Reconnaissance is the first step in ethical hacking, where you gather information about a specific target to understand its digital setup, weaknesses, and exposed data.
Reconnaissance helps hackers create a blueprint of the target’s systems, enabling the identification of potential attack vectors and security weaknesses. The goal is to identify as many attack vectors as possible.
Footprinting is a step in the reconnaissance process that focuses on mapping out detailed information about a target organization, such as its website structure, technologies, subdomains, and sensitive exposures.
This structured process allows ethical hackers to assess and strengthen an organization’s security posture by simulating attacker methodologies.
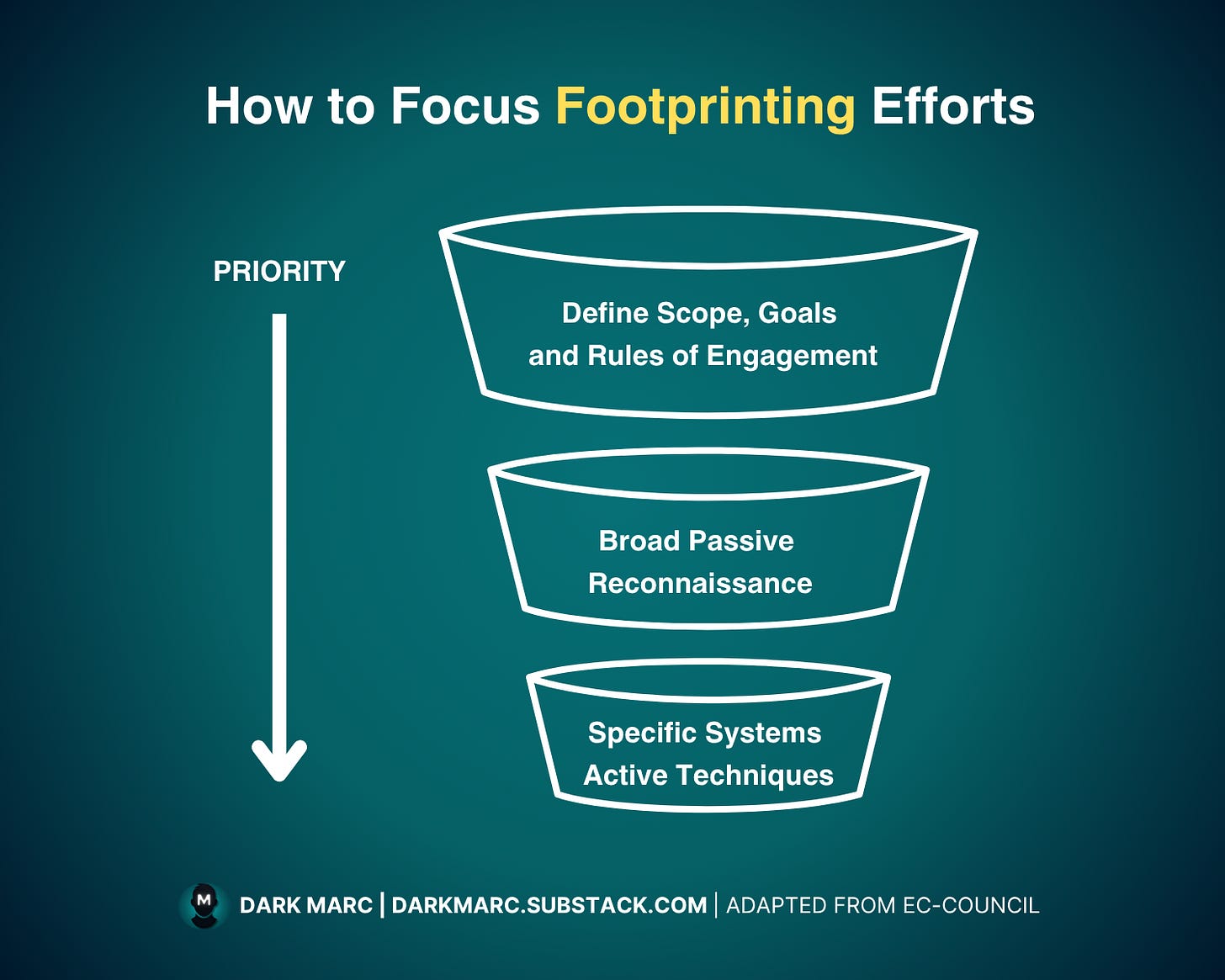
How to Focus Footprinting Efforts
Gathering all info is impractical and inefficient. Instead, hackers use a phased approach: start with broad passive reconnaissance, then narrow down to active techniques for specific vulnerabilities or systems.
Defining Scope, Goals and Rules of Engagement:
Hackers prioritize relevant data based on the engagement’s scope, goals, and rules of engagement (RoE).
If you are tasked with defining these for your client, check out this guide:
Defining the Goals:
Defining the goals for footprinting ensures that the process aligns with the client’s security objectives and supports the overall engagement. The goals clarify the purpose of the ethical hacking engagement, aligning it with the client’s security objectives.
To understand the client needs, discuss what the they aim to achieve (e.g., identify vulnerabilities, test incident response, or ensure compliance with regulations like GDPR or PCI-DSS).
Defining the Scope:
The scope outlines the boundaries of the ethical hacking engagement, specifying what systems, networks, or assets can be tested and what is off-limits.
Client Consultation: Meet with the client to understand their infrastructure, assets, and concerns (e.g., web applications, internal networks, cloud services).
Identify Targets: Specify domains, IP ranges, applications, or physical locations to be tested. For example, “test example.com and its subdomains” or “exclude production servers.”
Define Depth: Determine how deep the testing can go (e.g., passive footprinting only, or active scanning and exploitation).
Timeframe: Set start and end dates for the engagement to ensure timely completion.
Documentation: Create a detailed scope document listing included and excluded assets, approved testing methods, and any constraints (e.g., avoiding specific systems during business hours).
A corporation, for example, might include their public-facing website and employee email accounts but exclude third-party cloud services or legacy systems.
Defining the Rules of Engagement:
The Rules of Engagement establish the legal, ethical, and operational guidelines that govern how the ethical hacking engagement will be conducted. These rules protect both the ethical hacker and the client organization while ensuring the testing remains within acceptable boundaries.
Key Components of RoE:
Legal Authorization: Obtain written authorization from the appropriate stakeholders before beginning any testing activities. This includes signed agreements, statements of work, and liability waivers to provide legal protection for all parties involved.
Communication Protocols: Establish clear communication channels and escalation procedures. Define who should be contacted in case of emergencies, system outages, or when critical vulnerabilities are discovered. Include primary and backup contacts with their availability hours.
Testing Windows: Specify when testing activities can occur (e.g., business hours only, weekends, or 24/7). Consider the organization's operational requirements and potential impact on business continuity.
Intensity Limitations: Define the acceptable level of testing intensity to prevent system disruption. For example, limit concurrent connections, scan rates, or the number of exploitation attempts to avoid overwhelming target systems.
Prohibited Activities: Clearly outline what activities are forbidden during the engagement. Common restrictions include:
No denial-of-service (DoS) attacks
No data destruction or modification
No social engineering of specific personnel
No physical security testing without explicit permission
No testing of third-party systems or services
Data Handling: Establish protocols for handling sensitive data discovered during testing. Define how data should be documented, stored, transmitted, and ultimately destroyed after the engagement concludes.
Incident Response: Create procedures for handling unexpected situations such as system crashes, security incidents triggered by testing, or discovery of active threats or breaches during the engagement.
Reporting Requirements: Specify deliverable formats, timelines, and distribution lists for interim and final reports. Define the level of technical detail required and any compliance or regulatory reporting needs.
Documentation and Approval: All RoE must be formally documented and approved by authorized representatives from both the testing team and the client organization before any reconnaissance or testing activities begin.
This documentation serves as the contractual foundation for the entire engagement and helps prevent misunderstandings or legal complications.
The RoE should be reviewed and updated as needed throughout the engagement, with any changes requiring formal approval from all stakeholders.
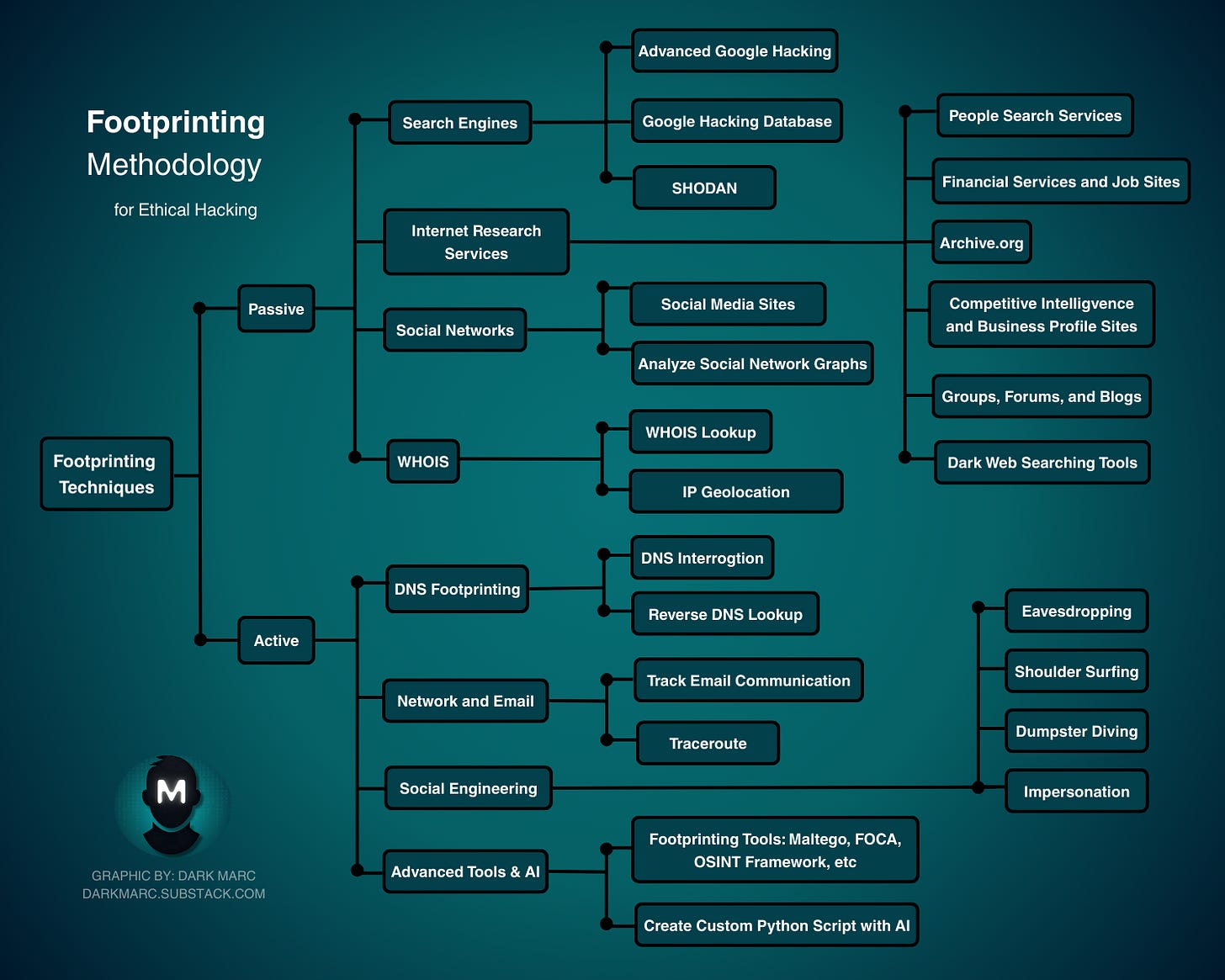
Types of Footprinting
In this section, we’ll go over the categories of footprinting as well as tools and techniques used for each. You’ll choose activities from this list based on the previously discussed goals, scope and ROE of the client.
Active & Passive Footprinting
Footprinting includes both active and passive techniques.
Passive Footprinting: Gathering information without directly interacting with the target system. Examples include analyzing public websites, social media, WHOIS records, job postings, or archived data (e.g., via Wayback Machine). This is stealthy and minimizes detection risk.
Active Footprinting: Directly engaging with the target system to collect data. Examples include network scanning (e.g., using Nmap), querying DNS servers, or social engineering. This carries a higher risk of detection but can yield more detailed information.
Technological Footprinting
Passive Tools
WHOIS Services - Domain registration information lookup
Internet Archive (Wayback Machine) - Historical website analysis
Search Engines - Google, Bing for indexed information
Netcraft - Internet infrastructure analysis
Shodan - Internet-connected device search engine
DNS Lookup Tools - Non-intrusive DNS queries
Active Tools
Nmap - Network discovery and security auditing
Burp Suite - Web application security testing
Acunetix - Web vulnerability scanner
Maltego - Link analysis and data mining (active probing features)
Recon-ng - Web reconnaissance framework (active modules)
Nikto - Web server scanner
Passive Techniques
WHOIS Lookups - Retrieving domain registration details
DNS Information Gathering - Querying public DNS records
Website Structure Analysis - Examining publicly available web content
Search Engine Reconnaissance - Using search operators for information discovery
Certificate Transparency Logs - Analyzing SSL certificate data
Social Media Mining - Gathering technical information from company profiles
Active Techniques
Network Scanning - Direct probing of network infrastructure
Port Scanning - Identifying open ports and services
Vulnerability Scanning - Automated security assessments
DNS Zone Transfers - Attempting to retrieve DNS zone files
SNMP Enumeration - Querying network devices directly
Web Application Fingerprinting - Direct interaction with web services
Banner Grabbing - Connecting to services to identify versions
People Footprinting
Passive Tools
Social Media Platforms - LinkedIn, Twitter, Facebook for profile viewing
Search Engines - Google, Bing for people searches
Public Records Databases - Government and commercial databases
People Search Engines - BeenVerified, Spokeo, PeopleFinder
Professional Networks - Industry-specific platforms and directories
News Archives - Historical news and press release databases
Active Tools
Social Engineering Frameworks - SET (Social Engineer Toolkit)
Communication Platforms - Direct messaging and contact tools
Survey Tools - Online questionnaires and forms
Phone/Email Systems - Direct contact mechanisms
Passive Techniques
Social Media Profiling - Observing profiles and public posts
Job Posting Analysis - Analyzing company recruitment information
Public Records Searches - Searching government and commercial databases
News and Media Monitoring - Tracking mentions in publications
Educational Background Research - Alumni directories and academic records
Conference and Event Analysis - Attendee lists and speaker profiles
Active Techniques
Direct Social Engineering - Phone calls, emails, or in-person conversations
Pretexting - Creating scenarios to elicit information
Surveys and Questionnaires - Direct information gathering
Professional Networking - Active engagement on platforms
Interview Requests - Formal or informal information gathering sessions
Physical Footprinting
Passive Tools
Surveillance Equipment - Cameras, binoculars for remote observation
Mapping Software - Google Earth, satellite imagery tools
Public Transportation Apps - Route and location information
Photography Equipment - Long-range cameras for discrete documentation
Drone Technology - Unmanned aerial reconnaissance (where legal)
Active Tools
Mobile Devices - Smartphones for on-site documentation
GPS Devices - Precise location tracking and mapping
Communication Equipment - Radios for team coordination
Lock Picking Tools - Physical security testing equipment
RFID/Badge Cloners - Access control testing devices
Passive Techniques
Remote Site Surveys - Visual assessment from public areas
Satellite Imagery Analysis - Studying facility layouts from aerial views
Public Information Gathering - Building permits, zoning records
Traffic Pattern Observation - Monitoring from distant vantage points
Waste Analysis - Examining discarded materials (dumpster diving)
Public Records Research - Property records and facility information
Active Techniques
On-site Surveillance - Direct physical monitoring of facilities
Tailgating Attempts - Testing unauthorized access procedures
Staff Interviews - Direct engagement with employees
Physical Security Testing - Testing locks, alarms, and access controls
Perimeter Probing - Active assessment of facility boundaries
Social Engineering - In-person manipulation for facility access
Reconnaissance Walks - Direct facility observation and documentation
Reconnaissance: Laying the Groundwork for Effective Ethical Hacking
To summarize what we’ve discussed: Reconnaissance is the first step in ethical hacking. Through footprinting, hackers collect data that reveals the structure, assets, and exposures of a target. This information helps identify potential weaknesses and define the most effective ways to test them.
A successful reconnaissance process starts with a clear understanding of the client’s goals, a well-defined scope, and agreed rules of engagement. These elements ensure the engagement is focused, legally sound, and aligned with the client's priorities.
Both passive and active techniques are necessary. Passive methods are useful for low-risk, broad data collection, while active methods provide more detailed information where needed. Choosing the right tool or technique depends on the target, the engagement terms, and the information required.
With proper planning and execution, reconnaissance provides accurate insights that help organizations improve their security posture and prepare for real-world threats. Happy hacking!
The Complete Guide to Vulnerability Scanning (Ethical Hacking)
Vulnerability Scanning is the second phase in ethical hacking, where you scan machines discovered in the previous phase (footprinting and reconnaissance) for vulnerabilities you can use to gain access to a system.