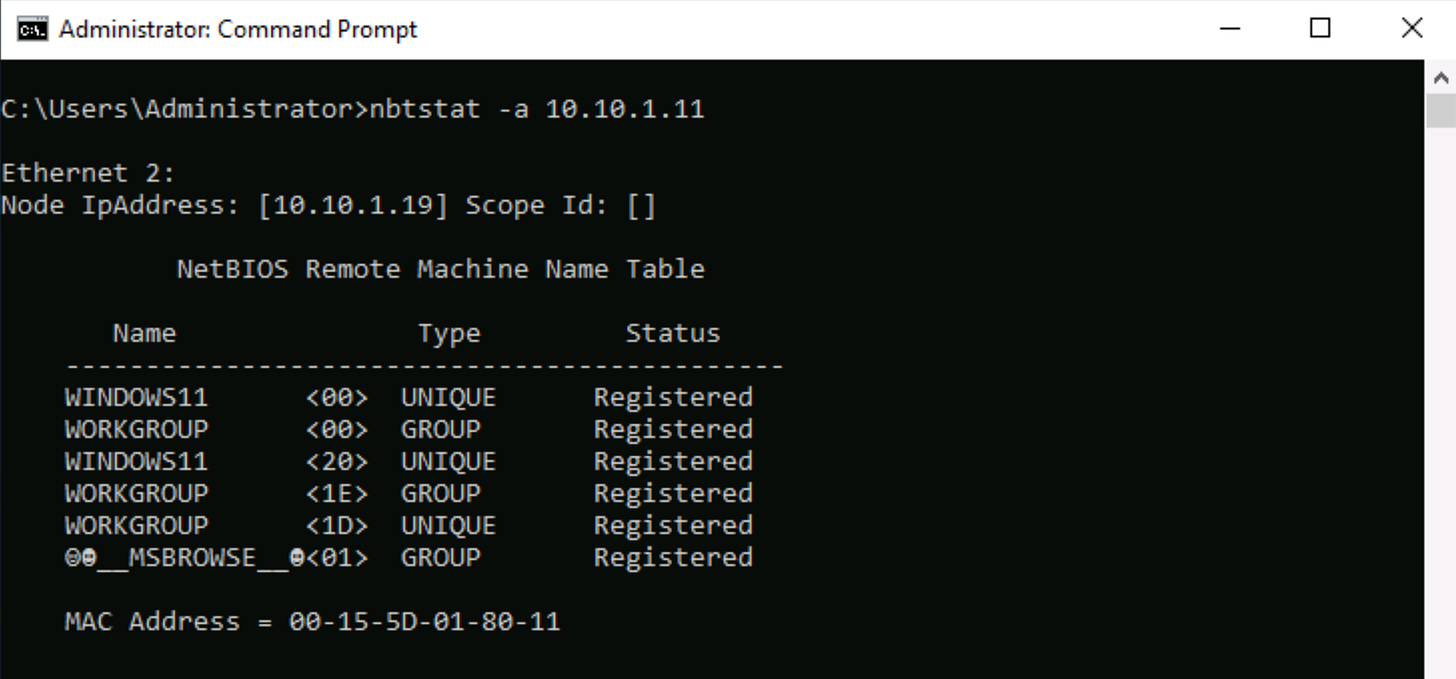
B) Use nbtstat -a to Display NetBIOS Name Table
A NetBIOS name table is a list of network identities and services that a Windows machine advertises to other computers on the network. It ells other devices what it's called, what workgroup it belongs to, and what network services it's running.
The command nbtstat -a [IP Address] will display the NetBIOS name table for the target machine. This table lists the NetBIOS name table of the target device, listing devices it has shares with on the network.
The nbtstat results reveal that the target machine at 10.10.1.11 is a Windows 11 workstation named "WINDOWS11" that belongs to the default "WORKGROUP."
The output shows the machine has file sharing services enabled and is acting as the master browser for the workgroup, which means it maintains a list of network resources and can share files.
The enumeration also exposes the machine's MAC address (00-15-5D-01-80-11), providing both service information and hardware identification that can be used for further network reconnaissance and potential access attempts.
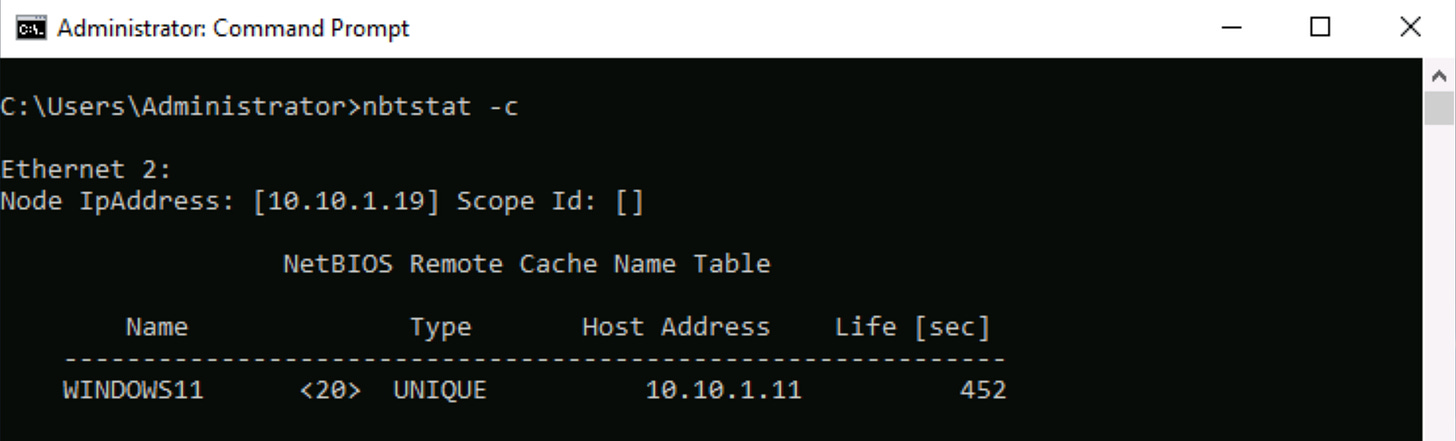
C) Use nbtstat -c to Display NetBIOS Name Cache
The NetBIOS name cache is a temporary storage area that holds the mappings of NetBIOS names to their corresponding IP addresses, allowing for quicker name resolution on a network. It helps improve network performance by reducing the need to repeatedly resolve names through broadcasts or a name server.
The command nbtstat -c is used to display the contents of the NetBIOS name cache on your machine. If you have the Internet Protocol (TCP/IP) installed and are connected to a network, it should run, but it may return "no names in cache" if there are no entries.
Step 3) Use 'net use’ to perform NetBIOS enumeration
The net use utility is a built-in Windows command that establishes, displays, or disconnects connections to shared network resources.
In NetBIOS enumeration, it allows us to discover and connect to shared folders, printers, and other resources on target machines.
When combined with NetBIOS name resolution, net use can help identify accessible shares and test authentication requirements, providing valuable intelligence about the target's security posture and available resources.
A) Type net use /? to view the syntax you can use for this command:
B) Run net use command
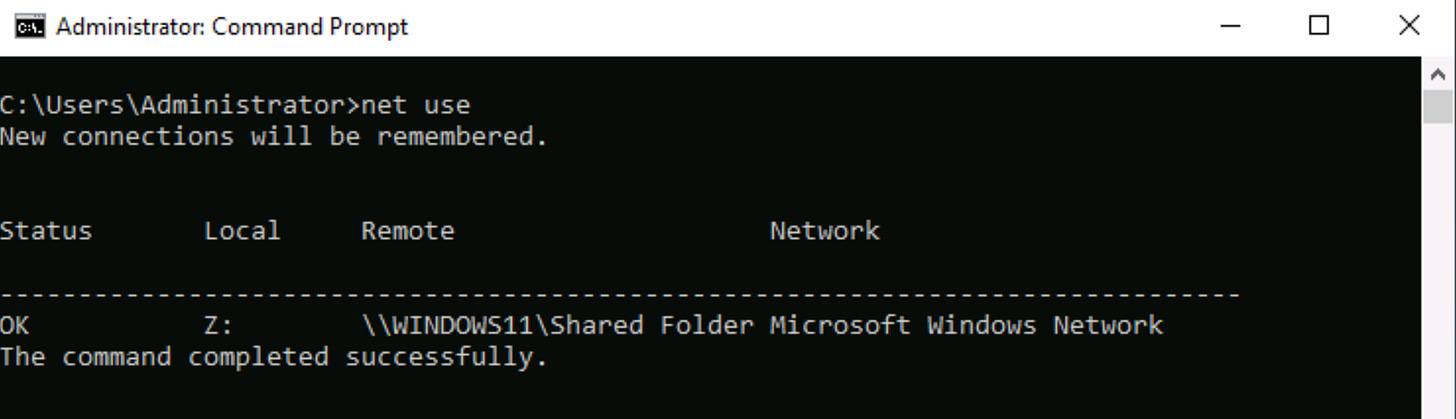
The net use command will output the available shares on NetBIOS for the current machine. In the example output below, we can see that there is one share available.
The output shows the current network connections established from your machine:
Status Column: Shows "OK" indicating the connection is active and functioning.
Local Column: Shows "Z:" which means this remote share has been mapped to the local drive letter Z on your machine.
Remote Column: Shows "\WINDOWS11\Shared Folder" which indicates:
The target machine's NetBIOS name is "WINDOWS11"
There is an accessible shared folder called "Shared Folder" on that machine
This share is currently connected and mapped to your local Z: drive
Network Column: Shows "Microsoft Windows Network" indicating this connection is using standard Windows file sharing protocols.
Key Findings from this enumeration:
Successful Connection: The "OK" status confirms you have successfully authenticated and connected to a share on the target machine (WINDOWS11 at IP 10.10.1.11).
Share Discovery: You've discovered that the target machine has at least one accessible network share named "Shared Folder".
Access Level: Since the connection was successful, you have at minimum read access to this share (and potentially write access depending on the share permissions).
Drive Mapping: The share has been mapped to drive letter Z:, meaning you can now access the remote files as if they were on a local drive by navigating to Z:\ in Windows Explorer or command prompt.
This information is valuable for further enumeration as you can now explore the contents of this share to potentially discover sensitive files, user data, or other resources that could be useful for your assessment.
Lab Completion and Next Steps
Upon completing this lab, you have successfully:
Used
nbtstat -ato enumerate NetBIOS name tables and identify target machine servicesUsed
nbtstat -cto view local NetBIOS name cache entriesUsed
net useto discover and connect to accessible network sharesGathered intelligence about the target system including machine name, workgroup membership, running services, and accessible resources
Security Implications
This lab demonstrates how legacy protocols like NetBIOS can expose significant information about Windows systems, even without authentication. The reconnaissance data gathered through NetBIOS enumeration can be used for:
Identifying potential attack vectors through accessible shares
Understanding network topology and trust relationships
Gathering information for social engineering attacks
Planning further enumeration and exploitation activities
Thanks for joining me for this lab exercise.
Happy hacking!