Scanning in ethical hacking is a three-step process that begins with identifying live hosts and open ports, then progresses into enumeration where we form active connections with the hosts to learn more about the attack surface.
In vulnerability scanning, we take it a step further by matching the ports, protocols and services found in previous steps with known vulnerabilities, setting the stage for the next phase, “Gaining Access”, where we exploit those vulnerabilities to get in to the target system.
Phase 2: Scanning - Three Step Process
Phase 2: Scanning is made up of three steps that work together:
Network Scanning - We discover live hosts, open ports, and running services using tools like Nmap. This gives us a broad view of what's available on the network.
Enumeration - We go beyond basic discovery by establishing active connections with target systems. We perform directed queries to extract detailed information like user accounts, network shares, and service configurations.
» Vulnerability Scanning (current step) - We identify specific security weaknesses in the services we've discovered and enumerated, preparing us for the actual exploitation phase.
Previous Step: Enumeration
If you haven't read about enumeration yet, check it out here:
In this guide, you will learn:
How to understand vulnerabilities, assessments and core concepts.
How to use common vulnerability assessment tools.
How to create and use vulnerability assessment reports.
Vulnerability Core Concepts
A vulnerability is a flaw in hardware, software, or configuration that attackers can exploit to gain unauthorized access. Some are widely known and cataloged, while others remain undisclosed until they’re actively exploited (zero-day vulnerabilities).
Not all systems are equally maintained. Many organizations still run outdated or unsupported software, leaving them exposed.
The GAO has reported that some federal systems are more than 60 years old, running software over a dozen versions behind. The older the system, the more vulnerabilities are documented against it, and the greater the risk.
In some cases, upgrading isn’t an option. Replacing legacy systems may be too disruptive or costly, leaving organizations to knowingly operate with weaknesses rather than overhaul critical infrastructure.
For attackers and defenders alike, staying informed about the latest vulnerability disclosures is essential. New vulnerabilities are always being discovered, and staying aware of these changes will keep you one step ahead.
Vulnerability Classification
Vulnerabilities can be organized into five categories:
1. Misconfigurations or Weak Configurations
These security vulnerabilities occur when a system is misconfigured or poorly configured. One commonly exploited vulnerability in this category is when default credentials are used on a device or software. I wrote an article going over some examples of this in the wild if you’d like to learn more:
2. Application Flaws
Application flaws are bugs or weaknesses in software that attackers can exploit.
One of the most notable examples is the Heartbleed Bug in the OpenSSL cryptographic library. This flaw allowed anyone on the Internet to read sensitive information from the memory of affected servers, including passwords, private keys, emails, and other confidential data, without leaving a trace.
These flaws can cause an application to behave in unintended ways, allowing attackers to steal data, impersonate users or services, or perform actions the software was not designed to allow.
3. Poor Patch Management
Poor patch management occurs when vulnerabilities are not fixed in a timely manner. As time goes on, more weaknesses become public and are exploited more often. If security patches are not released by software developers, and if they are not applied by administrators, the system accumulates vulnerabilities that remain exposed over time.
4. Design Flaws
Design flaws occur when a system is built without essential security features, allowing attackers to gain access or escalate privileges. This can include failing to encrypt sensitive data, not properly validating input on a website, or shipping machines with insecure default settings.
One example of a design flaw is when Microsoft once shipped Windows machines with a web server feature enabled by default. If left on, this exposed all those machines to potential attacks, creating a large-scale risk purely due to how the system was designed.
5. Third-Party Risks
Third-party risks come from relying on external code, especially open-source libraries that many developers use to build software. Attackers know these libraries are trusted, so they try to sneak in malicious code.
A recent example is the “Shai-Hulud” campaign, where attackers compromised more than 180 npm packages. One of the affected packages, @ctrl/tinycolor, had over 2 million weekly downloads. The malicious code was designed to steal cloud credentials, GitHub tokens, and npm tokens, and it spread automatically when developers installed the infected packages.
Supply-chain attacks like this are dangerous because one compromised library can quickly spread to thousands of applications that depend on it. Developers trust these libraries by default, but attackers take advantage of that trust to reach far more systems than they could by attacking one target at a time.
OWASP Top 10 Vulnerabilities
In addition to the categories above, the OWASP organization maintains a list of vulnerabilities that are commonly found. It is updated regularly, with the latest update being published in 2021. The current list includes:
Broken Access Control - Users can access data or functionality they shouldn't have permission to view or use. Example: A regular user manipulating a URL parameter to view another user's account information.
Cryptographic Failures - Sensitive data is exposed due to weak or missing encryption, poor key management, or flawed cryptographic implementations. Example: Passwords stored in plain text or using weak hashing algorithms like MD5.
Injection - Malicious code or commands are inserted into application inputs, allowing attackers to execute unintended operations. Example: SQL injection where an attacker inputs malicious SQL code into a login form to bypass authentication.
Insecure Design - Security flaws built into the application's architecture and design from the beginning, rather than implementation bugs. Example: An application that doesn't implement rate limiting, allowing unlimited login attempts.
Security Misconfiguration - Applications, servers, or databases are configured with insecure default settings or contain unnecessary features enabled. Example: Default administrator passwords left unchanged or debug mode enabled in production.
Vulnerable and Outdated Components - Applications use libraries, frameworks, or other software components with known security vulnerabilities. Example: Using an old version of a JavaScript library that contains publicly known security flaws.
Identification and Authentication Failures - Weaknesses in user identity verification, session management, or authentication processes allow attackers to impersonate users. Example: Weak password requirements or session tokens that don't expire properly.
Software and Data Integrity Failures - Applications don't verify the integrity of software updates, critical data, or CI/CD pipelines, allowing malicious modifications. Example: An application that downloads updates without verifying digital signatures.
Security Logging and Monitoring Failures - Insufficient logging, monitoring, or incident response capabilities prevent timely detection of security breaches. Example: Failed login attempts aren't logged, making it impossible to detect brute force attacks.
Server-Side Request Forgery (SSRF) - Applications fetch remote resources without validating user-supplied URLs, allowing attackers to make requests to internal systems. Example: A web application that fetches images from user-provided URLs without restricting access to internal network resources.
Vulnerability Scoring Systems and Databases
In the early days of hacking, companies often tried to keep vulnerabilities secret. While this may have seemed protective, it created a problem: hackers with malicious intent could discover these weaknesses and exploit them before anyone else knew they existed.
Over time, it became clear that security improves when vulnerabilities are disclosed responsibly. By working with system creators, researchers can ensure that users are informed of risks and that companies address issues promptly.
To organize and track vulnerabilities, the U.S. government created the National Vulnerability Database (NVD). This database uses the Common Vulnerabilities and Exposures (CVE) dictionary to catalog known security weaknesses.
Each CVE entry is classified using the Common Weakness Enumeration (CWE) system, which identifies the type of flaw or weakness, such as a buffer overflow or misconfiguration.
In addition, each vulnerability is assigned a Common Vulnerability Scoring System (CVSS) score, which quantifies its severity and potential impact. This combination helps organizations understand both what the problem is and how serious it is, enabling them to prioritize remediation effectively.
CVE Scoring
The (CVSS scores) quantify the severity of vulnerabilities, helping security teams prioritize issues to address first.
Scores range from 0 to 10 and are categorized as follows:
None (Score 0.0) – No significant impact on security.
Low (Score 0.1 – 3.9) – Minor issues that pose limited risk.
Medium (Score 4.0 – 6.9) – Vulnerabilities that can be exploited but have moderate impact.
High (Score 7.0 – 8.9) – Serious vulnerabilities that can lead to significant compromise.
Critical (Score 9.0 – 10.0) – Extreme risk; often allows full system compromise or widespread impact.
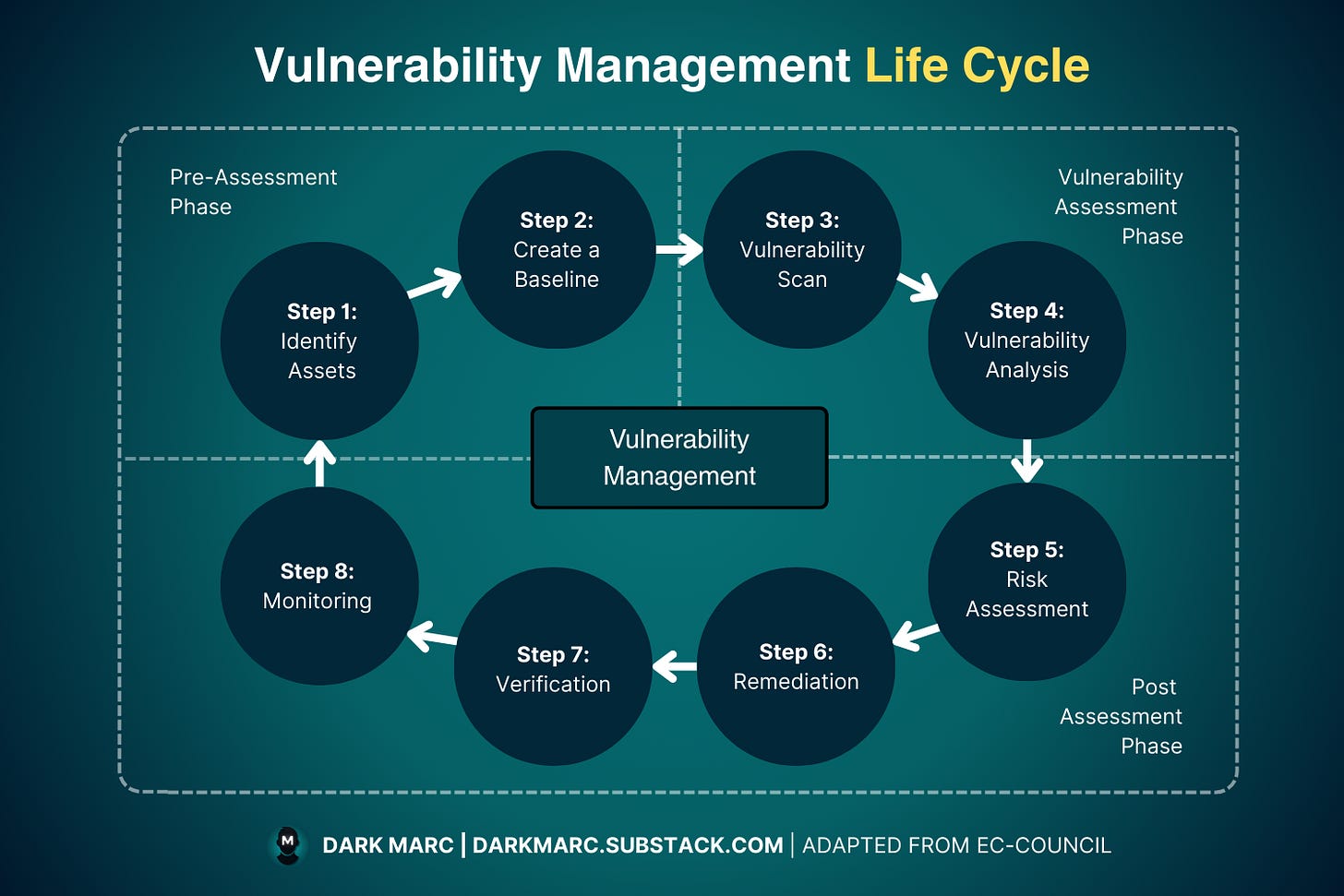
Vulnerability Management Lifecycle
Network defenders use the vulnerability management lifecycle as a systematic process for discovering, prioritizing, addressing, and monitoring vulnerabilities in systems.
As an ethical hacker, you'll work within this framework to identify and report vulnerabilities, enabling organizations to remediate them before malicious attackers can exploit these weaknesses.
The vulnerability management lifecycle involves 8 steps that you repeat on an ongoing basis to account for the ever-changing environment and new vulnerabilities.
The 8 Steps of Vulnerability Management
The lifecycle is divided into three main phases: Pre-Assessment, Vulnerability Assessment, and Post-Assessment, with the Post-Assessment phase containing more steps than the initial phases.
Pre-Assessment Phase
Step 1: Identify Assets - Organizations discover and catalog all hardware, software, network devices, and digital assets within their environment to create a comprehensive inventory. This complete asset inventory establishes the foundation needed to create an accurate baseline in the next step.
Step 2: Create a Baseline - Security teams document the current state of all identified assets, including configurations, software versions, and security postures to establish a reference point for future assessments. This baseline documentation provides the scope and context necessary for conducting thorough vulnerability scans.
Vulnerability Assessment Phase
Step 3: Vulnerability Scan - Automated scanning tools systematically examine all baseline assets to identify known security weaknesses, misconfigurations, and outdated components across the infrastructure. The raw scanning results then feed into the vulnerability analysis phase where findings are validated and prioritized.
Step 4: Vulnerability Analysis - Security teams analyze and validate scanning results to confirm genuine vulnerabilities, eliminate false positives, and categorize findings by type and severity. This analyzed vulnerability data then flows into risk assessment where each finding is evaluated for its potential business impact.
Post-Assessment Phase
Step 5: Risk Assessment - Organizations evaluate confirmed vulnerabilities based on CVSS scores, exploitability, asset criticality, and potential business impact to create a prioritized remediation plan. This risk-based prioritization guides remediation efforts by identifying which vulnerabilities require immediate attention versus those that can be addressed in future cycles.
Step 6: Remediation - System administrators and security teams implement fixes by applying patches, making configuration changes, or deploying compensating controls to eliminate or mitigate prioritized vulnerabilities. After remediation implementation, the process moves to verification to ensure fixes were successful and didn't introduce new security issues.
Step 7: Verification - Organizations conduct follow-up testing and scanning to confirm that vulnerabilities have been properly remediated and that fixes are functioning as intended without creating additional problems. This verification process leads to continuous monitoring where the security posture is maintained and new threats are detected.
Step 8: Monitoring - Security teams implement ongoing surveillance to detect new vulnerabilities, monitor for emerging threats, and maintain awareness of changes in the environment that could affect security. This continuous monitoring naturally cycles back to asset identification as new systems are deployed, configurations change, and the process repeats to ensure comprehensive security coverage.
The cyclical nature ensures that vulnerability management remains a continuous process rather than a one-time activity, adapting to organizational changes, new threats, and evolving security requirements as the cycle repeats indefinitely.
Vulnerability Research
Vulnerability research is an ongoing task for both network defenders and attackers. Knowing about the latest trends in threats and attack surfaces means that you'll be prepared to protect your system from bad actors.
A good vulnerability research platform is like the seismic sensors placed around the world to detect earthquakes before they begin, so you can alert admins and others on the security team before a major event takes place.
Keep an eye out for two key pieces of information: the weakness being disclosed, as well as the recovery steps to take should your organization be hit. Some of the best vulnerability research platforms include:
CISA Known Exploited Vulnerabilities Catalog: Delivers daily updates on actively exploited vulnerabilities with prioritized remediation guidance for critical threat research.
VulnDB: Provides near real-time vulnerability updates within hours, offering detailed threat context and actionable remediation advice for researchers.
Rapid7’s AttackerKB: Supplies community-driven, near real-time exploit context with rapid updates, focusing on real-world vulnerability and exploit research.
Flexera One (Secunia Research): Offers real-time vulnerability intelligence with granular software build-level details and exploit updates within 24 hours for patch-focused research.
Vulnerability Scanning
Vulnerability scanning is the process of systematically examining systems, netwroks and applications to identify security weaknesses that attackers could potentially exploit. This involves probing various components to uncover flaws in software, misconfigurations, or design issues that create security gaps.
The scanning process generates data about potential security issues, which then requires analysis to determine which findings represent genuine threats versus false positives. Security teams evaluate discovered vulnerabilities by their severity and potential for exploitation to prioritize remediation efforts effectively.
Type of Vulnerability Scanning:
External Scanning - Examines an organizations network from an outside perspective, testing what attackers would see when probing from the internet. This method reveals security gaps visible to external threats trying to breach perimeter defenses.
Internal Scanning - Evaluates systems from within the organization’s netowrk boundaries to identify vulnerabilities that could be exploited by insiders or attackers who have already penetrated initial defenses.
Host-based Scanning - Focuses on individual machines by examining their specific configurations, installed software, user accounts, and system settings to assess how secure each host is against potential compromise.
Network-based Scanning - Analyzes network infrastructure components like routers, switches, and protocols to find weaknesses in how systems communicate and share data across the network.
Application Scanning - Targets web applications and software to detect coding flaws, configuration errors, or outdated components that could allow attackers to manipulate or compromise these programs.
Credentialed Scanning - Performs scans using legitimate login credentials to access systems more thoroughly, revealing vulnerabilities that are only visible when authenticated to target systems.
Non-Credentialed Scanning - Conducts scans without logging into target systems, mimicking how external attackers would probe systems they cannot access, providing an outsider’s perspective on security.
Manual Scanning - Involves security professionals personally examining systems to identify vulnerabilities that automated tools might miss or to validate findings from automated scans.
Automated Scanning - Uses specialized software tools to rapidly scan large numbers of systems simultaneously, efficiently identifying common vulnerabilities across your organization’s infrastructure.
Vulnerability Assessment Tools
Vulnerability assessment tools help for identify, prioritize, and remediate security weaknesses in networks, applications, and systems, serving as a proactive layer in the vulnerability research ecosystem by providing detailed scans and actionable insights before exploitation occurs.
Nessus by Tenable: Delivers comprehensive vulnerability scanning with over 200,000 plugins, including 2025 updates for external attack surface scanning, cloud infrastructure support, and security fixes like CVE-2025-6021 remediation in libxml2 2.13.8, making it ideal for enterprise-wide assessments.
GFI LanGuard: Automates patch management, network auditing, and vulnerability scanning across Windows, Mac, and Linux, with 2025 enhancements in account-based license management, WAN scanning, and real-time monitoring for ransomware threats.
OpenVAS: Offers a free, open-source vulnerability scanner with daily feed updates for authenticated and unauthenticated testing, featuring 2025 improvements in performance tuning for large-scale scans and configurable reports in Greenbone OS 22.04.
Nikto: Functions as a lightweight command-line web server scanner detecting over 7,000 dangerous files and misconfigurations, with 2025 updates including IPv6 support, cookie handling, and enhanced database references for faster, automated web vulnerability checks.
AI-Powered Vulnerability Assessment Tools
AI-powered vulnerability assessment tools automate analysis tasks and provide intelligent insights into security weaknesses. These tools process large amounts of vulnerability data, identify patterns and provide contextual recommendations to help security teams prioritize remediation efforts.
Commonly used tools include:
SmartScanner - A web application security scanner that uses machine learning algorithms to detect vulnerabilities while reducing false positives. The tool adapts its scanning approach based on the target application's behavior and adjusts testing parameters for more accurate results.
Equixly - A vulnerability management platform that combines automated scanning with intelligent risk analysis. It uses natural language processing to analyze vulnerability descriptions and provides contextual threat intelligence to help organizations understand the real-world impact of discovered security issues.
Examples: Use ShellGPT for Vulnerability Scanning
ShellGPT (SGPT) is a command-line tool that uses AI to generate and execute terminal commands based on natural language prompts.
This tool speeds up vulnerability assessment workflows by automatically creating complex scanning scripts, and allowing you to chain together multiple commands to execute complex workflows.
If you haven’t used SGPT yet, check out the guide on that here:
In the three examples below, we’ll show how SGPT can use a variety of tools to conduct vulnerability scanning.
Example #1: Vulnerability Assessment with Nikto
SGPT can generate vulnerability scanning commands using natural language prompts. Here's how to use SGPT for basic web vulnerability scanning:
sgpt -s "Run nikto scan on google.com and save results to output.txt" && open output.txtSGPT interprets this prompt and generates the appropriate Nikto command for web server vulnerability assessment.
Example #2: Vulnerability Scan with Python Scripts
SGPT can create comprehensive Python scripts that combine multiple security tools for automated vulnerability scanning:
sgpt -chat scancode -code "Write a Python script to scan IPs in scan1.txt with Nmap and then check them for vulnerabilities using Nikto" > scan.py && python scan.pyThis SGPT command generates a Python script that performs network discovery with Nmap and chains web vulnerability scanning using Nikto. The python script will be saved to scan.py and run after it’s generated.
Example #3: Vulnerability Scanning with Skipfish
SGPT can orchestrate web application security testing using Skipfish and automate the report viewing process:
sgpt -s "Scan the URL http://testphp.vulnweb.com with Skipfish and open the output index.html in Firefox."This SGPT prompt generates chained commands to execute Skipfish scanning and automatically display the HTML report in a web browser.
Vulnerability Assessment Reporting
In this section, we take the results found in our vulnerability scanning and create reports for key stakeholders in the organization.
The challenge lies in presenting technical findings in a way that resonates with different audiences and their specific responsibilities.
Tailoring Reports to Your Audience
Raw vulnerability scan data overwhelms most stakeholders with technical details they don't need. Each audience requires different information presented in their preferred format and language.
Executive Leadership focuses on business risk, financial impact, and strategic decisions. They need to understand how vulnerabilities affect operations, compliance, and competitive position without getting lost in technical specifications.
IT Management requires operational context, resource requirements, and implementation timelines. They balance security needs against available staff, budget constraints, and business continuity requirements.
Technical Teams need detailed technical information, remediation steps, and priority rankings. They implement the actual fixes and require specific guidance on patches, configurations, and testing procedures.
Writing Effective Executive Summaries
The executive summary determines whether leadership will read the full report or take action on your recommendations. This section should answer key business questions within the first few paragraphs.
Start with the overall security posture using clear risk categories rather than technical scores. Translate CVSS scores into business terms like "immediate attention required" or "acceptable risk with monitoring."
Quantify the scope of exposure by stating how many systems are affected and which business functions could be impacted. Include potential consequences such as service outages, data breaches, or compliance violations.
Provide clear next steps with estimated costs, timelines, and resource requirements. Leadership needs to understand what decisions they must make and when action is required.
Vulnerability Assessment Report Structure
A vulnerability assessment report is a comprehensive document that details the findings of a vulnerability assessment. The report follows a standardized structure to ensure all stakeholders receive the information they need in an organized format.
Executive Summary provides a high-level overview designed for senior leadership and decision-makers who need to understand business impact without technical details. This section includes the assessment scope and objectives, a narrative of testing activities performed, and a summary of key findings with their potential business consequences.
Assessment Overview documents the technical approach and methodology used during the vulnerability assessment process. This section details the specific scanning techniques employed, information about target systems and network segments tested, and the tools and technologies utilized during the assessment.
Findings presents the core technical results discovered during the vulnerability scanning and analysis phases. This section catalogs all scanned hosts and affected assets, categorizes the types of vulnerabilities identified across the infrastructure, and provides detailed technical information about each security weakness discovered.
Risk Assessment analyzes and prioritizes discovered vulnerabilities based on their potential impact to the organization's security posture. Vulnerabilities are classified according to standardized risk levels, with emphasis on those that could lead to system or application compromise.
Recommendations transforms technical findings into actionable guidance for addressing identified security weaknesses. This section prioritizes remediation activities based on risk rankings and business impact, providing specific action plans for implementing fixes to each identified vulnerability.
Appendices and Supporting Information contains detailed technical data that supports the report's findings and conclusions. This section includes raw scan logs, configuration files, screenshots of vulnerability evidence, and references to external resources such as CVE databases or vendor advisories.
Conclusion reinforces the importance of addressing identified vulnerabilities while summarizing the overall security posture of the assessed systems. This section ties together key findings and recommendations, emphasizing critical areas that require immediate attention.
Follow-Up Actions and Timeline establishes clear expectations for remediation activities and ongoing security monitoring. This section provides realistic timelines for addressing vulnerabilities based on their severity and complexity, schedules follow-up assessments to verify remediation effectiveness, and outlines monitoring procedures to detect new vulnerabilities.
Glossary of Terms defines technical terminology used throughout the report to ensure all stakeholders understand the content regardless of their technical background. This section explains vulnerability types, risk classifications, technical acronyms, and security concepts in plain language.
The key to effective vulnerability reporting is remembering that different stakeholders need different information to make informed decisions about security investments and risk management priorities.
Next Step: Phase 4 - Gaining Access
In this guide, you've learned how to identify vulnerabilities through systematic scanning, analyze security weaknesses using various assessment tools, and leverage AI-powered solutions to streamline vulnerability discovery workflows.
You now understand the vulnerability management lifecycle, can classify different types of security flaws, and know how to use both traditional and modern tools for comprehensive security assessments.
This completes Phase 2 of Ethical Hacking, preparing us for exploitation and Phase 3 'Gaining Access' based on the vulnerabilities discovered in this phase.
This is where we transition from information collection into actively exploiting identified weaknesses and seeking to gain initial access on target systems.
Stay tuned for the next guide!