Substack Confirms Data Breach - Is Your Info Protected?
Substack has confirmed a data breach affecting user data.
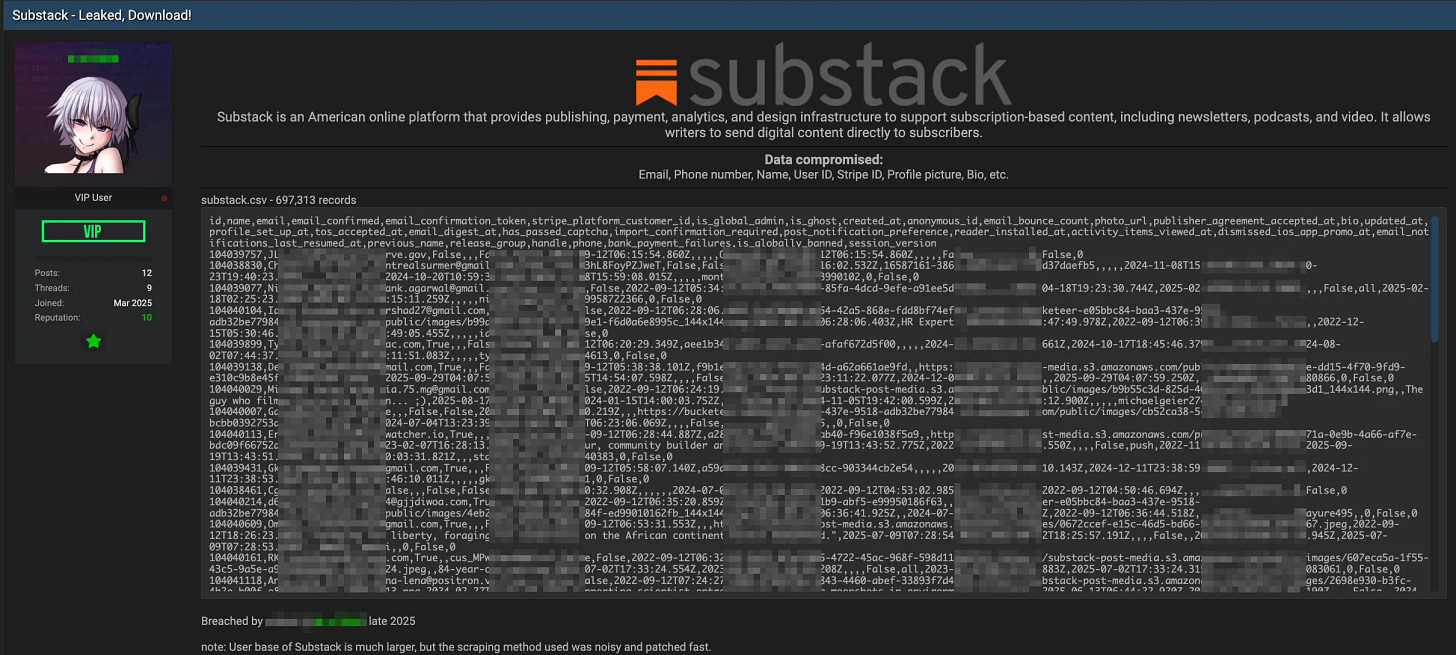
According to the company, an unauthorized third party accessed its systems in October 2025 and obtained user email addresses, phone numbers, and internal metadata. The breach was only discovered months later, in February 2026.
Substack says passwords, credit card numbers, and financial information were not affected, but the company has not disclosed how many users were impacted, what vulnerability was exploited, or why detection took so long.
Why Exposed Emails Are Dangerous
Your email address is the backbone of your online identity.
Most people reuse the same email and password across a variety of services. When one site leaks credentials, attackers automatically try that same email and password combination across hundreds of other platforms. This works because reuse is extremely common and trivial to automate.
Even when only an email is exposed, attackers can pivot. Emails are routinely searched in breach databases that aggregate years of past leaks. Those databases often reveal other accounts tied to the same email and sometimes old passwords used elsewhere. From there, attackers attempt logins, abuse password resets, send targeted phishing, or move toward extortion.
This is how a single breach turns into many compromised accounts.
How to Protect Yourself Going Forward
Never Reuse Passwords
Do not reuse passwords. Ever.
If one service is breached and you reused a password, attackers can immediately try it everywhere else. This remains one of the most common causes of account takeover.
Use a password manager to generate and store a unique password for every site.
Recommended options:
A password manager makes strong, unique passwords the default instead of an extra chore. You only need to remember one master password, and it gives you access to a vault of long, unique passwords for every site you use.
Never Reuse Email Addresses Across Most Accounts
Reusing the same email address across most of your accounts makes it easy for attackers to map your entire digital footprint after a breach.
Once your email is exposed, attackers search it across breach databases and public data sets. This often reveals many other services tied to that email and sometimes old passwords from previous leaks. From there, attackers target password resets, send highly convincing phishing emails, or attempt account recovery attacks.
This problem is not limited to high value accounts. Low importance accounts like forums, newsletters, and social platforms are often the weakest link. They expose usernames, interests, and behavior patterns that attackers use to move toward more valuable accounts.
The correct mental model is to treat email addresses like passwords. Most accounts should get a unique one.
Email aliases make this practical. ProtonMail is a strong option.
ProtonMail supports unlimited email aliases, allowing you to create a unique address for every service. All aliases deliver to the same inbox, so management stays simple.
For example:
substack@youralias.proton.me
shopping@youralias.proton.me
forum123@youralias.proton.me
To the outside world, these are completely separate addresses.
If one alias is leaked, attackers cannot use it to discover your other accounts or your primary email. If an alias starts receiving spam or phishing, you can disable it without breaking anything else.
Data Breaches Are Inevitable
Breaches are inevitable. Credential reuse is what turns them into cascading failures.
Unique passwords and unique email addresses isolate damage and prevent a single incident from becoming a full account takeover chain. Stay safe out there!
If you found this guide helpful, please share.



Sad that the first time I hear about it is in a Substack article, rather than a communication from Substack as a user.
really quick to jump on this! solid advice without the fud. nice stuff!